网络安全如何影响seo
In today’s digital world, SEO is now as important as any work performed by sales or engineering departments.
在当今的数字世界中,SEO与销售或工程部门执行的任何工作一样重要。
Almost all of today’s companies have onsite SEO interns, or a remote SEO team assembled within their permanent staff. That’s because the higher you rank in Google, the more chances your products, services and ‘content’ will be discovered by visitors. With discovery comes traffic, and with traffic often comes new customers and sales.
如今,几乎所有公司都在本地SEO实习生,或在其常任员工内部聚集了一个远程SEO团队。 这是因为您在Google中的排名越高,访问者发现您的产品,服务和“内容”的机会就越大。 发现带来流量,而流量往往带来新客户和销售量。
Some companies have big SEO teams that take care of all involved SEO responsibilities such as keyword research, content strategy, link building, negative SEO, penalization analysis and recovery.
一些公司拥有庞大的SEO团队,负责所有与SEO有关的职责,例如关键字研究,内容策略,链接建立,否定SEO,处罚分析和恢复。
If you want to Gain In-depth Knowledge on Cyber Security, please go through this link Cyber Security Online Training
如果您想获得有关网络安全的深入知识,请通过此链接进行网络安全在线培训
But even while digital companies prioritize their investment in SEO, they tend to lose sight of something really important: cybersecurity.
但是,即使数字公司优先考虑在SEO上进行投资,他们也往往会忽略一些真正重要的东西:网络安全。
In this article, we’ll explore how cybersecurity affects SEO, and why the digital security of your website, apps, and servers should be always part of your business plan.
在本文中,我们将探讨网络安全如何影响SEO,以及为什么网站,应用程序和服务器的数字安全性应始终作为业务计划的一部分。
被黑客入侵会怎样? (What happens when you get hacked?)
There are a lot of scenarios where you may be affected by a security breach. Some include hacking the database you’re using, others the DNS and HTTP servers, and others involve direct root compromise over SSH.
在许多情况下,您可能会受到安全漏洞的影响。 其中一些攻击包括入侵您正在使用的数据库,其他攻击包括DNS和HTTP服务器,其他攻击包括通过SSH直接破坏根目录。
In all these types of hacks, your corporate website may be directly hit. That means crackers can:
在所有这些类型的黑客攻击中,您的公司网站可能会受到直接攻击。 这意味着饼干可以:
- Redirect your traffic to 3rd party servers将您的流量重定向到第三方服务器
- Cause massive 404 errors across your website在您的网站上造成大量404错误
- Generate internal server errors (known as error 50X)生成内部服务器错误(称为错误50X)
- Infect your website with malicious code, spreading infections to all your visitors用恶意代码感染您的网站,将感染传播给所有访问者
- Cause a data breach, compromising credit cards and sensitive personal information from your customers造成数据泄露,损害客户的信用卡和敏感个人信息
- Setup phishing domains or perform a subdomain takeover attack in order to trick visitors设置网络钓鱼域或执行子域接管攻击以欺骗访客
Something to keep in mind: not only can hacks be performed against apps, services and servers, they can also target domain names. The most common attack against domains is ‘domain hijacking’, which basically consists of taking control over your domain name at registrar level.
注意事项:不仅可以针对应用程序,服务和服务器进行黑客攻击,而且还可以针对域名。 针对域名的最常见攻击是“域名劫持”,它基本上包括在注册服务商级别上控制您的域名。
The consequences of a security breach can be huge. Many companies don’t even recover after a sizable security compromise, and have to close their businesses.
安全漏洞的后果可能是巨大的。 许多公司甚至在遭受重大安全威胁后甚至无法恢复,因此不得不关闭其业务。
These consequences may include:
这些后果可能包括:
Website downtime: After a hacker attack, downtime is one of the most common consequences, especially when a direct server compromise or massive DDoS is involved.
网站停机 :遭受黑客攻击后,停机是最常见的后果之一,尤其是在涉及直接服务器入侵或大规模DDoS时。
- This not only affects your own access to your platform, but also your customers’ access to your services and data.这不仅影响您自己对平台的访问,还影响客户对您的服务和数据的访问。
Website-related file loss: Once they’ve gained access to your SSH or FTP server, malicious attackers can modify or delete your website files and database data, causing massive errors across your online platforms.
与网站相关的文件丢失 :恶意攻击者一旦获得对您的SSH或FTP服务器的访问权限,便可以修改或删除您的网站文件和数据库数据,从而在整个在线平台上造成大量错误。
Customer data loss: A lot of companies save personal and sensitive data from their customers, such as names, addresses, telephone numbers, emails, passwords, bank account and credit card numbers, and more. This is one of the top areas crackers may plunder when compromising your databases.
客户数据丢失 :许多公司保存其客户的个人和敏感数据,例如姓名,地址,电话号码,电子邮件,密码,银行帐户和信用卡号,等等。 这是黑客在破坏数据库时可能掠夺的最重要区域之一。
- The consequences of this type of data breach — for both company and customers — can be devastating, depending on how much information the attackers obtain.这种类型的数据泄露对公司和客户的后果可能是毁灭性的,具体取决于攻击者获得的信息量。
Reputation damage: Apart from technical consequences, the worst thing that can happen after a cybersecurity breach may be how much your reputation is damaged after the incident. This includes losing trust from your customers, investors, financial institutions that work with you, and others.
声誉受损 :除了技术后果外,在网络安全漏洞之后可能发生的最糟糕的事情可能是事件发生后您的声誉受损了多少。 这包括失去客户,投资者,与您合作的金融机构以及其他人的信任。
- Your online brand can become a negative company on any given day, something that is truly difficult to reverse. A lot of your competition waits for you to make a mistake — so they can take advantage of it.您的在线品牌在任何一天都可能成为负面公司,这确实很难逆转。 您的很多比赛都在等待您犯错,因此他们可以利用它。
网络安全如何影响您网站的SEO排名 (How Cybersecurity Affects Your Site’s SEO Rankings)
404错误 (404 Errors)
“Error 404 — Content not found” is one of the most commonly seen error messages on the Internet. It basically means that the content that used to be there wasn’t found; therefore, it’s missing. You know it when you visit the URL, but web crawlers such as Google also notice this kind of error, and that’s when the problems begin.
“错误404-找不到内容”是Internet上最常见的错误消息之一。 基本上,这意味着找不到以前存在的内容; 因此,它不见了。 您在访问URL时就知道了,但是Google之类的网络抓取工具也会注意到这种错误,那就是问题开始的时候。
While Google is a bit permissive with 404 errors, they can become a major SEO stumbling block when they’re attached to your site for a long time.
尽管Google允许404错误,但如果将它们长时间附加到您的网站,它们可能会成为主要的SEO绊脚石。
Crackers often delete web files and pages, which leads to isolated or even massive 404 errors across your website.
破解者经常删除Web文件和页面,这会导致整个网站出现孤立甚至大量的404错误。
停机时间 (Downtime)
Downtime is one of the worst nightmares of any website owner, whether of a small website, ecommerce store, or multi-million dollar organization. We never want our sites to be down.
停机对于任何网站所有者来说都是最糟糕的噩梦之一,无论是小型网站,电子商务商店还是价值数百万美元的组织。 我们从不希望我们的网站瘫痪。
Because downtime means that your content, products and services are no longer online for your new or recurring customers, this can be a great opportunity for your competition to offer whatever you’re missing.
由于停机时间意味着您的内容,产品和服务不再对新客户或老客户在线,因此这可能是您竞争中提供所缺少产品的绝佳机会。
From the ‘enterprise’ point of view it’s clear that losing customers or new sales during downtime is not good at all, sometimes even tragic.. Depending on the type of attack you recieve, downtime can last hours, days or even weeks in the worst of scenarios.
从“企业”的角度来看,很明显停机期间失去客户或新销售根本不好,有时甚至是悲惨的。根据您所接受的攻击类型,停机可能持续数小时,数天甚至数周,甚至是最坏的情况。场景。
When it comes to SEO, having your site online and running well and ready for web-crawlers is always a goal. For Googlebot to come crawling to your site only to find every single one of your pages down is a critical issue. It may return later — Google won’t drop your rankings instantly, and will try re-crawling on the same day to see if the site is back up — but hours or days of downtime can be serious. It determines the level of SERP (Search Engine Results Page) dropdown your site will experience.
当涉及到SEO时,使您的网站在线运行并为网络爬虫做好准备一直是一个目标。 要让Googlebot爬网到您的网站而仅查找您的每一个页面,都是一个关键问题。 它可能会在以后返回-Google不会立即降低您的排名,而是会在同一天尝试重新爬网以查看网站是否已备份-但是停机数小时或数天可能会很严重。 它确定您的网站将遇到的SERP(搜索引擎结果页)下拉菜单的级别。
That means that Google will not drop you from its index, but it may move your main keywords to lower levels while waiting for you to recover from downtime. Matt Cuts once said that one day of downtime is not a big deal, but after a few years tracking SERPs on different niches and languages, we know from experience that after 8 hours of downtime, SERPs may drop a site by about 35%, depending on how solid the keywords are. And results usually won’t come back until Google performs a new SERP update.
这意味着Google不会将您从其索引中删除,但会在等待您从宕机中恢复过来的同时将您的主要关键字移到较低的级别。 Matt Cuts曾经说过,一天的停机时间没什么大不了的,但是经过几年跟踪不同语言和语言的SERP的经验之后,我们从经验中知道,停机八小时后,SERP可能会使站点下降约35%,具体取决于关键字的牢固程度。 在Google执行新的SERP更新之前,结果通常不会返回。
To Become a Certified Hacker, Go Through Ethical Hacking Training
要成为认证的黑客,请经过道德黑客培训
SEO处罚 (SEO Penalties)
Hacked websites are dangerous, and Google wants to prevent people from getting damaged by visiting suspicious websites.
被黑的网站是危险的,Google希望防止人们通过访问可疑的网站而受到损害。
Long term SEO penalizations after hacking are a cruel reality you may have to face if part or all of your online presence gets compromised. Let’s imagine for a moment that a malicious actor gets into your servers, and starts distributing malware, virus or, unwanted downloads. Having been screwed up this much, your site will be less desirable to visit… and Google’s keeping track of this.
如果您的部分或全部在线业务受到损害,那么黑客入侵后长期的SEO处罚是一个残酷的现实。 让我们想象一下,恶意参与者进入您的服务器,并开始分发恶意软件,病毒或有害下载。 搞砸了这么多,您的网站将不受欢迎访问……而Google会跟踪这一情况。
浏览器列入黑名单 (Browser Blacklisting)
Sometimes, attackers will inject your pages with HTML, JS or PHP redirect codes, causing them to be permanently redirected to malicious phishing URLs, or to sites that spread virus or malware to your visitors.
有时,攻击者会向您的页面注入HTML,JS或PHP重定向代码,从而将其永久重定向到恶意网络钓鱼URL,或重定向到向您的访问者传播病毒或恶意软件的网站。
This will ultimately make you manually or automatically blacklisted, sometimes without you even noticing the hack until it’s too late.
最终,这将最终使您手动或自动将其列入黑名单,有时甚至没有注意到黑客入侵,直到为时已晚。
SafeBrowsing is one of the mechanisms that helps browsers to identify suspicious content across the Internet, and if you are infected with malicious code or redirected to a 3rd party non-safe website, you’ll probably end up on this blocking list that prevents your visitors from browsing your site normally.
安全浏览是一种机制,可帮助浏览器识别Internet上的可疑内容,并且如果您感染了恶意代码或重定向到第三者非安全网站,则您可能最终会进入此阻止列表,从而阻止访问者正常浏览您的网站。
您如何才能提高网络安全性并避免SEO问题? (What can you do to increase cybersecurity and avoid SEO issues?)
审核您的网站安全 (Audit your website security)
Scan your site with vulnerability scanners: In order to harden your app, you first have to know how solid your website is in terms of vulnerabilities and critical security bugs. Your best bet is to use an online vulnerability scanning tool.
使用漏洞扫描程序扫描您的网站 :为了加强您的应用程序,您首先必须知道网站在漏洞和严重安全漏洞方面的可靠性。 最好的选择是使用在线漏洞扫描工具。
- Once you have the results, you can get to work on hardening your website.获得结果后,就可以着手加固您的网站。
Scan your code with malware-scanning tools: After performing the vulnerability scan, there’s another thing that’s mandatory for auditing your website’s security. That’s running a full in-depth scan throughout the code.
使用恶意软件扫描工具扫描您的代码 :执行漏洞扫描后,审核网站的安全性还有另一件事是必须的。 这将对整个代码进行全面的深入扫描。
- You can use online utilities for this, or a server-side malware scanner, which is often the most reliable method. Excellent tools such as CXS, Maldet and ClamAV can help.您可以为此使用在线实用程序或服务器端恶意软件扫描程序,这通常是最可靠的方法。 出色的工具,例如CXS,Maldet和ClamAV可以提供帮助。
- You can also check your site with free online tools like Sucuri or VirusTotal.您也可以使用免费的在线工具(例如Sucuri或VirusTotal)检查您的网站。
Harden your website security: Once you’ve found vulnerabilities or malicious code in your apps, it’s time to take action. This is essential, whether you build your website from scratch using 3rd party libraries or you write your own. Our best advice is to always adopt and follow a defensive coding approach.
加强网站安全性 :一旦发现应用中存在漏洞或恶意代码,就该采取行动了。 无论您是使用第三方库从头开始构建网站还是编写自己的网站,这都是至关重要的。 我们最好的建议是始终采用并遵循防御性编码方法。
- And if you’re using a CMS, there are thousands of hardening guides for every CMS on earth, whether you’re using Drupal, Joomla or Wordpress. The last is one of the most popular targets for attackers worldwide.而且,如果您使用的是CMS,则无论您使用的是Drupal,Joomla还是Wordpress,都有数千种针对每个CMS的强化指南。 最后一个是全世界攻击者最受欢迎的目标之一。
- Wordpress powers a huge portion of the websites currently online, and there’s a big chance that your entire website infrastructure, or part of it, is built based on this CMS. If you’re using it, increasing Wordpress security should be an essential part of your cybersecurity plans.Wordpress为当前在线的网站提供了强大的支持,您的整个网站基础架构或其中的一部分很有可能是基于此CMS构建的。 如果您正在使用它,则提高Wordpress安全性应该是网络安全计划的重要组成部分。
审核服务器和网络安全 (Audit your server and network security)
Update your system packages: Whether you’re using Windows, Linux or Unix, a golden rule for all operating systems is to keep your system packages updated. This will protect against most critical security bugs on both kernel and general OS packages.
更新系统软件包 :无论您使用的是Windows,Linux还是Unix,所有操作系统的一个黄金法则就是保持系统软件包的更新。 这将防止内核和常规OS软件包上的大多数关键安全错误。
Use a system firewall: Generally, the second best advice we can give you to increase your server security is to use a firewall. A firewall is the shield that prevents unauthorized access to and from the Internet, a private network, or both.
使用系统防火墙 :通常,我们可以为您提供提高服务器安全性的第二个最佳建议是使用防火墙。 防火墙是一种防护罩,可防止未经授权访问Internet,专用网络或两者。
- Whether you’re using a hardware-based firewall or a software firewall, it will help you monitor network packets, filtering all the things that may hurt your box and allow only what you really want inside your network. If you own a VPS, cloud server or bare-metal server, installing and properly configuring a system firewall is one of the most basic of things for you to do.无论您使用的是基于硬件的防火墙还是软件防火墙,它都将帮助您监视网络数据包,过滤可能伤害您设备的所有内容,并仅允许您在网络中真正想要的东西。 如果您拥有VPS,云服务器或裸机服务器,则安装和正确配置系统防火墙是您要做的最基本的事情之一。
Use an intrusion detection system (IDS): The main purpose of this kind of defensive software is to prevent and detect intrusion attempts to your network or servers.
使用入侵检测系统(IDS) :这种防御软件的主要目的是防止和检测对您的网络或服务器的入侵尝试。
- While it works by detecting malicious patterns that could potentially intrude upon your systems, it also works by blocking all such attempts. An IDS uses one or more attack signature databases, which store common patterns for several types of intrusion attacks. Once it detects a suspicious event, it will block it and alert system administrators to it.虽然它通过检测可能会侵入您系统的恶意模式来起作用,但它也可以通过阻止所有此类尝试来起作用。 IDS使用一个或多个攻击签名数据库,该数据库存储几种类型的入侵攻击的通用模式。 一旦检测到可疑事件,它将阻止该事件并提醒系统管理员。
Use a file integrity monitoring (FIM) daemon: This type of defensive software runs on backend servers and lets you monitor, control and detect changes in files that may be part of a cybersecurity attack.
使用文件完整性监视(FIM)守护程序 :这种防御软件在后端服务器上运行,使您可以监视,控制和检测文件更改,这些更改可能是网络安全攻击的一部分。
- Once it’s installed, this software will create a database of the current state of the files as a start point, and begin monitoring any changes made to them, as well as who changed them and when, and provide the best suggestions toward restoring any file if found modified by a malicious unauthorized user. When file-upload defensive policies fail, FIM tools are the second layer that will help you detect malicious code, URL redirections, backdoors, trojans and more.安装完成后,该软件将创建一个以文件当前状态为起点的数据库,并开始监视对文件所做的任何更改以及更改的人和时间,并提供有关还原任何文件的最佳建议(如果有)被恶意未经授权的用户修改。 当文件上传防御策略失败时,FIM工具是第二层,可帮助您检测恶意代码,URL重定向,后门,特洛伊木马等。
Check system service logs: Since the early days of system administration, checking system logs is a must for network and system security.
检查系统服务日志 :从系统管理的早期开始,检查系统日志对于网络和系统安全是必不可少的。
When dealing with an attack, system and service logs are often the most overlooked source of data. In truth, they can share valuable information to help detect attack origins, vulnerabilities, impact over modified files, databases and much more.
在处理攻击时,系统日志和服务日志通常是最容易被忽视的数据源。 实际上,他们可以共享有价值的信息,以帮助检测攻击源,漏洞,对修改后的文件,数据库的影响等等。
- They’re also a great way to learn how the bad guys try to get into your box, as seen in our article about the Top 20 Honeypots for Detecting Network Threats.从我们关于“检测网络威胁的前20个蜜罐”的文章中可以看出,它们也是了解坏蛋如何试图进入您的机器的好方法。
Install a malware and virus scanner: As we’ve told you before, scan your files, over and over. Most of the top-ranked scanners, for performance and tweak reasons, are the ones installed on the server side. Having a malware scanner running scheduled scans and reporting day-today will help you detect infections quickly. If you want to stay one step ahead, you can also configure the scanner to inspect any file uploads to the server, and quarantine them before they become a real threat.
安装恶意软件和病毒扫描程序 :正如我们之前告诉您的那样,一遍又一遍地扫描您的文件。 出于性能和调整的原因,大多数排名靠前的扫描仪都是安装在服务器端的扫描仪。 使用恶意软件扫描程序运行计划的扫描并每天进行报告,将帮助您快速检测到感染。 如果您想保持领先地位,还可以将扫描仪配置为检查任何上传到服务器的文件,并在它们成为真正威胁之前对其进行隔离。
审核您的攻击面 (Audit your attack surface area)
Most people only look into the website and server-side areas when hardening their cybersecurity. They tend to overlook what’s called the attack surface area, the third layer missing on most hardening processes.
大多数人只会在加强网络安全时才关注网站和服务器端区域。 他们往往会忽略所谓的“攻击表面积”,这是大多数硬化过程中缺少的第三层。
When it comes to analyzing your attack surface area, we can include several tasks that will yield critical and normally unseen data from all your online assets.
在分析您的攻击范围时,我们可以包括几个任务,这些任务将从您所有的在线资产中生成关键的,通常是看不见的数据。
For this purpose, we will use our Attack Surface Reduction tool, which will give you instant access to this sensitive information within seconds.
为此,我们将使用“减少攻击面”工具,该工具可让您在几秒钟内立即访问此敏感信息。
While analyzing the attack surface of your company, there are a few things to keep in mind:
在分析公司的攻击面时,请牢记以下几点:
Find subdomains: The art of finding subdomains is something we’ve mastered over the years, and it’s now included in all our products.
查找子域 :多年来,我们已经掌握了查找子域的技巧,现在它已包含在所有产品中。
- From this interface, you’ll be able to find all the subdomains from any of your apex domain names, helping you discover old and unused subdomains created for dev projects, tests, temporary apps, old name servers, and much more.通过该界面,您可以从任何一个顶点域名中找到所有子域,从而帮助您发现为开发项目,测试,临时应用,旧名称服务器等创建的旧的和未使用的子域。
- This type of intelligence data can help you create a full subdomain map and analyze and delete the ones you don’t need. This will allow you to reduce your attack surface and prevent popular DNS attacks that involve stale DNS records.这种类型的情报数据可以帮助您创建完整的子域地图,并分析和删除不需要的子域地图。 这将使您减少攻击面并防止涉及陈旧DNS记录的流行DNS攻击。
Perform a full domain enumeration and IP block mapping: Creating a virtual map of all your online assets is one of the most worthwhile things you can do for all your domain names. This gives you the visibility you need to explore records one-by-one from the DNS server at the terminal.
执行完整的域枚举和IP块映射 :创建所有在线资产的虚拟映射是您可以对所有域名进行的最有价值的操作之一。 这样一来,您就可以从终端的DNS服务器一张一张地浏览记录,从而获得所需的可见性。
- Our Attack Surface Reduction tool offers an effective solution, letting you access all your domains and IPs in mere seconds:我们的减少攻击面工具提供了有效的解决方案,让您在短短几秒钟内即可访问所有域和IP:

- By combining this with a full IP block lookup, we will not only see the main trees but the entire forest, ordered by IP with full details about geolocation, ASN, IP usage, reputation, web hosting provider, rDNS and forward DNS:通过将其与完整的IP块查找结合起来,我们不仅会看到主要的树,而且还会看到整个林,它们按IP排序,并提供有关地理位置,ASN,IP使用,信誉,Web托管提供商,rDNS和转发DNS的完整详细信息:
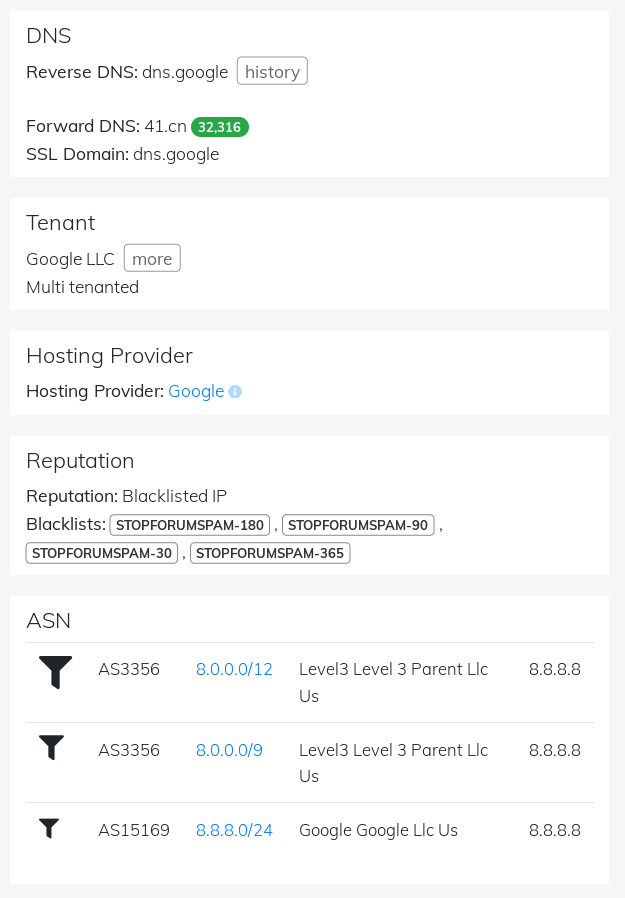
Perform a massive open port scan: Open ports are always important, and while they’re not a direct sign of vulnerability, unpatched or vulnerable services running on those ports may become a silent threat sooner or later. ASR offers you the ability to discover exposed open ports and services, giving you access to the big picture across your entire IP infrastructure, as you can see below!
执行大规模的开放端口扫描 :开放端口始终很重要,尽管它们并不是漏洞的直接迹象,但迟早在这些端口上运行的未打补丁或易受攻击的服务可能会成为无声的威胁。 ASR使您能够发现暴露的开放端口和服务,从而使您能够访问整个IP基础架构的全貌,如下所示!

- Not only does our technology give you the port number and service name, it checks for the remote software version as well. And if this isn’t enough for you, we also offer full historical TCP and UDP port history, as shown in the following screenshot:我们的技术不仅会为您提供端口号和服务名称,还会检查远程软件版本。 如果这还不够,我们还提供完整的历史TCP和UDP端口历史记录,如以下屏幕截图所示:

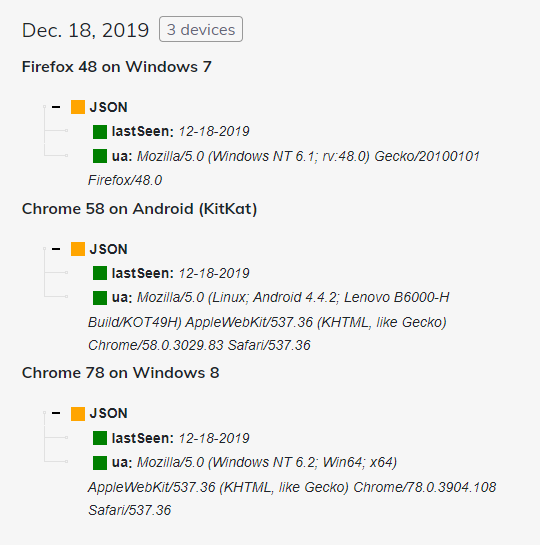
User-agent inspection: What are the devices related to this IP address? To answer this question, we keep a record of all the connected devices that have interacted with this host. The Devices sub-tab lets you jump directly into all this data, and filter it by user-agent or date.
用户代理检查 :与该IP地址相关的设备是什么? 为了回答这个问题,我们保留了与此主机交互的所有已连接设备的记录。 通过“设备”子选项卡,您可以直接跳至所有这些数据,并按用户代理或日期对其进行过滤。
- Once you click on any device, you’ll get all the information related to that device:单击任何设备后,您将获得与该设备有关的所有信息:
Analyze your SSL certificates: SSL certificates play a critical role in cybersecurity, and something we notice every day is the huge amount of expired SSL certificates. People purchase massive amounts of SSL certificates. They also tend to forget to renew a lot of them, leaving critical areas unencrypted. With ASR, you get the chance to obtain full SSL data including SSL scope, locality name, state/province, organization name, common name, country and organizational unit name:
分析您的SSL证书 :SSL证书在网络安全中起着至关重要的作用,我们每天都注意到大量过期的SSL证书。 人们购买了大量的SSL证书。 他们也往往忘记更新其中的许多内容,而使关键区域保持未加密状态。 使用ASR,您有机会获得完整的SSL数据,包括SSL范围,位置名称,州/省,组织名称,通用名称,国家和组织单位名称:

- You’ll also get the exact expiration date, which is critical for keeping your website information encrypted at all times.您还将获得确切的到期日期,这对于始终保持网站信息的加密至关重要。
- And that’s not all. We offer you the full SSL by domain data, so you can easily know how many SSL certificates you have for each domain name at all times.不仅如此。 我们为您提供按域的完整SSL数据,因此您可以随时轻松地了解每个域名拥有多少SSL证书。
To get in-depth knowledge on Cyber Security, Enroll for live free demo on Cyber Security Training
要获得有关网络安全的深入知识,请注册免费进行有关网络安全培训的实时演示
结论 (Conclusion)
Businesses rely on implementing great SEO strategies to attract traffic and generate profits.
企业依靠实施出色的SEO策略来吸引流量并产生利润。
For Google and other search engines, filling your site with great content is by no means your only priority; you’ll also want to offer the best user experience possible. Not only does that include responsive design with close attention to buttons, text, layouts and font sizes and styles, it also includes the security of your site.
对于Google和其他搜索引擎而言,让您的网站内容丰富绝不是您的首要任务; 您还希望提供最佳的用户体验。 这不仅包括响应式设计,并且特别关注按钮,文本,布局以及字体大小和样式,还包括网站的安全性。
翻译自: https://medium.com/@Priya.Reddy/how-cyber-security-affects-seo-d3a9d538fcc5
http://www.taodudu.cc/news/show-1987121.html
相关文章:
- Nikto漏洞扫描工具简介
- 一级必杀,防不胜防的漏洞,WEB安全基础入门—文件上传漏洞
- qt添加控制台语句_向控制台语句添加样式
- chrome升级后无高级-断续访问
- Suricata默认规则集相关
- Java反序列化漏洞之殇
- [网络通信协议]websocket
- web应用程序安全性测试_立即提高Web应用安全性的6种方法
- Tracking Attackers: Honeypot, Part 1 (Honeyd)
- Chaff Bugs: Deterring Attackers by Making Software Buggier
- Your connection is not private Attackers might be trying to steal your information from nemertes.lis
- 【NDSS 2021】On the Insecurity of SMS One-Time Password Messages against Local Attackers 论文笔记
- 11 Steps Attackers Took to Crack Target
- 论文阅读笔记——Adversarial Attack on Attackers Post-Process to
- 数字化时代,需要数据思维!
- Python 可轻松获取天气数据、可视化分析
- 2020年中国标准化发展现状分析,数字化为标准化领域带来新挑战「图」
- 华为数据之道(5):华为数字化转型的目标、蓝图和愿景
- 数据化、信息化、数字化和智能化之间联系和区别解析(建设收藏)
- 《企业架构的数字化转型》10000字有感
- 微软独特的数字化转型思想和方法论
- 从看《长津湖》想到的数字化转型
- 数据化、信息化、数字化和智能化之间联系和区别解析
- CDA I级学习 - EDIT数字化模型
- 化学实验中计算机技术的应用,数字化实验在化学教学中的应用
- 以智能制造推动企业数字化转型的方法、路径和举措
- python天气可视化分析报告_Python爬取天气数据及可视化分析
- 电商数字化色彩系统的探索
- 2021爱分析·药企数字化趋势报告
- 关于分行数字化转型工作的几点思考
网络安全如何影响seo相关推荐
- 二级域名是否可以随意设定_新老域名是否影响SEO优化收录排名?企业需要多域名做网站吗?...
(文/守护袁昆)各互联网平台想免费做营销推广变得比较困难,而大多数中小企业又没什么资金方面的营销预算,所以付费推广广告也没法做.建立自己的企业官网貌似是不错的方式. 传统企业在互联网上玩了一圈,发现还 ...
- 计算机病毒对网络有什么影响,小议计算机病毒对网络安全的影响
小议计算机病毒对网络安全的影响当谈到计算机病毒,人们会有和对生物病毒一样的反应----"谈毒色变"!因为计算机病毒带来的危害和生物病毒一样令人恐惧,一样令人手无足措! 虽然此病毒非 ...
- 网站服务器和seo,网站更换服务器而不影响SEO的两个关键因素【实战经验分享】...
本文信息本文由方法SEO顾问发表于2015-03-1700:00:48,共 1726 字,转载请注明:网站更换服务器而不影响SEO的两个关键因素[实战经验分享]_[方法SEO顾问],如果我网站的文章对 ...
- 影响 SEO 的排名优化的因素
我们在做网站SEO运营的时候,经常会遇到没有排名的情况.即使我们每天保持原创内容的更新和发布,也没有用.这时候就要马上检查网站存在哪些问题,及时解决,让我们的日常努力尽快盈利.以下因素按米贸搜排序,影 ...
- 网站迁移是否会影响 SEO
无论您是否意识到,网站迁移都会影响 SEO.每当您对网站进行重大更改时,都会使您的 SEO 面临风险.许多网络主机提供免费的迁移服务,或者您可以选择使用您的开发人员自行迁移.尽管如此,尽管迁移是免费的 ...
- 修改html会影响seo,网站修改css影响seo吗?
改动不大的话,不会影响:慢慢改,别一下子改动太大了,大幅度的修改.CSS样式在SEO中最重要的作用,就是平衡链接在内容页面与HTML的展示位置,它严重影响蜘蛛抓取的频率,以及传递的权重. css对se ...
- 网络安全ai能力建设_人工智能对网络安全的影响
网络安全ai能力建设 Artificial intelligence (AI) and machine learning (ML) have shown significant progress in ...
- 影响SEO网站文章收录的因素有哪些?
众所周知,网站文章的收录良好不仅对网站排名有帮助还非常利于吸引更多的用户浏览.但有些时候优化人员也每天都在更新高质量文章,但搜索引擎总是不收录,也引得优化人员百思不得其解,那么接下来就带大家了解一下网 ...
- 大量html乱码seo,HTTPS改造之后网页错位乱码,影响SEO和正常访问,应该这样改
有一些朋友可能不太知道https改造怎么做,就学着网站的步骤进行,实际操作过程中可能会遇到很多问题.比如说有的会出现网页错位.页面乱码.后台功能无法使用的情况. 昨天我们就有一个客户他自己做了http ...
- php签入html出来的影响seo吗_搜索引擎优化_SEO必备6大技能+SEO误区讲解!
大家好,我是逆冬,今天来分享一下实战SEO需要掌握什么样的技能以及SEO知识误区,本篇文章仅代表逆冬本人几年的经验.不见得适合每一个SEOer!下面就让逆冬本人来分析一下实战型SEO到底需要掌握什么技 ...
最新文章
- Arduino可穿戴教程之第一个程序——Blink(一)
- OpenStack高可用核心架构分析
- 毕业后的五年拉开大家差距的原因在哪里
- Android程序员面试必备的知识点,附答案
- php 公交 查询系统,php定做单城市公交路线查询系统
- uboot移植——使用三星官方的uboot进行移植
- Android之launchMode总结
- STM103单片机串口输出函数printf重映射
- vc++树状控件(TreeCtrl)用法
- c# zxing条形码设置密度_C# 中 ZXing.Net 怎样突破 条形码 多识别 数量限制
- 热工检测系统设计知识点总结
- 中交一公局二公司全面推进章管家 印章智慧管理转型在即
- jmeter +ant实现接口的自动生成测试报告
- 经典算法之左边界二分查找法(俗称左边界二分搜索法)
- 【赚钱应跟Apple,做大不忘Google】移动开发时代的开发者选择
- 论文笔记-对话系统综述
- 湘潭大学c语言作业系统学生端,作业收发系统学生端使用说明
- 中高级iOS大厂面试宝典,进厂率80%,金三银四将是你的新起点
- 小说《肖申克的救赎》的优秀读后感2600字
- [附源码]Python计算机毕业设计电子病历系统
热门文章
- java batik 乱码_Batik渲染png图片异常的bug修复
- JVM内存模型和java内存模型
- 解决pom文件无法导入ojdbc驱动的问题
- Sql Server数据库查询去重数据,并保留最新的数据,以及删除重复数据
- 即时语音提示软件php,InsTalk即时语音提示校对软件(语音识别和语音合成软件)
- Hownet在NLP领域内是什么样的地位?
- 计算机丢失gdiplus.dll怎么办,win7系统丢失gdiplus.dll报错的解决办法
- ERP系统之比较——SAP、Oracle、BAAN、JDE、SSA
- java项目-基于SSM实现物流信息管理系统
- Linux下搭建FastDFS文件服务器(亲测成功)
