在真正的短信网络钓鱼攻击内部
SMS based phishing attacks (Smishing) are a real threat that we see every day. To help you spot them in future, this is how they work.
基于SMS的网络钓鱼攻击(Smishing)是我们每天看到的真正威胁。 为了帮助您将来发现它们,这就是它们的工作方式。
网上诱骗/网络钓鱼攻击 (A Phishing/Smishing Attack In Action)
At 17:52 pm today I received a text message from my mobile phone network, ‘EE’. I picked up the message at 18:08. This is what it said:
今天下午17:52,我从手机网络“ EE”收到一条短信。 我在18:08收到消息。 它是这样说的:
[EE]:We were unable to process your latest bill. In order to avoid fees, update your billing information via: https://ee.uk.billing45.com/?ee=2
[EE]:我们无法处理您的最新帐单。 为了避免收费,请通过以下网址更新您的结算信息:https://ee.uk.billing45.com/?ee=2
(It’s not a real link. I’ve made it unclickable. Please don’t visit it…)
(这不是真正的链接。我使其无法点击。请不要访问它……)
So that’s weird. Yes, I’m an EE customer and they send me text messages all the time. But that domain looks strange. Let’s check it out. What happens when I visit the link with Chrome on my Android phone?
所以这很奇怪。 是的,我是EE客户,他们一直向我发送短信。 但是那个域名看起来很奇怪。 让我们来看看。 当我在Android手机上访问带有Chrome浏览器的链接时会怎样?

It works! And it looks pretty real. That’s almost exactly what I see whenever I visit the EE site on my Android phone. However, four things stand out immediately:
有用! 而且看起来很真实。 这几乎就是我在Android手机上访问EE网站时所看到的。 但是,有四件事立即脱颖而出:
- The domain is not a domain I trust. I’ve no idea who billing45.com are.该域不是我信任的域。 我不知道谁是billing45.com。
- The copyright statement is 2019. It’s over a month into 2020 now. Either EE generates this value dynamically or someone will have updated it by now.版权声明为2019。到2020年已经过去了一个多月。 EE会动态生成此值,或者有人会立即更新它。
- Most of the links in the footer do nothing. Some of them actually take you to real EE sites. The link to newsroom actually works…页脚中的大多数链接都不起作用。 他们中的一些实际上将您带到了真正的EE网站。 与新闻编辑室的链接实际上有效……
- It’s got the secure padlock we’ve all been trained to look for. Looks legit, right? Maybe not.它具有我们都经过训练才能寻找的安全挂锁。 看起来合法,对吧? 也许不会。
When I open the site on my laptop however, Chrome gives me a big red warning message:
但是,当我在笔记本电脑上打开网站时,Chrome会给我一个红色的大警告消息:

What concerns me here is that I use Chrome on both my Android smartphone and my laptop and yet mobile Chrome did nothing to protect me. @Google, why do you protect desktop users but not mobile?
这里让我担心的是,我在Android智能手机和笔记本电脑上都使用了Chrome,但是移动版Chrome并没有保护我。 @Google,为什么保护桌面用户而不保护移动用户?
Undeterred, I proceed to update my billing details because I don’t want my phone to be cut off and I can’t afford to pay any late fees. I immediately and successfully login with a made-up username and password. Had I chosen to register as a new customer I’m sure that would have worked too.
话虽如此,我还是继续更新我的帐单明细,因为我不希望手机被切断并且我负担不起任何滞纳金。 我立即使用虚构的用户名和密码成功登录。 如果我选择注册为新客户,我肯定那也可以。

Now that I’m logged in I can update my billing information. Except, the top right of the page is still asking me to ‘Log in’… I thought I just did that…
现在,我已经登录,可以更新我的账单信息。 除此以外,页面右上角仍要求我“登录” ...我以为我刚刚做了...
Anyway, all of these things look like perfectly reasonable pieces of information to ask for. I complete the form with more made-up details. Fortunately, I didn’t get any of those annoying, red, data validation errors on any of the input fields! How refreshing. Onwards to the next page.
无论如何,所有这些事情看起来都是需要提供的完全合理的信息。 我用更多虚构的细节来填写表格。 幸运的是,在任何输入字段上我都没有收到那些烦人的红色数据验证错误! 多么令人耳目一新。 转到下一页。

OK. This page looks a little bit more suspicious. The look and feel is just like the real EE site but now they want my full name as shown ‘on card’, (whatever card that might be), card number, expiry date, the CVV code from the back/front of my card of choice, my date of birth… my sort code for my bank account, my bank account number… and my Mother’s Maiden name. All of those things look totally normal and definitely go together on a single page like this one, which still wants me to ‘Log in’.
好。 该页面看起来有点可疑。 外观就像真实的EE网站一样,但是现在他们想要我的全名,如“在卡上”所示(无论是哪种卡),卡号,有效期,卡背面/正面的CVV代码选择,我的出生日期……我的银行帐户代码,我的银行帐号……以及我母亲的娘家姓。 所有这些事情看起来都是完全正常的,并且绝对可以在这样的页面上放在一起,但仍然要我“登录”。
Still undeterred, I invent all of those details and move on to the next page.
仍不为所动,我发明了所有这些细节,然后转到下一页。

Excellent, I see the bank validation lefty-righty flashy-lighty page that the bank always does when validating stuff. Then the site presents me with the swirly-whirly ‘redirecting you’ page. Everything is looking good! My fingers are crossed and I’m hoping that everything worked.
太好了,我看到银行验证东西时银行始终会执行左右验证页面。 然后,该网站向我展示了令人费解的“重定向您”页面。 一切看起来都很好! 我的手指交叉了,我希望一切正常。

It Worked! I’ve successfully updated my name, address, date of birth, payment card details, bank account details, mothers maiden name, and inside leg measurement. Now I’m back on the real EE website and ready to log in to win huge tech prizes.
有效! 我已经成功更新了我的姓名,地址,出生日期,支付卡详细信息,银行帐户详细信息,母亲的娘家姓和内腿围。 现在,我回到了真正的EE网站,并准备登录以赢得巨大的技术奖。
And I’ve just been phished. Easy as that.
而且我只是被钓鱼了。 那样简单。
深入研究网络钓鱼 (Digging Deeper Into the Phish)
Now that we’ve seen what it does, let’s dig into the details a bit further.
现在我们已经了解了它的作用,让我们进一步深入研究细节。
网络钓鱼站点URL (The Phishing Site URL)
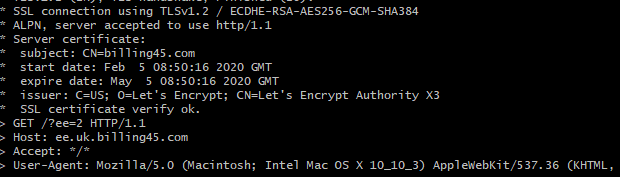
I expect that the link in the text message would look pretty convincing to most people: https://ee.uk.billing45.com/?ee=2. How are we to know it isn’t legit? It even has https to show us that it is a ‘secure website’. More on that later.
我希望短信中的链接对大多数人来说都具有说服力: https : //ee.uk.billing45.com/?ee = 2。 我们怎么知道这是不合法的? 它甚至带有https来告诉我们这是一个“安全网站”。 以后再说。
The end of the URL has a basic form of authentication included. The ee=2 parameter causes the page to load successfully. If you take away the ee parameter or change the value 2 to any other value the page fails to load.
URL的末尾包含基本的身份验证形式。 ee = 2参数导致页面成功加载。 如果删除ee参数或将值2更改为任何其他值,页面将无法加载。

This is a security/stealth mechanism to prevent people from stumbling upon the page by accident and reporting it. Automated web crawlers index good content and bad. The data captured can be used to identify phishing pages in the wild. By needing a token to access the phishing page (ee=2), automated crawlers are much less likely to stumble upon the site.
这是一种安全/隐匿机制,可以防止人们因意外而绊倒页面并进行报告。 自动化的网络爬虫索引好内容和坏内容。 捕获的数据可用于识别网络钓鱼页面。 通过需要令牌来访问网络钓鱼页面(ee = 2),自动爬网程序不太可能偶然发现该站点。
网络钓鱼网站软件 (Phishing Site Software)
Phishing sites are usually deployed using pre-built phishing kits. People write phishing kits for targeting different types of applications, websites, and people, and sell them to criminals who then deploy and use them as they see fit. The kits make it easy to deploy a site, capture sensitive information, verify visitors as potential targets through the use of a simple token (ee=2), redirect users to the real site after they’ve been phished, and switch the kit on and off.
网络钓鱼站点通常使用预先构建的网络钓鱼套件进行部署。 人们编写网络钓鱼工具包以针对不同类型的应用程序,网站和人员,然后将其出售给犯罪分子,然后由犯罪分子按照自己的意愿进行部署和使用。 这些工具包使部署站点,捕获敏感信息,通过使用简单令牌(ee = 2)将访问者验证为潜在目标,将用户被诱骗后重定向到真实站点以及打开工具包变得容易。和关闭。
This phishing kit is written in PHP and seems to only target the EE brand. I haven’t spent a lot of time trying to brute force other brand names to see if they also exist but I think it is unlikely. The URL in use is tailored to the EE brand to match the phishing kit content. There may be other phishing URLs hosted on this server but I haven’t gone looking for them.
该网络钓鱼工具包是用PHP编写的,似乎只针对EE品牌。 我没有花很多时间尝试强行使用其他品牌,看看它们是否也存在,但我认为这不太可能。 使用的URL是针对EE品牌量身定制的,以匹配网络钓鱼工具包的内容。 该服务器上可能还托管有其他网络钓鱼URL,但我没有去寻找它们。
挂锁死了 (The Padlock Is Dead)
The https padlock on this site simply shows that traffic between your browser and the webserver is encrypted. Nothing more. The SSL encryption certificate which your browser uses to verify the site is indeed ee.uk.billing45.com is provided by https://letsencrypt.org/. This is an excellent service as it allows anyone to encrypt traffic to and from their website for free. Sadly, that also includes the bad guys who want a padlock on their malicious websites. Letsencrypt is great for privacy but not so great for preventing phishing attacks.
该站点上的https挂锁仅表明您的浏览器和Web服务器之间的流量已加密。 而已。 您的浏览器用来验证站点的SSL加密证书确实是ee.uk.billing45.com,由https://letsencrypt.org/提供。 这是一项出色的服务,因为它允许任何人免费加密往返其网站的流量。 可悲的是,其中还包括想要在其恶意网站上挂锁的坏人。 Letsencrypt对于保护隐私很有用,但对于防止网络钓鱼攻击却不是那么有用。
To display a padlock on this site, all the admin needed to do was request and approve a certificate through the LetsEncrypt platform. They’re generated in a few seconds and installed automatically. Once done, the site is trusted by all modern browsers. The visible padlock gives the site credibility despite the fact that no credibility checks have actually been done.
要在此站点上显示挂锁,所有管理员所需要做的就是通过LetsEncrypt平台请求并批准证书。 它们会在几秒钟内生成并自动安装。 完成后,所有现代浏览器都可以信任该站点。 尽管实际上没有进行任何可信度检查,但可见的挂锁仍可确保站点的可信度。
We spent years educating people to only trust web sites with the padlock in the URL bar. Today, anyone can get a padlock with almost no upfront cost or effort. The ‘trust the padlock’ message is now working against us.
我们花了多年的时间来教育人们仅信任URL栏中带有挂锁的网站。 如今,任何人都可以在几乎没有前期成本或精力的情况下获得挂锁。 “信任挂锁”消息现在正在对我们不利。
撰写网络钓鱼/网络钓鱼短信 (Writing Phishing/Smishing Text Messages)
In my article 9 Things I’ve Learned Writing Phishing Emails I talk about the use of language to convince people to take a specific action. The words ‘in order to avoid fees’ are all that is needed to convince many people to click the link and start filling in details. Our aversion to loss, paying more money than we should have done, is a very strong motivator.
在我的文章9我学过的编写网络钓鱼电子邮件的知识中,我谈到了使用语言说服人们采取特定行动。 要说服许多人单击链接并开始填写详细信息,只需使用“为了避免收费”一词即可。 我们对损失的厌恶,付出的钱比我们应该做的要多,这是一个非常强烈的动机。
SMS messages are capped at 160 characters of text including spaces. Because of this, a phishing message delivered over text message needs to be short, specific, and powerful. Every character is precious. This smishing message achieves:
SMS消息的文本上限为160个字符,包括空格。 因此,通过文本消息传递的网络钓鱼消息必须简短,特定且功能强大。 每个角色都是宝贵的。 此欺骗消息可实现:
- Authority. ‘[EE]’ identifies them as the phone provider, EE. If you receive this message and EE is indeed your phone provider then they’re stating that they have power over your contract and your connection to the rest of the world.权威。 “ [EE]”将其标识为电话提供商EE。 如果您收到此消息,而EE确实是您的电话提供商,则他们表示他们对您的合同以及您与世界其他地方的连接拥有控制权。
- Define a problem. ‘We were unable to process your latest bill.’定义问题。 “我们无法处理您的最新账单。”
- Invoke feelings of fear, loss aversion, and urgency. ‘In order to avoid fees’. The urgency is an implicit statement as we all know that late fees are a very real thing.唤起恐惧,厌恶情绪和紧迫感。 “为了避免收费”。 紧迫性是一个隐含的陈述,因为我们都知道滞纳金是很真实的事情。
- The solution to your problem. ‘Update your billing information via…’ tells you how to prevent feeling the pain alluded to in 2 and 3.解决您的问题。 “通过...更新您的帐单信息”告诉您如何避免感觉到2和3中提到的痛苦。
网络钓鱼站点受到实时监视 (Phishing Sites are Monitored in Real-Time)
These sites are monitored while SMS phishing attacks are taking place. SMS messages are sent at a cost and attackers want to make the most out of their investment. Sending 10,000 text messages and watching for responses for the next 2 hours will yield an excellent return on the black market. It also allows attackers to spot threats and shut their operation down when people like me start poking around.
在SMS网络钓鱼攻击发生时,将监视这些站点。 SMS消息的发送成本很高,攻击者希望最大程度地利用其投资。 在接下来的2小时内发送10,000条短信并等待回复,这将在黑市上获得丰厚的回报。 当像我这样的人开始四处张望时,它还允许攻击者发现威胁并关闭其操作。
In order to walk through this phishing experience, I entered false details on every page. At the end of the process, all of the information will have either been written to a local file on the server, sent to a remote server, or emailed to a free email address from Gmail, Hotmail, Protonmail, etc.
为了获得这种网络钓鱼的经验,我在每一页上输入了虚假的详细信息。 在此过程结束时,所有信息都将被写入服务器上的本地文件,发送到远程服务器,或者通过Gmail,Hotmail,Protonmail等通过电子邮件发送给免费的电子邮件地址。
By the time I went back for a second pass at 18:16, just 3 minutes after I submitted the first set of forms, someone had seen my fake details and deactivated the phishing kit. If you visit /?ee=1 or any other non-verified link you still get the same error message as before. If you visit /?ee=2 you get redirected to the real EE.co.uk website instead of being shown the phishing kits data capture pages.
当我在提交第一套表格仅3分钟后的18:16返回第二遍时,有人看到了我的虚假信息并停用了钓鱼工具包。 如果您访问/?ee = 1或任何其他未验证的链接,您仍会收到与以前相同的错误消息。 如果您访问/?ee = 2,则您将重定向到真实的EE.co.uk网站,而不是看到网页仿冒工具数据捕获页面。
I suspect that my clearly made-up information alerted the attacker to the fact that I’d discovered their scam and that their time was up. Deactivating the phishing kit prevents further investigation into what the kit does and buys them time to process what they’ve captured so far. Ultimately, phishing attacks are all about stealth. When the game is up, it’s time to move on.
我怀疑我的虚假信息使攻击者意识到我发现了他们的骗局,并且他们的时间到了。 停用网络钓鱼套件将阻止进一步调查套件的功能,并为其腾出时间来处理迄今为止捕获的内容。 最终,网络钓鱼攻击完全与隐身有关。 游戏结束时,该继续前进了。
网络钓鱼/网络钓鱼攻击跌落的影响 (The Impact of Falling for This Phishing / Smishing Attack)
If you fall for an attack like this, you’ve given away your email address and password, name, address, and telephone number, date of birth, credit card information, bank information, and answer to a very common security question (mother’s maiden name). All of this can be sold on the black market for profit or used directly to commit fraud, gain access to your other accounts, steal your mobile phone number by moving it from your SIM card to theirs, and more.
如果您遭受这样的攻击,则已经放弃了您的电子邮件地址和密码,姓名,地址和电话号码,出生日期,信用卡信息,银行信息,并回答了一个非常常见的安全性问题(母亲的娘娘腔)。名称)。 所有这些都可以在黑市上出售以牟利,也可以直接用于欺诈,获取其他帐户的访问权限, 通过将SIM卡中的手机号码转移到他们的手机号码等来窃取您的手机号码 。
Even if you only complete the first of several steps, any information you’ve typed into the forms on your browser should be considered compromised. There’s nothing stopping them from recording each page individually as you move through the phishing site, or even scraping every keystroke you make while on their page, even if you don’t actually hit submit. Once you’re on a phishing site you’re in danger and everything you do is being watched.
即使仅完成了几个步骤中的第一步,您在浏览器中输入的所有信息也应视为已泄露。 没有什么可以阻止他们在您进入钓鱼网站时单独记录每个页面的,甚至是刮擦您在页面上进行的每次击键,即使您实际上没有点击提交也是如此。 一旦进入钓鱼网站,您将面临危险,您所做的一切都将受到监视。
If you do fall for a scam like this, change all of your passwords, change all of your security questions, enable Multi-Factor Authentication on all of your accounts that support it, contact your bank, and contact the relevant authorities for reporting cybercrime and fraud.
如果您确实喜欢这种骗局,请更改所有密码,更改所有安全性问题,在支持该功能的所有帐户上启用“多因素身份验证”,然后与您的银行联系,并与相关机构联系以举报网络犯罪和舞弊。
Join the others in my private email list to stay up-to-date with my latest articles, videos, thoughts, and more.
将其他人加入我的私人电子邮件列表中,以了解我的最新文章,视频,想法等最新信息。
Originally published at https://craighays.com on February 5, 2020.
最初于 2020年2月5日 发布在 https://craighays.com 。
翻译自: https://medium.com/swlh/inside-a-real-sms-phishing-attack-smishing-4b5e325f3fa
http://www.taodudu.cc/news/show-4232899.html
相关文章:
- 前端登录注册页面、多方式登录功能、腾讯云短信发送功能二次封装(包)、发送短信接口
- python adb读取手机中短信_python+adb实现自动化获取手机信息
- 如何调用外部webservice 接口来发送短信
- 通知栏显示流程
- android广播监听短信并显示内容
- 05短信发送验证
- JS短信接口代码示例
- 使用js的方式设置点击按钮发送短信倒计时并且防止刷新
- Redis存放短信验证码 RedisTemplate =>opsForValue
- PyMc01短信推断
- 微信短信显示服务器解包异常,最新微信小程序解包反编译bug处理 解决 $gwx is not defined 错误...
- twilio php 发送短信,如何使用 Twilio 实现语音和短信功能 (PHP) | Microsoft Docs
- jquery短信验证码倒计时
- Re: Object Oriented
- c# 分数处理
- http://39.98.219.132 题库标准答案(题库序号:463)之编写一个给一个分数约分的程序
- python假分数约分,数学中假分数怎么约分
- java 约分_java如何将分数快速约分
- 北航计算机机试13真分数约分
- 用Java编写约分最简公式_一个有趣的算法问题:如何定义一个分数类
- python输入一个分数、约分后输出_Python中分数的相关使用教程
- python分数约分_Python基础知识
- C语言约分-化为最简分数
- 分数约分方法
- python分数约分_python分数的四则运算
- 实现分数的约分
- java 约分_约分的方法
- 【C++PTA】7-1 运算符重载 分数类 约分
- 分数约分
- C++:分数处理(约分、加减乘除、假分数输出)
在真正的短信网络钓鱼攻击内部相关推荐
- 防不胜防?网络钓鱼攻击常用手法盘点与防护建议
[环境搭建资料.工具包.全套视频-等籽料]私信聆取 网络钓鱼攻击是最常见.最容易让受害者中招的网络犯罪之一,随着网络技术的不断发展,攻击者的伪装手段也变得愈发狡诈,攻击频次也再增高,各种新奇的攻击方式 ...
- 网络类型_多种类型的网络钓鱼攻击和诈骗
点击标题下「蓝色微信名」可快速关注 网络钓鱼攻击每年都会对企业造成重大损失和损害 谷歌和Facebook的损失总计超过1亿美元.比利时克里兰银行向网络犯罪分子交付了超过7500万美元.奥地利航空零部件 ...
- 钓鱼攻击防不胜防,该如何预防网络钓鱼攻击?
"网络钓鱼"是一种网络欺诈行为,是指不法分子利用各种手段,仿冒真实网站地址及页面内容,欺骗消费者或者窃取访问者提交的账号和密码等私人信息.钓鱼网站通常主要通过电子邮件.短信等网络方 ...
- 常见的5种网络钓鱼攻击类型!
网络钓鱼攻击是比较常见且人人熟知的一种攻击方式,虽然这种攻击方式不是以入侵为主要,但其危害范围极大,也是最严重的网络威胁之一.目前,网络钓鱼攻击类型有很多种,本文主要为大家介绍一下"常见的5 ...
- 新套路+老配方 | 2023年网络钓鱼攻击新方式
在过去的几年,随着网络攻击技术的更新进步,攻击活动日益猖獗.企业不得不改变和增加防范手段,不断进步和优化办公策略来减少安全事件的发生. 如今超过90%的数据泄露是由"云钓鱼"为主的 ...
- 6.2 网络钓鱼攻击
目录 一.了解网络钓鱼 二.实验环境 三.实验步骤 四.实验过程中出现的一些问题 一.了解网络钓鱼 网络钓鱼(phishing)由钓鱼(fishing)一词演变而来.在网络钓鱼过程中,攻击者使用诱饵( ...
- 实例解析网络钓鱼攻击的幕后
实例解析网络钓鱼攻击的幕后 网络钓鱼是通过大量发送声称来自于银行或其他知名机构的欺骗性垃圾邮件,意图引诱收信人给出敏感信息(如用户名.口令.帐号ID.ATM PIN码或信用卡详细信息)的一种攻击方式. ...
- AI+网络安全 让鱼叉式网络钓鱼攻击无所遁形
2017年是网络攻击极其活跃的一年,全球先后发生了多起大型网络攻击事件,例如令人震惊的Wanna Cry勒索病毒席卷全球,包括中国在内的150多个国家受到网络攻击.各国企业.学校.医院等机构无一幸免, ...
- 披露针对安卓手机的高级SMS网络钓鱼攻击,可被远程安装恶意设置项
本文会过多涉及OMACP,有的小伙伴可能会感到陌生,实际上其就是手机里的OMACP应用,英文为 OMA(Open Mobile Alliance) Client Provisioning 协议实例,或 ...
最新文章
- boost::geometry::detail::as_range用法的测试程序
- RobotFramework读取mysql和oracle数据库
- centos6.5搭建php网站,Centos6.5下搭建web环境(Apache+mysql+php+phpMyAdmin)
- 操作系统原理(二)操作系统逻辑结构、CPU的态和中断机制
- 曹 雷 : 证券基金经营机构如何理解科技是投资而非投入
- 《证券基金经营机构信息技术管理办法》要点简读
- 桑拿锁技术升级:桑拿手牌复制休矣!
- 彻底清除微软拼音输入法
- 梯度消失,梯度爆炸产生的原因及解决办法
- HTML5期末大作业:温泉酒店网站设计——中国风的温泉酒店网(13页) HTML+CSS+JavaScript 学生web网页制作期末大作业_住宿 旅游 主题酒店
- 父级fixed_相对于父元素的fixed定位的实现
- 全球智能制造产业联盟落地深圳
- 李白打酒递归java_李白打酒----递归理解
- 技术经理成长复盘-我是什么样的人
- AI三大主义:符号主义、联结主义、行为主义
- Android 传感器开发详解
- Android平台使用-谷歌广告联盟AdMob-赚取收益的编程方法
- Python3中print的高级用法——print中执行命令和函数:print(*meta)
- PCB地与机壳电容连接 转
- MPC算法轨迹跟踪控制资源
热门文章
- 网页使用微信扫码登录
- 计算机文档考试题目及答案,计算机word考试题及答案解析
- 微信公众号本地环境搭建(解决微信接口需要公网地址,但是只有本地环境的问题)
- 抓包工具 HTTP Analyzer v7.5 的下载,安装,使用,破解说明
- 计算机认知训练效果,为轻度认知功能障碍的人保持认知功能而进行的计算机化认知训练...
- 基于Token的验证方式(JWT简笔)
- 微信公众号开发以及测试公众号菜单配置
- WPF实战之DataGrid设置行高
- maven打包缺少依赖异常eu.neilalexander:jnacl:jar:1.0.0 was not found in...解决
- 移动端web总结(一)——JDM项目总结
