linkedin 架构_如何通过linkedin消息发现网络钓鱼
linkedin 架构
Just a few days after been falsely accused by my former web host of operating a phishing scam (the accusation still burns!) I received a LinkedIn message from a literary agent connection that piqued my interest.
几天前,我的前网络托管服务商错误地指控我进行了网络钓鱼诈骗(指控仍在燃烧!),我从一家文学代理机构收到了LinkedIn消息,激起了我的兴趣。
Something about the message felt a little in-genuine, however a literary agent reaching out to a writer in this manner wouldn’t be unheard of (although this may be pure happenstance and whoever devised the attack just hit lucky with a credible background).
关于此消息的某些知识有些入微, 但是以这种方式与作家接触的文学代理并不是闻所未闻的(尽管这可能纯粹是偶然的,并且设计攻击的人只是幸运地拥有可信的背景)。
So I decided to check out the OneDrive share.
因此,我决定查看OneDrive共享。
Here are some things I did to investigate the suspicious share and correctly determine that it was a phishing attempt.
我做了一些调查可疑份额并正确确定这是网络钓鱼尝试的事情。
1:检查网址结构 (1: Check the URL Structure)
If you’re dubious that something you’ve received in this manner might be a phishing scam, the first place you should check is the URL bar.
如果您怀疑以这种方式收到的内容可能是网络钓鱼诈骗,则应首先检查URL栏。
In this case, the link was to a genuine OneDrive share.
在这种情况下,链接是指向真正的OneDrive共享的。
Note that, in Google Chrome, the padlock symbol to the left of the URL is marked as secure, indicating that the connection to the website is encrypted and secured by a valid Secure Socket Layer (SSL) certificate.
请注意,在Google Chrome浏览器中,URL左侧的挂锁符号标记为secure ,表示与网站的连接已通过有效的安全套接字层(SSL)证书进行加密和保护。

2:检查SSL证书 (2: Check the SSL Certificate)
Both the fact that the connection has an SSL certificate and the issuing authority are important pieces of information: discrepancies (the phishing attempt uses a self-signed certificate and the operator issues under its own name) can be valuable clues that something is amiss.
连接具有SSL证书这一事实和颁发机构都是重要的信息:差异(网络钓鱼尝试使用自签名证书,而操作员以其自己的名义发布)可能是有价值的线索,说明存在问题。
Let’s take a look at the SSL issuer certificate so that we can compare and contrast anything that changes:
让我们看一下SSL颁发者证书,以便我们可以比较和对比任何更改的内容:
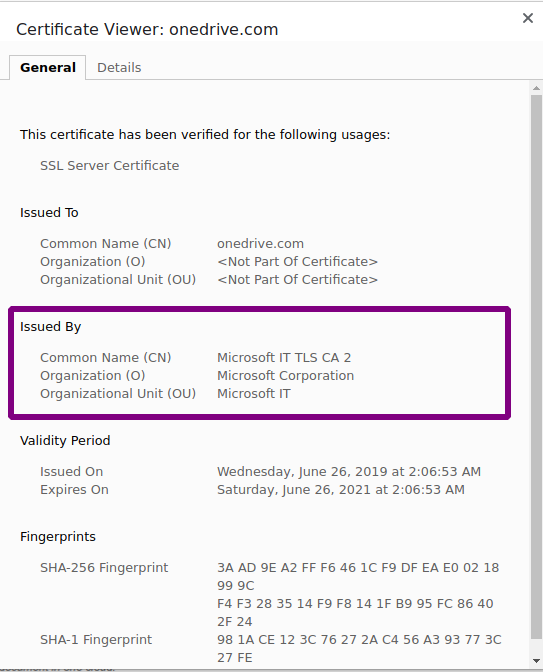
As I would have expected, the SSL certificate on OneDrive.com, where legitimate OneDrive shares are hosted, is issued by Microsoft Corporation.
如我所料,托管合法OneDrive共享的OneDrive.com上的SSL证书是由Microsoft Corporation发行的。
3:提防狡猾的图形 (3: Watch Out For Dodgy Graphics)

Here’s where things got a bit phishy (get it)?
这是东西有点麻痹的地方(得到它)?
There’s no reason why the sender couldn’t have simply sent an open access link. Instead, this looks like a OneDrive link to another OneDrive folder.
没有理由不能使发送者简单地发送开放访问链接。 而是,这看起来像是指向另一个OneDrive文件夹的OneDrive链接。
But look at the image that’s embedded.
但是,看看嵌入的图像。
As a company with more than $125 billion in annual revenue, Microsoft are not lacking the budget to hire a graphic design team — so the pixellated image immediately drew my suspicion.
作为一家年收入超过1250亿美元的公司,Microsoft并不缺少聘请图形设计团队的预算- 因此像素化图像立即引起了我的怀疑。
Next, read the copy it contains:
接下来,阅读其中包含的副本:
“You have a new secure message for your perusal from X”.
“您有一个新的安全消息 供您细阅 X”。
There’s no way that a staid corporate like Microsoft would use such jocular phrasing as “for your perusal “ in their standard OneDrive share template notification.
像Microsoft这样的老套公司绝对不可能在其标准OneDrive共享模板通知中使用诸如“供您细读 ”之类的俗语。
Besides comparing how this link looked with a OneDrive share link which we know to be valid, we could also run an exact string search on Google to check if this suspicious line of copy has been reported as malware anywhere else on the internet.
除了将链接的外观与我们知道有效的OneDrive共享链接进行比较之外,我们还可以在Google上进行精确的字符串搜索,以检查此可疑副本是否已在互联网上其他任何地方被报告为恶意软件。
4:在可疑UI副本上运行搜索 (4: Run Searches On Suspicious UI Copy)
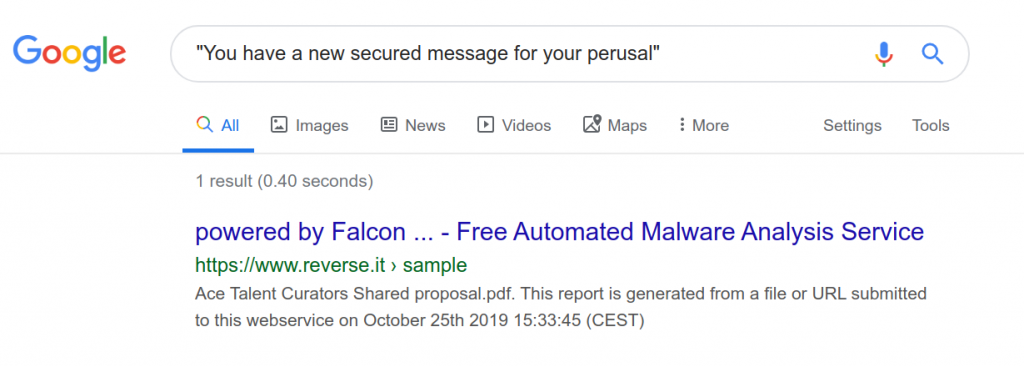
The one match here is from Hybrid Analysis, a free malware analysis service. Evidently, somebody has submitted this message for analysis:
一个匹配项来自免费的恶意软件分析服务Hybrid Analysis。 显然,有人已提交此消息进行分析:
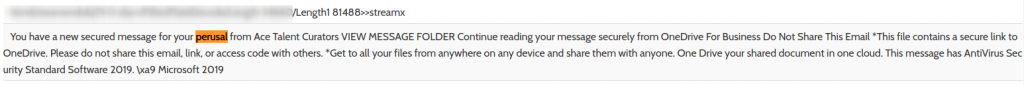
When we click the “View Message Folder” button, we are then taken to another login.
当我们单击“查看邮件文件夹”按钮时,我们将转到另一个登录名。
5:当心网上诱骗URL! (5: Watch Out For Phishing URLs!)
This brings us to a pretty typical phishing landing page.
这将我们带到一个非常典型的网络钓鱼登录页面。
Notice two things from the Omnibox:
请注意多功能框上的两件事:
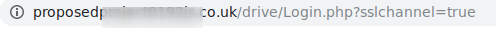
a) We’re now on an external website. Although conceivably, this could be achieved legitimately by the operator adding a CNAME DNS record if OneDrive allowed white-labeling a store site (I don't believe that they do).
a)我们现在在外部网站上。 尽管可以想象,如果OneDrive允许在商店站点上用白标签标记(我不认为这样做),则可以通过操作员添加CNAME DNS记录来合法地实现这一点。
b) The SSL certificate has vanished.
b)SSL证书已消失。
c) It’s no longer a Microsoft-issued certificate:
c)不再是Microsoft颁发的证书:
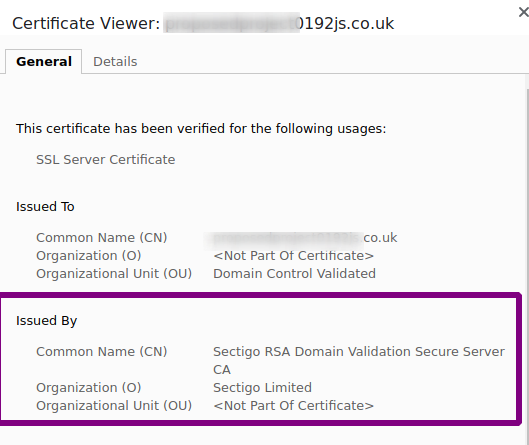
If we look into the issuing authority, we see that it’s certificates are being hocked on a website called cheapsslsecurity.com.
如果我们查看签发机构,就会发现它的证书在一个名为cheapsslsecurity.com的网站上受骗 。
Again, I think that Microsoft have enough money to be throwing around not to have to deal with such a disreputable-sounding operator.
再一次,我认为微软有足够的钱去花钱,而不必与这样一个声名狼藉的运营商打交道。

6:始终使用一次性登录凭证 (6: Always Use Throwaway Login Credentials)

If you want to be brave and explore further, under no circumstances provide your actual login credentials to a website that appears to be a phishing scam!
如果您想勇敢尝试并进一步探索,请在任何情况下都不要将您的实际登录凭据提供给似乎是网络钓鱼骗局的网站!
Doing so is all that is required to pass on your login details to the operator. Then, you’re effectively done for and your Gmail username and password could easily wind up on a dark web marketplace.
这样做是需要通过你的登录信息,以运营商所有 。 然后,您已完成工作,您的Gmail用户名和密码可以轻松地在黑暗的网络市场上收尾。
For the purpose of verifying that this was indeed a scam (at this stage I was 99% sure), I set up a throwaway @outlook.com address just so that I could safely get through the login credential to access the “share”.
为了验证这确实是一个骗局(在这个阶段,我有99%的把握),我设置了一个一次性@ outlook.com地址,以便可以安全地通过登录凭据来访问“共享”。
Here there were some further discrepancies:
这里还存在一些差异:
If you pay close attention to the phishing login dialogs and actual ones you can often notice subtle differences.
如果您密切注意网络钓鱼登录对话框和实际的登录对话框,通常会发现细微的差别。
当心细微的UI差异 (Watch Out For Subtle UI Discrepancies)
This is the phishing login for Google that the page linked to after I chose to log in through a Google account:
这是我选择通过Google帐户登录后页面链接到的Google的网络钓鱼登录名:
And this is an actual Google login that I just accessed and screenshotted to get to my GSuite email:
这是我实际访问的Google登录信息,并对其进行了截图以获取GSuite电子邮件的屏幕截图:
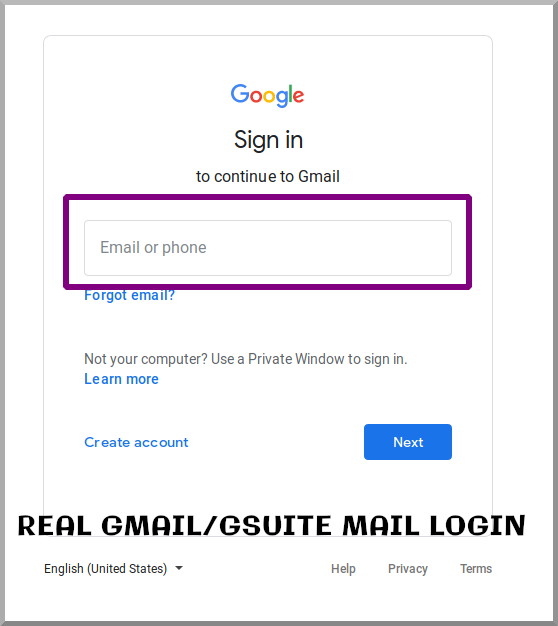
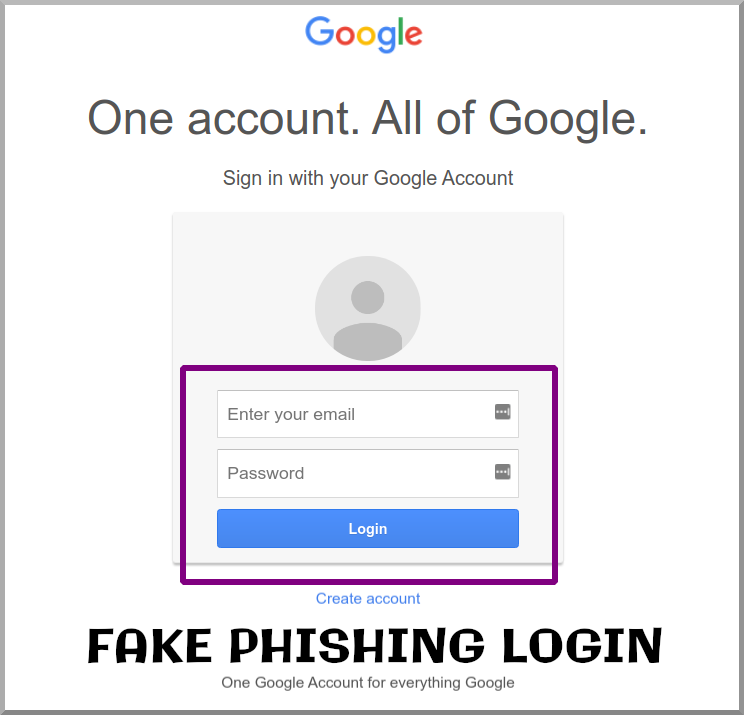
Notice any differences?
注意到有什么区别吗?
a) Google’s current UI only prompts for username first and then password, not both at the same time.
a) Google当前的用户界面仅提示您先输入用户名,然后提示密码 ,而不是同时提示输入密码 。
b) The genuine Google login doesn’t feature the footer text “One Google Account for everything Google”
b) 真正的Google登录名没有页脚文本“一个Google帐户,可容纳所有Google产品”
c) There are other obvious differences.
c)还有其他明显的差异。
Like many phishing attempts, this is a bad forgery.
像许多网络钓鱼尝试一样,这是伪造的。
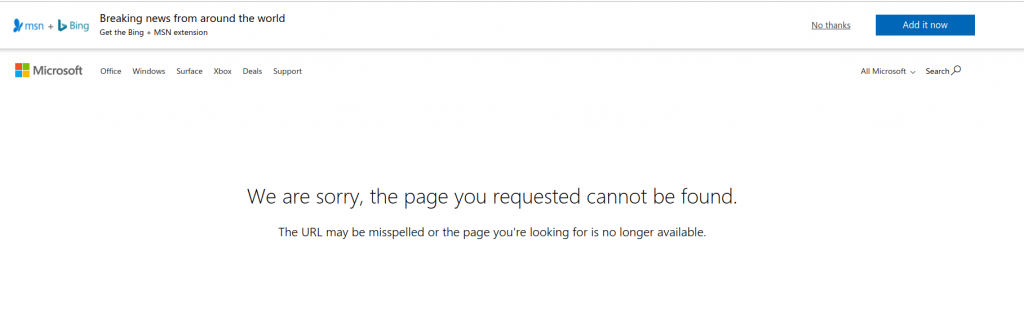
I logged in using my @outlook.com burner account and was greeted by an empty screen.
我使用@ outlook.com刻录机帐户登录,并被一个空白屏幕打招呼。
The URL had also reverted to live.com so, after capturing the credentials, the phishing operator had presumably wanted the user to give up.
该URL也已还原为live.com,因此,在捕获凭据后,网络钓鱼操作者可能希望用户放弃。
7:检查WHOIS (7: Check the WHOIS)
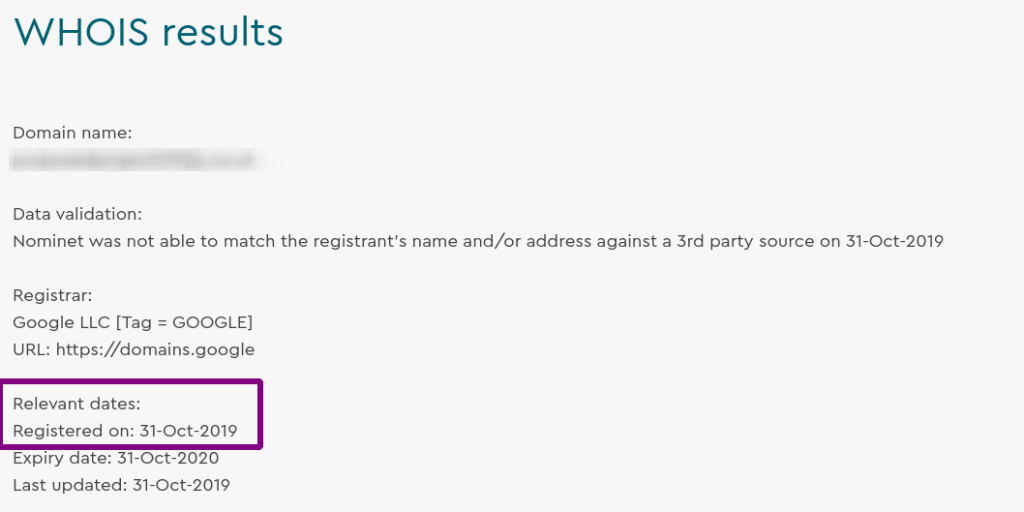
If you’ve determined beyond reasonable doubt that the domain is part of a phishing scam, it might be worth running a WHOIS lookup to see if you can alert the registrar and get the site pulled before vulnerable users hand over their actual login credentials.
如果您毫无疑问地确定该域是网络钓鱼骗局的一部分,则可能值得运行WHOIS查找,以查看是否可以在易受攻击的用户移交其实际登录凭据之前提醒注册服务商并拉动该站点。
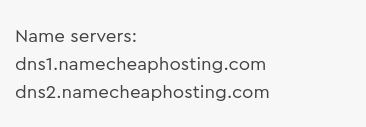
This domain had been in operation for just 12 days and the nameservers detected indicate that it was being hosted on NameCheap.
该域仅运行了12天,检测到的域名服务器表明该域名托管在NameCheap上。
In this case, as a good deed for the day, I will alert NameCheapHosting to the fact that their services are being used to host a phishing site.
在这种情况下,作为当下的好事,我将提醒NameCheapHosting有关其服务已用于托管网络钓鱼站点的事实。
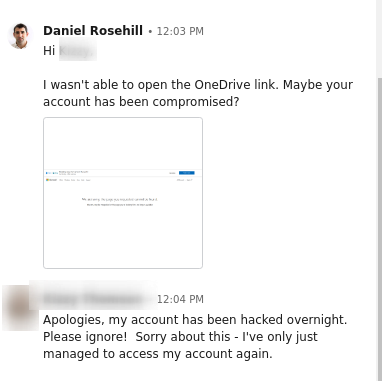
I contacted the account owner and my suspicions were confirmed:
我与帐户所有者联系,并确认了我的怀疑:
得到教训 (Lessons Learned)
a) Be suspicious of any drive shares from strangers!
a)怀疑来自陌生人的驱动器共享!
b) Always check the URL and SSL cert to differentiate between a genuine website and a phishing one.
b)始终检查URL和SSL证书以区分真正的网站和网络钓鱼网站。
Originally published at https://www.danielrosehill.co.il
最初发布在 https://www.danielrosehill.co.il
翻译自: https://medium.com/daniels-tech-world/how-to-spot-phishing-by-linkedin-message-952ecb813ae9
linkedin 架构
相关文章:
- 深度学习网络每一层维度_每个人都可以使用深度学习
- 双击事件_双击
- ai 预测未来股市_是预测分析的未来,人工智能将如何将其提升到一个新的水平...
- 文本数据可视化_非结构化文本数据的分析和可视化
- win10拷贝到linux文件夹很慢,samba和nfs互相拷贝时速度奇慢的原因
- Ubuntu11.10耳机没声音?解决之...
- Sound Spaces: Audio-Visual Navigation in 3D Environments(2020)
- Semantic Audio-Visual Navigation(2021)
- View Controller Initialization
- QT 遇到的错误记录
- 微信已过期或被清理的图片怎么恢复?4种方法!
- 微信图片预览
- 11月14日报告
- NeurIPS 2021 | 用于物体检测的实例条件知识蒸馏
- 【GNN报告】考虑拓扑信息的图神经网络学习
- 上交大许志钦:神经网络中的奥卡姆剃刀——简单有效原理
- 直播预告 11.18 | KDD-7,纽约大学斯特恩商学院、伊利诺伊大学香槟分校 PhD
- 3月3日 10:00 | AI研讨班正式启航!
- android 2.2手机,Android2.2即将来临?最值得购买的手机推荐
- 掉价最快的手机排行榜_要说掉价最快的手机,当属这部了,从3199将至999元!...
- 3000元手机性价比排行榜2022 3000元手机买什么好
- 软件开发公司怎么用抖音宣传
- 拍抖音的素材
- 抖音爆款广告怎么拍?4大技巧助力品牌打造爆款
- 拍摄抖音短视频使用BGM是否构成侵权?
- 成都欢蓬电商:拍抖音唱歌怎么显示歌词?
- 字节跳动小程序点击右上角分享胶囊设置“拍抖音”和“分享”功能
- Web3的“陨落”,西下与东升
- 深入解读Airbnb推荐算法
- 大数据毕业设计 二手房数据爬取与分析可视化系统 -python
linkedin 架构_如何通过linkedin消息发现网络钓鱼相关推荐
- linkedin 架构_投票:您如何使用LinkedIn?
linkedin 架构 Business social network LinkedIn announced that they've turned on their OpenSocial-power ...
- 鱼叉式网络钓鱼和网络钓鱼_您需要了解的反网络钓鱼标准–第1部分
鱼叉式网络钓鱼和网络钓鱼 *This article by Marc Laliberte was originally published in the October edition of Cybe ...
- linkedin 分享_如何在LinkedIn上记录和显示您的名字发音
linkedin 分享 Justin Duino 贾斯汀·杜伊诺(Justin Duino) Having a last name that almost no one pronounces corr ...
- linkedin爬虫_您应该在LinkedIn上关注的8个人
linkedin爬虫 Finding great mentors are hard to come by these days. With so much information and so man ...
- linkedin爬虫_如何建立一个惊人的LinkedIn个人资料[15+个行之有效的技巧]
linkedin爬虫 Looking for some LinkedIn profile tips to help you step up your game, beat out the compet ...
- linkedin 分享_如何管理您的LinkedIn隐私设置
linkedin 分享 FGC/ShutterstockFGC /快门 LinkedIn is a great way to connect with professionals in your fi ...
- linkedin 分享_如何永远阻止LinkedIn的烦人电子邮件
linkedin 分享 Like most social networks, LinkedIn loves to send you emails. While they can be a handy ...
- linkedin爬虫_重新设计Linkedin的指导功能-用户体验案例研究
linkedin爬虫 为什么选择导师+ Linkedin平台? (Why mentorship + Linkedin platform?) As a recent graduate, I went o ...
- linkedin 分享_如何在保持电子邮件私密性的同时导入LinkedIn联系人
linkedin 分享 When you use LinkedIn, it's all about who you know. However, to import contacts, you nor ...
最新文章
- 将不确定变为确定~异常被抛出的顺序
- Python 这么火,如何快速掌握?
- 区块链学堂(5):Geth 安装
- js特效 在服务器显示变形,使一行文字变形产生弯曲弧度特效的jQuery插件 - Arctext.js...
- 二阶偏微分方程组 龙格库塔法_有限单元法(Finite Element Method)实现声波方程模拟(Part 2)...
- 再见,RabbitMQ,你好,Kafka!
- 【每日SQL打卡】DAY 27丨每次访问的交易次数【难度困难-提前放出来】
- django-动态的读取静态目录路径
- Intel Core Enhanced Core架构/微架构/流水线 (12) - 数据预取
- Domino邮件服务器防垃圾邮件中转
- Ext4及F2FS文件系统 Debug
- KindEditor上传图片word
- 计算机帮教助教活动总结,家长助教活动总结范文(精选5篇)
- 从少年变成老男孩-----韩寒与郭敬明的十年
- 信号完整性基础01:从频域出发理解信号(1)-时域和频域
- stm32F407中arr与psc以及pwm之间的关系
- 华硕重装后进入bios_华硕电脑重装系统后开机直接进入BIOS原因分析及解决方法...
- 【音乐可视化】Audacity,一款免费的多轨音频编辑器
- 怎样加入一个开源项目?
- elementui DateTimePicker组件 限制时间范围(包含时分秒)
