python简史_移动恶意软件简史
python简史
系列概述: (Series outline:)
Part 1: A Short History of Mobile Malware (you are here)
第1部分:移动恶意软件的简要历史记录( 您在此处 )
Part 2: The Layers of the Android Security Model
第2部分: Android安全模型的各层
Part 3: Mitigating Android Social Engineering Attacks
第3部分 : 缓解Android社交工程攻击
The context generated by the COVID-19 pandemic determined attackers to retarget their arsenal towards a more susceptible audience.
COVID-19大流行产生的环境决定了攻击者将他们的武器库重新瞄准了更易受影响的听众。
To an extent, the human immune system is able to adapt and defend people against the threat of biological viruses.
在一定程度上, 人类的免疫系统能够适应并保护人们免受 生物病毒 。
Yet, what is there to defend them against computer viruses?
但是,有什么方法可以防御计算机病毒?
To identify the recurrent vulnerability that is being exploited by attackers, we will take a short journey through the history of mobile malware.
为了确定攻击者正在利用的反复出现的漏洞,我们将在移动恶意软件的历史中进行很短的旅程。
移动恶意软件时间表 (The Mobile Malware Timeline)
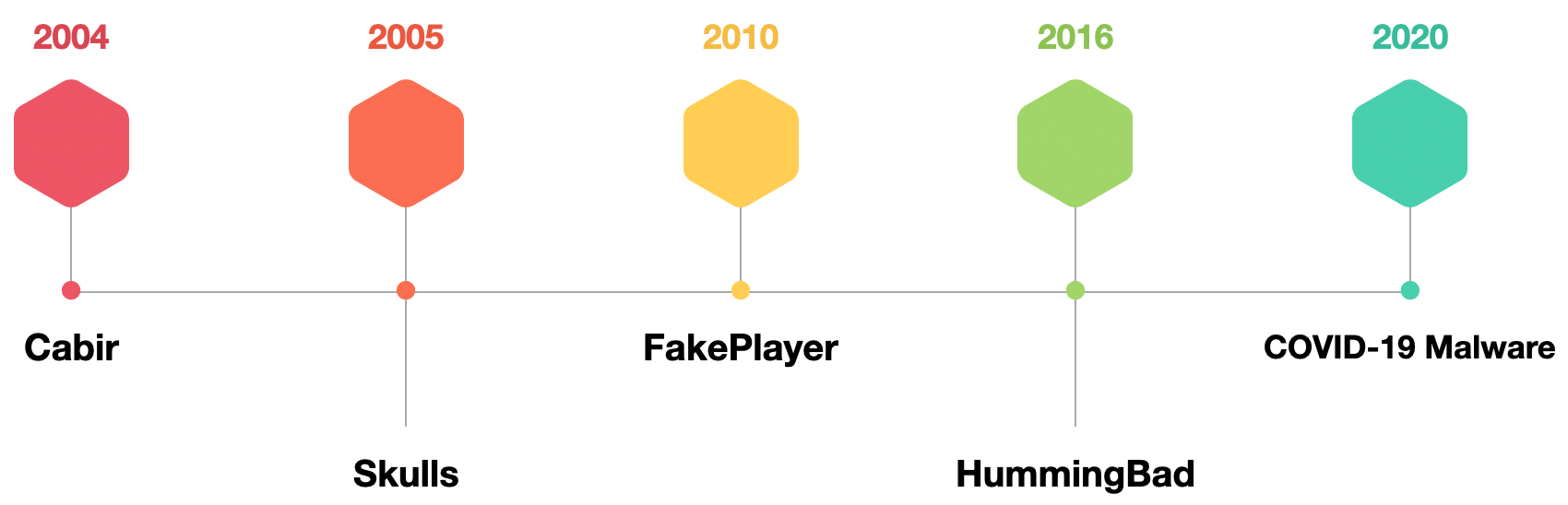
The virus writers haven’t yet penetrated the mobile malware sector until 2004, when the first mobile virus (targeting and running on a mobile device), was found in the wild. The source code of this virus acted as a base for the surge of subsequent mobile malware.
直到2004年 ,在野外发现了第一个移动病毒(针对并在移动设备上运行)后,病毒编写者才进入移动恶意软件领域。 该病毒的源代码为随后的移动恶意软件激增奠定了基础。
1.卡比尔(2004) (1. Cabir¹ (2004))
Mobile security became a concern in June 2004, when a professional virus and worm coder group known as 29A created a virus named Cabir (also known as Caribe, Syb- mOS/Cabir, Symbian/Cabir and EPOC.cabir). It was named by Kaspersky employees after their colleague Elena Kabirova.
2004年6月,当一个专业的病毒和蠕虫编码者小组称为29A创建了一种名为Cabir的病毒( 也称为Caribe,SybmOS / Cabir,Symbian / Cabir和EPOC.cabir )时,移动安全成为一个问题。 卡巴斯基公司员工以同事Elena Kabirova的名字命名。
At Kaspersky, Roman Kuzmenko was responsible for the analysis of the virus. It didn’t took him long to find out that the virus was designed for Symbian OS running on an ARM processor.
在卡巴斯基,Roman Kuzmenko负责病毒分析。 他花了很长时间才发现该病毒是为运行在ARM处理器上的Symbian OS设计的。
This combination of OS and processor existed only in Nokia phones. Consequently, it was assumed that the virus is targeting mobile phones — the first virus for mobile phones.
操作系统和处理器的这种组合仅在诺基亚手机中存在。 因此,可以认为该病毒针对的是手机,这是第一款手机病毒 。
Getting a hold of a yet to be established area of security was a hard task but it proved to be a success.
掌握尚未建立的安全领域是一项艰巨的任务,但事实证明是成功的。
It was discovered that the virus’ main feature was the ability to use the Bluetooth protocol to transfer files. This was its sole mean of replication. It was searching for Bluetooth-enabled devices in a 10m radius.
发现该病毒的主要特征是使用蓝牙协议传输文件的能力。 这是其唯一的复制手段。 它正在寻找半径为10m的蓝牙设备。
Upon finding such a device, it would send a transfer file request to the respective device. After receiving and executing the file, the second device would start searching for other devices to spread the Cabir virus further.
找到这样的设备后,它将向相应设备发送传输文件请求。 接收并执行文件后,第二台设备将开始搜索其他设备以进一步传播卡比尔病毒。
The initial version of Cabir had no negative effect on the devices, other than the battery drain caused by the constant Bluetooth search. It was not trying to steal credentials or money from the device owner as most of the malware is trying to do nowadays.
Cabir的初始版本对设备没有负面影响,除了持续不断的蓝牙搜索造成的电池消耗外。 如今,大多数恶意软件都在试图从设备所有者那里窃取凭证或金钱。
2.头骨²(2005) (2. Skulls² (2005))
Unlike Cabir, Skulls was a Trojan.
与Cabir不同, Skulls是特洛伊木马 。
Targeting Series 60, it was possible for it to be installed on some Series 80 devices as well. The risk of infection for the lattermost devices was low since these devices would get a prompt that this file is not intended for them.
针对60系列 ,也可以将其安装在某些80系列设备上。 最新的设备被感染的风险很低,因为这些设备会提示您该文件不适合他们使用。
After installation, Skulls overrode the device’s system application by creating new files with the same name in the same folder.
安装后,Skulls通过在同一文件夹中创建具有相同名称的新文件来覆盖设备的系统应用程序。
The new files contained no malicious code but the effect was destructive. The device’s only function left was making and answering calls. Every other application was not usable anymore.
新文件不包含恶意代码,但后果是破坏性的。 设备剩下的唯一功能是拨打和接听电话。 其他所有应用程序都不再可用。
All the application icons were replaced with an icon of a skull — hence the name Skulls.
所有应用程序图标都被替换为头骨图标,因此命名为Skulls 。
At that time, the Symbian OS was not well-documented. Malware developers had a hard time developing new attacks. Thus, the malware still had to be manually installed by the user. The attackers had to employ social engineering attacks to deceit the smartphone users into installing the Trojan.
当时,Symbian OS的文档不足。 恶意软件开发人员很难进行新的攻击。 因此,恶意软件仍然必须由用户手动安装。 攻击者必须进行社会工程 攻击,以欺骗智能手机用户安装特洛伊木马。
3.FakePlayer³(2010) (3. FakePlayer³ (2010))
In August 2010, the first wild Android malware was reported by Denis Maslennikov, an employee of Kaspersky³.
卡巴斯基³的员工Denis Maslennikov于2010年8月报告了第一个野生Android恶意软件。
Disguised in a media player application, FakePlayer was sending SMS messages at the numbers 3353 and 3354, with each message costing about $5.
FakePlayer伪装在媒体播放器应用程序中 ,正在以3353和3354的号码发送SMS消息 ,每条消息的成本约为5美元。
Similarly to the previous malware, FakePlayer had to be manually installed by the user.
与以前的恶意软件类似,用户必须手动安装FakePlayer。
The user was warned that this application is allowed to send SMS messages to premium numbers.
用户被警告该应用程序被允许将SMS消息发送到高级号码。
The application was named ’Media Player’ and came with a fake Microsoft Windows Media Player icon.
该应用程序名为“ Media Player ”,并带有假的Microsoft Windows Media Player图标。
After the malware was launched, it displayed a loading message in Russian. In background, it sent costly SMS messages to the premium numbers, unbeknown to the user.
恶意软件启动后,它以俄语显示加载消息。 在后台,它将昂贵的SMS消息发送给用户不知道的高级号码。
The application was rather simple. It was developed on top of the sample Hello World application provided by Google. The package name of the application was “org.me.androidapplication1” — the example package name for an Android application at that time.
该应用程序非常简单。 它是在Google提供的示例Hello World应用程序的基础上开发的。 该应用程序的软件包名称为“ org.me.androidapplication1” -当时的Android应用程序的示例软件包名称。
FakePlayer used a fairly simple mechanism that could be replicated by any beginner Android developer. Regardless of its simplicity, as with Cabir, it opened new horizons in the development of Android malware.
FakePlayer使用了一种相当简单的机制,任何初学者Android开发人员都可以复制该机制。 不管其简单性如何,与Cabir一样,它为Android恶意软件的开发开辟了新的视野。
4.HummingBad⁴(2016) (4. HummingBad⁴ (2016))
Six years later, in 2016, HummingBad was found in the wild.
六年后的2016年,在野外发现了HummingBad。
Created by the Chinese advertising company Yingmob, HummingBad generated revenue for the aforementioned company by automatically clicking on intrusive ads.
由中国广告公司Yingmob创建的HummingBad通过自动点击侵入性广告为前述公司创造收入。
Five months after its first discovery, in July 2016, a multinational IT security company, called Check Point, released a report⁴ containing data about the HummingBad malware.
在首次发现五个月后,一家名为Check Point的跨国IT安全公司发布了一份报告⁴,其中包含有关HummingBad恶意软件的数据。
Not only did HummingBad displayed ads and simulated clicks on them, but it also installed fraudulent applications on the infected device. We can see that this malware was extremely complex in regard to its functionalities.
HummingBad不仅展示了广告并模拟了 广告的 点击 ,而且还在受感染的设备上安装了欺诈性应用程序 。 我们可以看到,该恶意软件在功能方面极为复杂。
The service responsible for the advertisement networks used by the apps is called Se.
负责应用程序使用的广告网络的服务称为Se 。
A broadcast receiver is registered when the malware is installed. This broadcast receiver listens for the following events:
安装恶意软件后,将注册一个广播接收器。 该广播接收器侦听以下事件:
USER PRESENT — triggers when the device is unlocked
USER PRESENT-解锁设备时触发
BOOT COMPLETED — triggers once after the user finished booting
引导完成-用户完成引导后触发一次
SCREEN ON — triggers when the device wakes up and becomes interactive
SCREEN ON ( 屏幕打开) —在设备唤醒并变为互动状态时触发
When any of the previously mentioned events is received by the broadcast receiver, the Se service is started.
当广播接收机接收到任何前面提到的事件时,Se服务就会启动。
When an advertisement is shown, the process captures the KeyDownEvent event and doesn’t dispatch it further if the key code is one of:
显示广告时,如果关键代码为以下之一,则该过程将捕获KeyDownEvent事件,并且不会进一步分派该事件:
KEYCODE HOME (3)
KEYCODE HOME (3)
KEYCODE BACK (4)
按键返回 (4)
KEYCODE MENU (82)
键盘菜单 (82)
Without being able to use the navigation controls, the user is forced to process the advertisement.
在无法使用导航控件的情况下,用户被迫处理广告。
However, if the user tries to close the advertisement, the click event is intercepted and a click event in the middle of the screen is dispatched instead.
但是,如果用户尝试关闭广告,则会拦截click事件,而将分派屏幕中间的click事件。
A pattern emerged from the plethora of mobile malware that were found in the wild.
从野外发现的大量移动恶意软件中发现了一种模式 。
The user is warned.
警告用户。
Since the majority of mobile malware are Trojans, and not real viruses, the user has to “accept” the malware.
由于大多数移动恶意软件是特洛伊木马,而不是真正的病毒,因此用户必须“ 接受 ”恶意软件。
As we’ve already seen, the user is warned by Android that the application can be harmful. This means that attackers have to come up with a convincing story to support their attack.
正如我们已经看到的,Android向用户警告该应用程序可能有害。 这意味着攻击者必须想出令人信服的故事来支持他们的攻击。
In the Android ecosystem, the user is the primary vulnerability.
在Android生态系统中,用户是主要漏洞。
In the next part, we will see why do attackers choose to exploit the user, and not the operating system itself.
在下一部分中,我们将看到攻击者为什么选择利用用户 ,而不是操作系统本身。
[1] Eugene Kaspersky. 10 years since the first smartphone malware — to the day. https://eugene.kaspersky.com/2014/06/15/10-years-since-the-first-smartphone-malware-to-the-minute/
[1]尤金·卡巴斯基。 自第一款智能手机恶意软件发生至今已有10年。 https://eugene.kaspersky.com/2014/06/15/10-years-since-the-first-smartphone-malware-to-the-minute/
[2] Alexandre Gostev. Mobile Malware Evolution: An Overview, Part 1. https://securelist.com/mobile-malware-evolution-an-overview-part-1/36109/
[2] Alexandre Gostev。 移动恶意软件演进:概述,第1部分。https://securelist.com/mobile-malware-evolution-an-overview-part-1/36109/
[3] Denis Maslennikov. First SMS Trojan for Android. https://securelist.com/first-sms-trojan-for-android/29731/
[3] Denis Maslennikov。 首款适用于Android的SMS木马。 https://securelist.com/first-sms-trojan-for-android/29731/
[4] Check Point. From HummingBad to Worse. https://blog.checkpoint.com/wp-content/uploads/2016/07/HummingBad-Research-report_FINAL-62916.pdf
[4]检查点。 从HummingBad到更糟。 https://blog.checkpoint.com/wp-content/uploads/2016/07/HummingBad-Research-report_FINAL-62916.pdf
翻译自: https://proandroiddev.com/a-short-history-of-mobile-malware-296570ed5c1b
python简史
http://www.taodudu.cc/news/show-5066644.html
相关文章:
- Mac的恶意软件真的比较少吗?
- 计算机辅助教学设计,计算机辅助教学设计介绍
- 40主题制作代码———更新手机颜色十六进制代码
- python开发小工具项目_给中级Python开发者的13个练手项目,适合你不?
- Restorator 2018 v3.90汉化注册版 含注册码汉化激活教程
- 【渗透测试笔记】之【钓鱼姿势——exe伪装word文档(exe图标修改方法)】
- restorator无法打开exe
- exe 文件添加大尺寸图标
- 为 Cobalt Strike exe 木马添加图标
- Restorator 2005 v3.51 b1457
- Restorator 2007 3.70.1729
- restorator 运行后其他所有EXE文件都无法运行的解决方案
- restorator安装后接口问题解决
- 手动修改Restorator源文件告别繁琐:
- Restorator破解版下载
- 介绍linux上两种rootkits检测工具: Rootkit Hunter和Chkrootkit
- 看看这篇U盘防毒的文章吧,希望对你有用。
- Wsyscheck20080204(V1.68.32) by wangsea
- Wsyscheck20080122(V1.68.21)
- 【转】MFC隐藏进程自身(任务管理器不可见,wSysCheck等工具可见)
- 三两行代码实现进程防杀,免驱动,IceSword,WSysCheck等无效.
- Wsyscheck20080126(V1.68.24)
- 【平民系列教程】强悍的杀毒辅助软件Wsyscheck—没用过包你肠子都悔青了
- Wsyscheck 20080116
- Wsyscheck(系统检测维护工具) v1.68.33绿色版
- Wsyscheck 20080201
- Wsyscheck使用说明
- 实验五:系统检测维护工具Wsycheck使用
- ffmpeg为mkv封装格式的音视频文件添加内挂字幕
- 小尺寸android手机,索尼Z5 Compact:好的小尺寸Android手机
python简史_移动恶意软件简史相关推荐
- python简史_命令行简史
python简史 by Gitter 通过吉特 命令行简史 (A Brief History of the Command Line) This post by Andy Trevorah, Engi ...
- 云计算简史_云计算知识简史
围绕云计算相关的技术领域.技术名词和技术产品令人眼花缭乱.在云计算发端之初,应用开发环境和过去还没有本质不同:这当中也包括一个超级大用户"奈飞"(Netflix),他们的下行流量占 ...
- python ui bs_Guibs的Python学习_列表
Guibs 的 Python学习_列表# 列表# 列表由一系列按特定顺序排列的元素组成, 其中元素和元素之间可以没有任何关系 # 在 Python 中, 用方括号 [] 来表示列表, 并用逗号 , 分 ...
- Python 进阶_生成器 生成器表达式
目录 目录 相关知识点 生成器 生成器 fab 的执行过程 生成器和迭代器的区别 生成器的优势 加强的生成器特性 生成器表达式 生成器表达式样例 小结 相关知识点 Python 进阶_迭代器 & ...
- python基础_格式化输出(%用法和format用法)(转载)
python基础_格式化输出(%用法和format用法) 目录 %用法 format用法 %用法 1.整数的输出 %o -- oct 八进制 %d -- dec 十进制 %x -- hex 十六进制 ...
- python判断题题库大数据技术_智慧树_大数据分析的python基础_搜题公众号
智慧树_大数据分析的python基础_搜题公众号 更多相关问题 社会公众可以查阅烟草专卖行政主管部门的监督检查记录.() 公民.法人或者其他组织不得利用自动售货机销售烟草制品.() 烟草广告中不得有下 ...
- python 切片_全面解读Python高级特性切片
大家好,欢迎来到Crossin的编程教室! 众所周知,我们可以通过索引值(或称下标)来查找序列类型(如字符串.列表.元组-)中的单个元素,那么,如果要获取一个索引区间的元素该怎么办呢? 切片(slic ...
- python爬虫_网易音乐歌单
小白flag7 python爬虫_网易音乐歌单 准备 import os #存放文件处理 import time #程序运行时间计算 import sys #错误信息返回 预留 from seleni ...
- Python基础_第2章_Python运算符与if结构
Python基础_第2章_Python运算符与if结构 文章目录 Python基础_第2章_Python运算符与if结构 Day02之`Python运算符与if结构` 一.昨日回顾 1.回顾昨天的课程 ...
最新文章
- DeepLearning 应用概述
- android ui篇
- hibernate更新部分字段的几种方法
- linux vector 头文件,LINUX 之Vector用法
- Android逆向笔记-大部分内购游戏破解思路
- MySQL_JDBC_数据库连接池
- 开发中为组件添加预览信息
- h5分线程Worker
- linux程序内存布局,关于Linux中程序的内存布局
- Hive_Hive的数据模型_分区表
- JPEG库在Linux系统下的编译和移植【转】
- python基础教程 pdf github_GitHub - looly/python-basic: 老齐(qiwsir)的Python基础教程Gitbook版...
- Oracle创建用户与授予表空间与权限
- 淘宝美工掌握这4种能力,不逊色于UI设计师
- 关于STM32F105 双CAN口通信的一些学习心得
- Web课程设计——小米商城页面实战(html,css,js实现)
- 你的生活布满了网络爬虫
- SSRF - ctfhub -2【FastCGI协议、Redis协议、URL Bypass、数字IP Bypass、302跳转 Bypass、DNS重绑定Bypass】
- python从txt导入数据到CSV文件末尾行丢失
- 经典力学、相对论、量子力学
