美团机器学习实践 密码_机器学习遇到密码学的地方
美团机器学习实践 密码
When reading this, chances are that you know one or another thing about machine learning already. You know that machine learning algorithms typically take in a bunch of samples, each containing a fixed amount of features, and output a prediction in the end.
阅读本文时,您很有可能已经对机器学习有所了解。 您知道机器学习算法通常会吸收一堆样本,每个样本都包含固定数量的特征,最后输出预测 。
What you maybe have heard about (but did not dig deeper into) is the field of cryptography. It is this mysterious subject where it’s all security, passwords, hiding things. Maybe you have even heard about AES or RSA, which are algorithms to encrypt data.
您可能听说过(但没有更深入地研究) 加密领域。 这是一个神秘的主题,它包含所有安全性,密码和隐藏的内容。 也许您甚至听说过AES或RSA ,它们是加密数据的算法。
But don’t worry, even if you have never dealt with cryptography before, you will be able to follow along since I will explain everything on an introductory level .
但是不用担心,即使您以前从未处理过加密技术,也可以继续学习,因为我将在入门级进行解释。
In this article, I want to bring both fields together. I will present to you an easy to understand, yet hard to solve problem used to build cryptographic algorithms — the so-called Learning Parity with Noise problem, LPN for short. The “L” in LPN should ring your machine learning alarm bells already because this problem can be seen as a routine machine learning problem!
在本文中,我想将这两个领域结合在一起。 我将向您介绍一个易于理解但难以解决的用于构建密码算法的问题,即所谓的“ 学习带有噪声的奇偶性”问题,简称LPN 。 LPN中的“ L”应该已经响起了您的机器学习警报,因为这个问题可以看作是例行的机器学习问题!
But first, let us see where the LPN problem naturally arises in a cryptographic setting and how to define it. We will solve the LPN problem by using machine learning afterward.
但是首先,让我们看看在密码设置中LPN问题自然产生的位置以及如何定义它。 之后,我们将通过机器学习来解决LPN问题。
动机 (Motivation)
Imagine that you own a hotel and you want to manage access to the guests’ rooms, i.e. each guest should only be able to enter their own room. Makes sense, right?
想象一下,您拥有一家酒店,并且想要管理对客人房间的访问,即每个客人只能进入自己的房间。 有道理吧?
Now, traditionally you could use normal, physical keys. The disadvantage is that people sometimes lose their keys, which means a lot of costs for your business since you have to replace the lock from the affected doors.
现在,传统上您可以使用普通的物理键。 缺点是人们有时会丢失他们的钥匙,这意味着您必须为受影响的门更换锁,这对您的企业来说是很大的成本。
So you decide on deploying smart cards, in particular cards with RFID (radio-frequency identification) chips, and also the corresponding locks. Since you have to provide for a lot of doors and you want to save money, you choose very weak RFID chips, i.e. chips with diminishing computational power, maybe even without its own source of electricity.
因此,您决定部署智能卡,尤其是带有RFID(射频识别)的卡 芯片,以及相应的锁。 由于必须提供大量的门并且要节省资金,因此您选择了非常弱的RFID芯片 ,即计算能力降低的芯片,甚至可能没有自己的电源。

The way your system should work is the following: Every lock and every card has a secret key stored, a binary vector such as s=(1,0,1,0), just much longer in practice. If you hold your card next to a lock, the lock works as a reader, scanning the card’s secret key. The chip is called a tag in this context.
系统的工作方式如下:每个锁和每张卡都存储有一个秘密密钥 ,一个二进制向量,例如s = (1,0,1,0), 实际上要长得多 。 如果您将卡放在锁旁边,则该锁将用作读取器 ,扫描卡的密钥。 在这种情况下,该芯片称为标签 。
The clue: If the secret keys of the card and the door match, the door opens.
提示:如果卡的密码和门的密钥匹配,则门将打开。
Perfect! But how to do it? Well, an easy way is to hold your card next to the lock and the lock tells the chip on the card to send its secret key to the lock. Then the lock checks if both secret keys are equal and open the door, if yes.
完善! 但是怎么做呢? 好吧,一种简单的方法是将您的卡放在锁旁边,锁告诉卡上的芯片将其秘密密钥发送到锁。 然后,锁检查两个秘密钥匙是否相等,如果是,则打开门。

This makes sense, because if you do not have the correct card, i.e. the secret key on your chip is different from the secret key in the door lock, the door will not open.
这是有道理的,因为如果您没有正确的卡,即芯片上的密钥与门锁中的密钥不同,则门将无法打开。
问题 (The Problem)
The trouble with this solution begins when a guest wants to enter their room: A bad guy, usually called an attacker in cryptography, could sit in the hallway, apparently just typing innocently on their notebook. What the attacker actually does is sniffing the RFID traffic, i.e. reading the communication between the lock and the guest’s chip. If the chip sends the secret key directly, the attacker will see it, store it, forge a card containing this key and then will be able to enter the room.
这种解决方案的麻烦始于客人要进入房间时:一个通常被称为密码学攻击者的坏人可能坐在走廊上,显然只是在他们的笔记本上无辜地打字。 攻击者实际上所做的是嗅探 RFID流量,即读取锁和访客芯片之间的通信。 如果芯片直接发送密钥,攻击者将看到它,将其存储,伪造一张包含该密钥的卡,然后便可以进入房间。
So, this is a bad idea. It only works if there are no bad people in the world (highly unlikely). Instead, we have to arm ourselves and improve security for our guests. The idea is the following:
因此,这是一个坏主意。 它仅在世界上没有坏人的情况下才有效(极不可能)。 相反,我们必须武装自己并提高客人的安全性。 这个想法如下:
The chip somehow has to prove to the lock that it possesses the correct secret key without revealing it.
芯片必须以某种方式向锁证明它拥有正确的秘密密钥而不泄露它。
I hear you scream: That’s what encryption is for! And you are right. The attacker would only see garbage in the sniffing tool and wouldn’t be able to reconstruct the key. But sadly, the RFID chip is much too weak for encrypting anything because you wanted to save money, remember? Sadly, this is also true for bigger companies in the real world. The chip has nearly no computational power and also only barely enough storage for its secret key. So we need another, more light-weight solution.
我听到你在尖叫: 这就是加密的目的! 你是对的。 攻击者只会在嗅探工具中看到垃圾,而无法重构密钥。 但是可悲的是,RFID芯片太弱了,无法加密任何东西,因为您想省钱,还记得吗? 可悲的是,对于现实世界中的大型公司而言,情况也是如此。 该芯片几乎没有计算能力,也几乎没有足够的存储空间来存储其密钥。 因此,我们需要另一个更轻便的解决方案。
One way to do that is to use a cryptographic protocol like the HB Protocol by Hopper and Blum [1]. This protocol makes it difficult for this attacker to extract the key.
一种方法是使用像Hopper和Blum [1]的HB Protocol这样的加密协议。 该协议使攻击者很难提取密钥。
The vanilla HB Protocol that I am going to introduce has other vulnerabilities and should not be used in practice. I just use because it is easy to explain. For real-world security, more secure extensions of this protocol or other secure protocols should be used.
我将要介绍的香草HB协议还有其他漏洞,不应在实践中使用。 我使用它是因为它很容易解释。 为了实现真实世界的安全性,应使用此协议或其他安全协议的更安全的扩展。
HB协议 (HB Protocol)
So, you have a reader R (the lock) and a tag T (your chip). T now wants to prove to R that it possesses the same secret key without revealing it. This is done by R repeatedly challenging T with questions only a tag with the correct secret key can answer. So far, we have seen that the single question “What is your secret key?” is insecure since this reveals too much information already. Instead, in the HB Protocol T is asked to only reveal small portions of the secret one tiny bit at a time, until R can be sure that T has the correct secret key.
因此,您有一个读取器R (锁)和标签T (您的芯片)。 T现在想向R证明它拥有相同的秘密密钥而没有透露它。 这是通过R反复向T提出问题来挑战T的 ,只有具有正确密钥的标签才能回答。 到目前为止,我们已经看到了一个问题:“您的秘密密钥是什么?” 是不安全的,因为这已经暴露了太多信息。 取而代之的是,在HB协议中,要求T一次仅透露一小部分秘密的一小部分,直到R可以确定T具有正确的秘密密钥为止。
Imagine that the secret keys of R and T are in fact both the same s=(1,0,1,0). Now R sends a random binary vector a (e.g. a=(1,0,1,1)) to T and expects T to respond back to it the scalar product b=<a, s>, which is
想象一下, R和T的秘密密钥实际上都是相同的s =(1,0,1,0)。 现在R发出一个随机二进制矢量 (例如,=(1,0,1,1))到T,我们期望吨至响应回到它的标量积B = <A,S>,这是
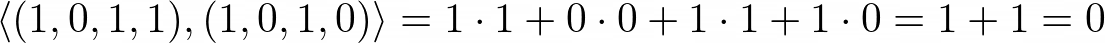
in this example. We call this a a challenge. Remember, we deal with bit arithmetic here, so the “+” is, in fact, an XOR. The multiplication is the same as in the real numbers. Or for mathematicians: we calculate in the field GF(2) or
美团机器学习实践 密码_机器学习遇到密码学的地方相关推荐
- 机器学习 凝聚态物理_机器学习遇到了凝聚的问题
机器学习 凝聚态物理 为什么要机器学习? (Why machine learning?) Machine learning is one of today's most rapidly cutting ...
- 机器学习模型 非线性模型_机器学习:通过预测菲亚特500的价格来观察线性模型的工作原理...
机器学习模型 非线性模型 Introduction 介绍 In this article, I'd like to speak about linear models by introducing y ...
- 机器学习导论�_机器学习导论
机器学习导论� Say you are practising basketball on your own and you are trying to shoot the ball into the ...
- 机器学习偏差方差_机器学习101 —偏差方差难题
机器学习偏差方差 Determining the performance of our model is one of the most crucial steps in the machine le ...
- 机器学习系列(4)_机器学习算法一览,应用建议与解决思路
作者:寒小阳 时间:2016年1月. 出处:http://blog.csdn.net/han_xiaoyang/article/details/50469334 声明:版权所有,转载请联系作者并注明出 ...
- 机器学习系列(7)_机器学习路线图(附资料)
作者:寒小阳&&龙心尘 时间:2016年2月. 出处:http://blog.csdn.net/han_xiaoyang/article/details/50759472 http:/ ...
- (转)机器学习系列(7)_机器学习路线图(附资料)
作者:寒小阳&&龙心尘 时间:2016年2月. 出处:http://blog.csdn.net/han_xiaoyang/article/details/50759472 http:/ ...
- 机器学习系列(9)_机器学习算法一览(附Python和R代码)
转载自:http://blog.csdn.net/longxinchen_ml/article/details/51192086 – 谷歌的无人车和机器人得到了很多关注,但我们真正的未来却在于能够使电 ...
- 转机器学习系列(9)_机器学习算法一览(附Python和R代码)
转自http://blog.csdn.net/han_xiaoyang/article/details/51191386 – 谷歌的无人车和机器人得到了很多关注,但我们真正的未来却在于能够使电脑变得更 ...
最新文章
- Win2003 安全设置大全
- matlab里面板有什么作用,MATLAB轻松享受GPU的强大功能
- 巧用Win2003负载平衡服务实现LCS2005企业版的部署:LCS2005系列之五
- bootstrap4 左侧导航栏 优秀 大气_Axure导出html没有左侧菜单栏(导航栏)?——Mac Safari...
- 【C语言笔记进阶篇】第一章:指针进阶
- 初识MyBatis-Plus
- RTL8201EL介绍
- ZetCode Spring 教程
- 专访iQOO Pro产品经理:以更好的产品 更低的价格推进5G生态普及
- 揭秘计算机之间互发数据的关键原理!
- android 应用使用Root权限执行linux命令
- .net core EF Core 调用存储过程
- 图片标注工具LabelImg
- leetcode 5724. 绝对差值和
- 域名转入阿里云操作说明
- 安卓图片三级缓存策略与实现
- 路由器刷openwrt后不能上网 修改brlan的ip地址失败
- 卫生专业计算机考试,快熟悉一下2019卫生专业技术资格考试人机对话系统
- basler恢复出厂设置_实现图像实时采集(使用BaslerSDK)-C
- 给黑白照片上色软件神器
