18.1 集群介绍 18.2 keepalived介绍 18.3/18.4/18.5 用keepalived配置高可用集群
2019独角兽企业重金招聘Python工程师标准>>> 
第十八章 Linux集群
18.1 集群介绍
Linux集群根据功能划分为两大类:高可用和负载均衡。
高可用集群
高可用集群通常为2台服务器,一台工作,另一台作为冗余,当提供服务的机器宕机时,冗余将接替继续提供服务。
实现高可用的开源软件有:heartbeat、Keepalived,其中heartbeat已无人维护,所以今后使用Keepalived来搭建高可用集群。
负载均衡集群
负载均衡集群,需要有1台服务器作为分发器,它负责把用户的请求分发给后端的服务器处理,在这个集群里,除了分发器外就是给用户提供服务的服务器了,这些服务器数量至少为2台,所以负载均衡集群至少要3台服务器。
实现负载均衡的开源软件有:LVS、Keepalived、haproxy、nginx;商业软件有:F5、Netscaler。
18.2 Keepalived介绍
Keepalived通过VRRP(virtual router redundancy protocol)虚拟路由冗余协议来实现高可用。
在这个协议里会将多台功能相同的路由器组成一个小组,这个小组会有1个master角色和N(N≥1)个backup角色。
Keepalived有三个模块:core、check、vrrp。其中core模块为Keepalived的核心,负责主进程的启动、维护以及全局配置文件的加载和解析;check模块负责健康检查,vrrp负责实现vrrp协议。
18.3-18.5 用Keepalived配置高可用集群(上)
操作环境:
两台虚拟机:
master:192.168.230.135;
backup:192.168.230.145;
准备工作
master:
[root@cham002 ~]# yum install -y keepalived[root@cham002 ~]# /usr/local/nginx/sbin/nginx -v
nginx version: nginx/1.12.1
backup:
[root@test ~]# yum install -y keepalived[root@test ~]# yum install -y nginx[root@test ~]# nginx -v
nginx version: nginx/1.12.2
开始配置
配置master机器:
在此使用自定义的Keepalived配置文件脚本(先清空或删除自带配置文件脚本)。
[root@cham002 ~]# vim /etc/keepalived/keepalived.conf
global_defs {notification_email {aming@aminglinux.com } #定义故障提醒邮件接收地址(本实验用不到)notification_email_from root@aminglinux.comsmtp_server 127.0.0.1smtp_connect_timeout 30 router_id LVS_DEVEL #定义故障提醒邮件发送地址(本实验用不到)
}
vrrp_script chk_nginx { #定义监控脚本script "/usr/local/sbin/check_ng.sh" #指定服务健康检测(check)脚本interval 3 #检测时间间隔
}
vrrp_instance VI_1 { state MASTER #定义该服务的角色 interface ens33 #定义在本机中监听VIP的网卡virtual_router_id 51 #虚拟路由id(同组中的服务器保持该id一致)priority 100 #指定本机权重(决定优先级)advert_int 1 authentication { #定义认证相关信息 auth_type PASS #认证类型为密码形式auth_pass 123456 #定义认证密码}virtual_ipaddress { #定义VIP192.168.230.100}track_script { #加载监控服务(脚本)chk_nginx #注意此处服务名称要与上面监控脚本名称一致}
}创建监控脚本:
[root@cham002 ~]# vim /usr/local/sbin/check_ng.sh#!/bin/bash
#时间变量,用于记录日志
d=`date --date today +%Y%m%d_%H:%M:%S`
#计算nginx进程数量
n=`ps -C nginx --no-heading|wc -l`
#如果进程为0,则启动nginx,并且再次检测nginx进程数量,
#如果还为0,说明nginx无法启动,此时需要关闭keepalived
if [ $n -eq "0" ]; then/etc/init.d/nginx startn2=`ps -C nginx --no-heading|wc -l`if [ $n2 -eq "0" ]; thenecho "$d nginx down,keepalived will stop" >> /var/log/check_ng.logsystemctl stop keepalived #在此停止Keepalived服务是为了避免发生脑裂fi
fi更改脚本权限:
[root@cham002 ~]# chmod 755 !$
chmod 755 /usr/local/sbin/check_ng.sh
启动Keepalived服务:
[root@cham002 ~]# systemctl start keepalived
检测服务状态:
[root@cham002 ~]# ps aux |grep keep
root 4915 0.0 0.1 120720 1400 ? Ss 18:51 0:00 /usr/sbin/keepalived -D
root 4916 0.0 0.3 127460 3276 ? S 18:51 0:00 /usr/sbin/keepalived -D
root 4917 0.0 0.2 131656 3024 ? S 18:51 0:00 /usr/sbin/keepalived -D
root 4966 0.0 0.0 112680 976 pts/1 S+ 18:52 0:00 grep --color=auto keep
[root@cham002 ~]# ps aux |grep nginx
root 2302 0.0 0.2 46840 2956 ? Ss 01:08 0:00 nginx: master process /usr/local/nginx/sbin/nginx -c /usr/local/nginx/conf/nginx.conf
nobody 4763 0.0 0.4 48764 4164 ? S 18:25 0:00 nginx: worker process
nobody 4764 0.0 0.4 48764 4164 ? S 18:25 0:00 nginx: worker process
root 4986 0.0 0.0 112684 976 pts/1 S+ 18:52 0:00 grep --color=auto nginx
[root@cham002 ~]# date
2018年 01月 24日 星期三 18:54:09 CST
注:由以上检测状态可知关闭nginx服务之后Keepalived会再次自动启动nginx服务[root@cham002 ~]# /etc/init.d/nginx stop
Stopping nginx (via systemctl): [ 确定 ]
[root@cham002 ~]# !ps
ps aux |grep nginx
root 2302 0.0 0.2 46840 2956 ? Ss 01:08 0:00 nginx: master process /usr/local/nginx/sbin/nginx -c /usr/local/nginx/conf/nginx.conf
nobody 4763 0.0 0.4 48764 4164 ? S 18:25 0:00 nginx: worker process
nobody 4764 0.0 0.4 48764 4164 ? S 18:25 0:00 nginx: worker process
root 5175 0.0 0.0 112684 976 pts/1 S+ 18:53 0:00 grep --color=auto nginx
注:由以上检测状态可知关闭nginx服务之后Keepalived会再次自动启动nginx服务说明: “脑裂”,即当master宕机后仍然未释放VIP,同时backup接替master提供服务要使用同一VIP,因而导致两台机器争占同一VIP导致服务紊乱,所以当master宕机后需要关闭其Keepalived服务来避免脑裂现象发生。Keepalived服务的日志位置:/var/log/messages。
查看网卡信息:
[root@cham002 ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:b6:9f:e3 brd ff:ff:ff:ff:ff:ffinet 192.168.230.135/24 brd 192.168.230.255 scope global ens33valid_lft forever preferred_lft foreverinet 192.168.188.100/32 scope global ens33valid_lft forever preferred_lft foreverinet 192.168.230.150/24 brd 192.168.230.255 scope global secondary ens33:0valid_lft forever preferred_lft foreverinet6 fe80::6f15:52d3:ebeb:e193/64 scope link valid_lft forever preferred_lft forever
3: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:b6:9f:ed brd ff:ff:ff:ff:ff:ffinet 192.168.100.1/24 brd 192.168.100.255 scope global ens37valid_lft forever preferred_lft foreverinet6 fe80::1801:cbbb:ebcc:89a3/64 scope link valid_lft forever preferred_lft forever
说明: 在此不能使用ifconfig查看,ens33中增加了一个IP:192.168.188.100/32。
检查防火墙
[root@cham002 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination
[root@cham002 ~]# getenforce
Disabled
配置backup机器:
检查防火墙
[root@test ~]# systemctl stop firewalld
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 92 packets, 6136 bytes)pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 50 packets, 5200 bytes)pkts bytes target prot opt in out source destination
[root@test ~]# setenforce 0
[root@test ~]# getenforce
Permissive
配置Keepalived:
同样使用自定义脚本。
[root@test ~]# vim /etc/keepalived/keepalived.conf
global_defs {notification_email {aming@aminglinux.com}notification_email_from root@aminglinux.comsmtp_server 127.0.0.1smtp_connect_timeout 30router_id LVS_DEVEL
}
vrrp_script chk_nginx {script "/usr/local/sbin/check_ng.sh"interval 3
}
vrrp_instance VI_1 { #只有该部分与master有区别state BACKUP #角色interface ens33 virtual_router_id 51 priority 90 #权重advert_int 1authentication {auth_type PASSauth_pass 123456}virtual_ipaddress {192.168.230.100} track_script {chk_nginx}
} 说明: 如果是多台服务器,权重决定了master宕机后,backup接管master角色的顺序。
创建监控脚本:
[root@test ~]# vim /usr/local/sbin/check_ng.sh#时间变量,用于记录日志
d=`date --date today +%Y%m%d_%H:%M:%S`
#计算nginx进程数量
n=`ps -C nginx --no-heading|wc -l`
#如果进程为0,则启动nginx,并且再次检测nginx进程数量,
#如果还为0,说明nginx无法启动,此时需要关闭keepalived
if [ $n -eq "0" ]; thensystemctl start nginxn2=`ps -C nginx --no-heading|wc -l`if [ $n2 -eq "0" ]; thenecho "$d nginx down,keepalived will stop" >> /var/log/check_ng.logsystemctl stop keepalivedfi
fi
~
[root@test ~]# chmod 755 !$
chmod 755 /usr/local/sbin/check_ng.sh
说明: 该检测脚本中与master检测脚本的区别在于:systemctl start nginx,即nginx的启动方式,因为在backup服务器中是使用yum安装的nginx,默认添加到系统服务中。
[root@test ~]# systemctl start keepalived
[root@test ~]# ps aux |grep keep
root 10695 0.0 0.1 120704 1396 ? Ss 20:19 0:00 /usr/sbin/keepalived -D
root 10696 0.0 0.3 127444 3260 ? S 20:19 0:00 /usr/sbin/keepalived -D
root 10697 0.0 0.2 131640 2840 ? S 20:19 0:00 /usr/sbin/keepalived -D
root 10728 0.0 0.0 112664 968 pts/1 R+ 20:19 0:00 grep --color=auto keep
测试
宕机前
master:
[root@cham002 ~]# cat /usr/local/nginx/conf/vhost/aaa.com.conf
server
{listen 80 default_server; server_name aaa.com;index index.html index.htm index.php;root /data/wwwroot/default;location ~ \.php${include fastcgi_params;fastcgi_pass unix:/tmp/champ.sock;#fastcgi_pass 127.0.0.1:9000;fastcgi_index index.php;fastcgi_param SCRIPT_FILENAME /data/wwwroot/default$fastcgi_script_name;}}[root@cham002 ~]# cat /data/wwwroot/default/index.html
This is the default sete.
[root@cham002 ~]# vim /data/wwwroot/default/index.html
master This is the default sete.
[root@cham002 ~]#
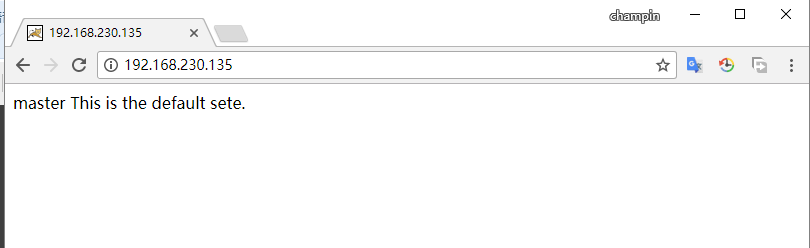
backup:
[root@test ~]# cat /usr/share/nginx/html/index.html
[root@test ~]# vim /usr/share/nginx/html/index.html
backup backup.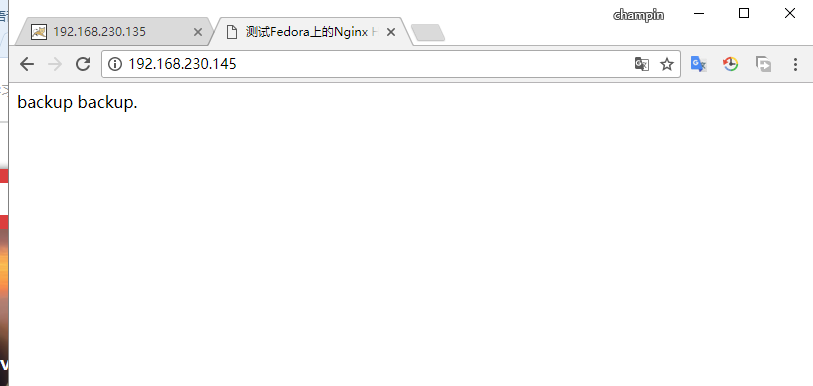
使用VIP访问:
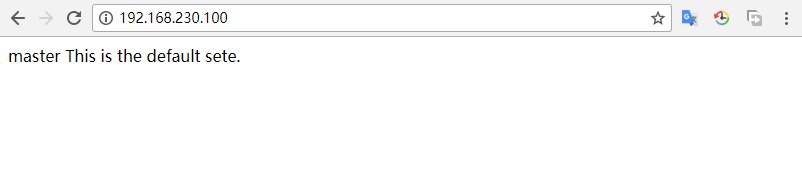
此时默认访问到master服务器。
master宕机后:
[root@cham002 ~]# systemctl stop keepalived
[root@cham002 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:b6:9f:e3 brd ff:ff:ff:ff:ff:ffinet 192.168.230.135/24 brd 192.168.230.255 scope global ens33valid_lft forever preferred_lft foreverinet 192.168.230.150/24 brd 192.168.230.255 scope global secondary ens33:0valid_lft forever preferred_lft foreverinet6 fe80::6f15:52d3:ebeb:e193/64 scope link valid_lft forever preferred_lft forever
3: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:b6:9f:ed brd ff:ff:ff:ff:ff:ffinet 192.168.100.1/24 brd 192.168.100.255 scope global ens37valid_lft forever preferred_lft foreverinet6 fe80::1801:cbbb:ebcc:89a3/64 scope link valid_lft forever preferred_lft forever
[root@cham002 ~]#
backup:
[root@test ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:50:f9:44 brd ff:ff:ff:ff:ff:ffinet 192.168.230.145/24 brd 192.168.230.255 scope global ens33valid_lft forever preferred_lft foreverinet 192.168.230.100/32 scope global ens33valid_lft forever preferred_lft foreverinet6 fe80::9b07:b28d:f5e9:d107/64 scope link valid_lft forever preferred_lft forever
[root@test ~]# tail /var/log/messages
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
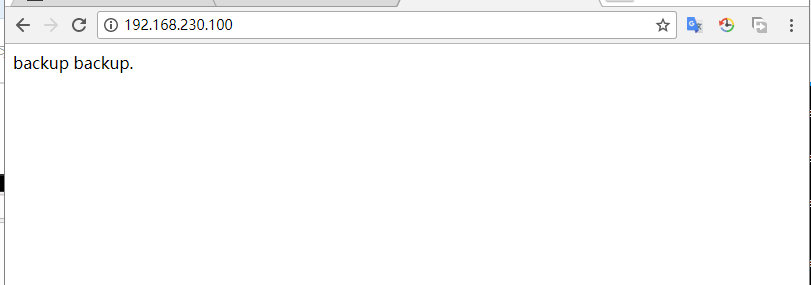
注: 恢复master上的Keepalived服务后,会由master服务器为该集群提供服务。如下:
[root@cham002 ~]# systemctl start keepalived
[root@cham002 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:b6:9f:e3 brd ff:ff:ff:ff:ff:ffinet 192.168.230.135/24 brd 192.168.230.255 scope global ens33valid_lft forever preferred_lft foreverinet 192.168.230.100/32 scope global ens33valid_lft forever preferred_lft foreverinet 192.168.230.150/24 brd 192.168.230.255 scope global secondary ens33:0valid_lft forever preferred_lft foreverinet6 fe80::6f15:52d3:ebeb:e193/64 scope link valid_lft forever preferred_lft forever
3: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:b6:9f:ed brd ff:ff:ff:ff:ff:ffinet 192.168.100.1/24 brd 192.168.100.255 scope global ens37valid_lft forever preferred_lft foreverinet6 fe80::1801:cbbb:ebcc:89a3/64 scope link
在看看日志变化
[root@test ~]# tail /var/log/messages
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
[root@test ~]# tail /var/log/messages
Jan 28 20:44:17 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:44:22 test Keepalived_vrrp[12877]: Sending gratuitous ARP on ens33 for 192.168.230.100
Jan 28 20:47:29 test Keepalived_vrrp[12877]: VRRP_Instance(VI_1) Received advert with higher priority 100, ours 90
Jan 28 20:47:29 test Keepalived_vrrp[12877]: VRRP_Instance(VI_1) Entering BACKUP STATE
Jan 28 20:47:29 test Keepalived_vrrp[12877]: VRRP_Instance(VI_1) removing protocol VIPs.
在生产环境中,可能会用到2-3台backup角色, vim /etc/keepalived/keepalived.conf
这里面的权重调成不通级别。权重越高优先级越高!除了nginx服务的话,还可以做MySQL的高可用集群服务。
转载于:https://my.oschina.net/u/3708120/blog/1614191
18.1 集群介绍 18.2 keepalived介绍 18.3/18.4/18.5 用keepalived配置高可用集群相关推荐
- 18.3/18.4/18.5 用keepalived配置高可用集群
2019独角兽企业重金招聘Python工程师标准>>> 用keepalived配置高可用集群 准备两台机器130和132,130作为master,132作为backup 两台机器都执 ...
- linux集群-keepalived介绍-用keepalived配置高可用集群
2019独角兽企业重金招聘Python工程师标准>>> linux集群介绍: 以功能划分:高可用和负载均衡 高可用集群:通常为两台服务器,一台工作,另外一台作为冗余.实现高可用的开源 ...
- 集群介绍 、keepalived介绍 、 用keepalived配置高可用集群
集群介绍 根据功能划分为两大类:高可用和负载均衡 高可用集群通常为两台服务器,一台工作,另外一台作为冗余,当提供服务的机器宕机,冗余将接替继续提供服务 实现高可用的开源软件有:heartbeat.ke ...
- 集群介绍+用keepalived配置高可用集群(总结)
1.集群介绍 根据功能划分为两大类:高可用和负载均衡 高可用集群通常为两台服务器,一台工作,另外一台作为冗余,当提供服务的机器宕机,冗余将接替继续提供服务 高可用集群,英文原文为High Availa ...
- 用keepalived配置高可用集群
2019独角兽企业重金招聘Python工程师标准>>> 一 集群介绍 1.概述 根据功能划分为两大类:高可用和负载均衡 高可用集群通常为两台服务器,一台工作,另外一台作为冗余,当提供 ...
- 采用ipvsadm管理工具,及Keepalived软件检测服务器的状态,搭建负载均衡的高可用集群
前言 ipvsadm是Linux虚拟服务器的管理命令,是用于设置.维护和检查Linux内核中虚拟服务器列表的命令.Linux虚拟服务器可用于基于两个或更多个节点的集群构建可扩展的网络服务.群集的活动节 ...
- keepalived配置高可用集群
准备工作 分别在主从上安装keepalived和nginx yum install -y keepalived yum install -y nginx 关闭主从上的防火墙和SELinux syste ...
- Nginx+Keepalived+Proxy_Cache 配置高可用集群和高速缓存
环境: CentOS release 6.5 x86_64 192.168.100.90 CentOS release 6.5 x86_64 192.168.100.91 在主备服务器上部 ...
- corosync+pacemaker+crmsh配置高可用集群。
实验环境: admin1.tuchao.com 192.168.18.100 ansible管理节点 admin2.tuchao.com 192.168.18.101 集群节点一 admin3.t ...
最新文章
- 活久见!谷歌开源“大杀器”,CV、NLP都能用!
- java opennlp_使用opennlp进行文档分类
- C#中的委托和事件 (7)---总结
- bzoj4636: 蒟蒻的数列
- mysql 数据操作,MySQL-数据操作
- win10安装python的xlrd_win10安装python的xlrd
- 越烧钱越上瘾,年轻人为何沉迷「白色鸦片」?
- php 位运算 负数,php的位运算详解
- 开公司的两个方向,要么把公司开成很赚钱,要么把公司做成很值钱
- 设置元素的高度为百分比,结果不起作用的解决方法
- 传智播客Java 关键字,标识符,注释
- 毕设题目:Matlab图像修复
- 二进制文件与文本文件详解
- 图像列表控制(CImageList)
- 解决:Please either set ERLANG_HOME to point to your Erlang installation or place the RabbitMQ server d
- K8S 1.23 metrics-server及cadvisor 杂记
- (最全干货分享)渗透测试全流程归纳总结之四
- Unity 读取本地文件夹图片
- Lambda表达式比较foreach使用
- FPGA、集创赛记录
