mail安全性与加密
邮件系统的安全性通过两个方面:
第一方面:发送与接收(通过协议进行加密)
发送加密(点对点):
通过协议smtp与ssl的结合——》smtps
smtps:
1:使用965端口(smtps)
2:利用25端口直接进行加密:stmp+ssl(即starttls)
查看编译时是否支持starttls
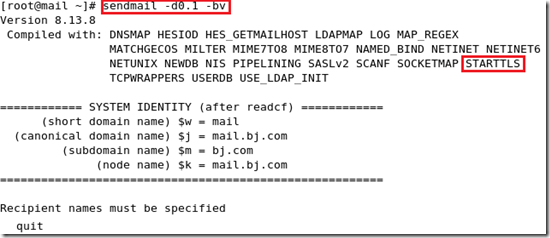
查看在编译时是否加密:
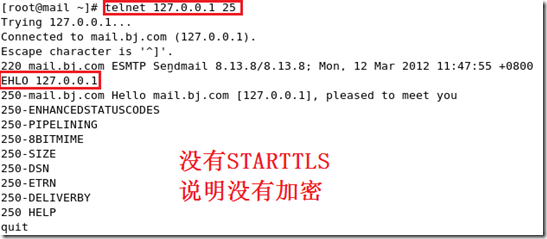
3:(端对端)在ftp上与第三方工具(gpg)进行加密。(即s/mime)
接收加密:
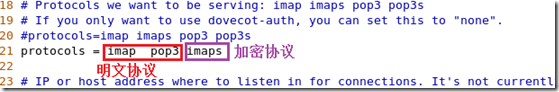
通过协议pop2/3与ssl的结合——》pops
通过协议imap与ssl的结合——》imaps
第二方面:身份验证
启动STARTTLS进行加密:
编译制作颁发机构
[root@mail ~]# cd /etc/pki/
[root@mail pki]# ll
total 36
drwx------ 3 root root 4096 Feb 9 00:16 CA
drwxr-xr-x 4 root root 4096 Mar 20 10:27 dovecot
drwxr-xr-x 2 root root 4096 Feb 9 00:15 nssdb
drwxr-xr-x 2 root root 4096 Feb 9 00:15 rpm-gpg
drwxr-xr-x 5 root root 4096 Mar 20 19:37 tls
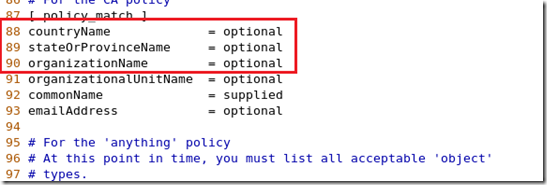
[root@mail pki]# vim tls/openssl.cnf 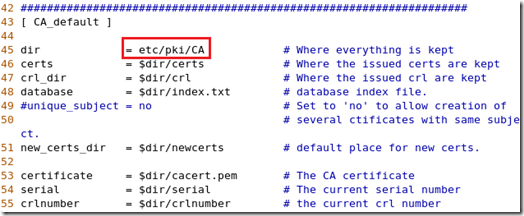
[root@mail pki]# cd CA 切换到CA目录
[root@mail CA]# mkdir certs crl newcerts 创建3个目录
[root@mailt CA]# touch index.txt serial 创建2个文档
[root@mail CA]# echo "01" >serial 赋予serial序列号
[root@mail CA]# ll 查看
total 24
drwxr-xr-x 2 root root 4096 Mar 20 20:08 certs
drwxr-xr-x 2 root root 4096 Mar 20 20:08 crl
-rw-r--r-- 1 root root 0 Mar 20 20:08 index.txt
drwxr-xr-x 2 root root 4096 Mar 20 20:08 newcerts
drwx------ 2 root root 4096 Jun 30 2009 private
-rw-r--r-- 1 root root 3 Mar 20 20:09 serial
创建私钥:
[root@mail CA]# openssl genrsa 1024 >private/cakey.pem
Generating RSA private key, 1024 bit long modulus
..........++++++
.++++++
e is 65537 (0x10001)
创建营业执照:
[root@mail CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:BEIJING
Locality Name (eg, city) [Newbury]:BEIJING
Organization Name (eg, company) [My Company Ltd]:SECCENTER
Organizational Unit Name (eg, section) []:tec
Common Name (eg, your name or your server's hostname) []:rootca.net.net
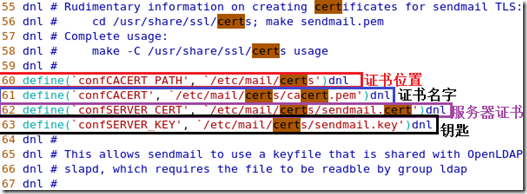
Email Address []:
[root@localhost CA]# ll
total 28
-rw-r--r-- 1 root root 1155 Mar 20 20:17 cacert.pem
drwxr-xr-x 2 root root 4096 Mar 20 20:08 certs
drwxr-xr-x 2 root root 4096 Mar 20 20:08 crl
-rw-r--r-- 1 root root 0 Mar 20 20:08 index.txt
drwxr-xr-x 2 root root 4096 Mar 20 20:08 newcerts
drwx------ 2 root root 4096 Mar 20 20:11 private
-rw-r--r-- 1 root root 3 Mar 20 20:09 serial
[root@mail CA]# chmod 600 private/* 更改钥匙权限
[root@mail CA]# mkdir /etc/mail/certs 创建目录
[root@mail CA]# cd /etc/mail/certs/ 切换到目录
[root@mail certs]# ll 查看
total 0
产生钥匙:
[root@mail certs]# openssl genrsa 1024 >sendmail.key
Generating RSA private key, 1024 bit long modulus
...........++++++
.++++++
e is 65537 (0x10001)
根据钥匙做请求文件:
[root@mail certs]# openssl req -new -key sendmail.key -out sendmail.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:HENAN
Locality Name (eg, city) [Newbury]:ZHENGZHOU
Organization Name (eg, company) [My Company Ltd]:zzdx
Organizational Unit Name (eg, section) []:tec
Common Name (eg, your name or your server's hostname) []:mail.bj.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
根据钥匙请求文件得到证书:
[root@mail certs]# openssl ca -in sendmail.csr -out sendmail.cert
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Mar 20 12:27:04 2012 GMT
Not After : Mar 20 12:27:04 2013 GMT
Subject:
countryName = CN
stateOrProvinceName = HENAN
organizationName = zzdx
organizationalUnitName = tec
commonName = mail.bj.com
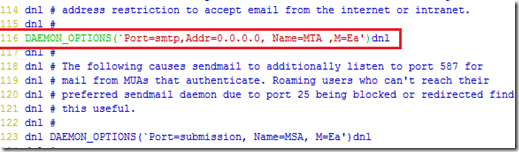
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
54:FA:EA:A7:E0:8B:72:DF:57:37:4E:41:84:AA:BA:1A:AB:C4:B7:C9
X509v3 Authority Key Identifier:
keyid:8F:9B:34:8D:DA:DD:63:D5:0B:07:AF:F4:E4:E0:C9:6C:04:44:65:CC
Certificate is to be certified until Mar 20 12:27:04 2013 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@mail certs]# ll 查看证书
total 12
-rw-r--r-- 1 root root 3075 Mar 20 20:27 sendmail.cert
-rw-r--r-- 1 root root 647 Mar 20 20:23 sendmail.csr
-rw-r--r-- 1 root root 887 Mar 20 20:19 sendmail.key
[root@mail certs]#cp /etc/pki/CA/cacert.pem . 把证书拷贝当前目录下
[root@mail certs]# ll 查看
total 16
-rw-r--r-- 1 root root 1155 Mar 12 12:07 cacert.pem
-rw-r--r-- 1 root root 3074 Mar 12 12:06 sendmail.cert
-rw-r--r-- 1 root root 647 Mar 12 12:05 sendmail.csr
-rw-r--r-- 1 root root 887 Mar 12 12:02 sendmail.key
[root@mail certs]# cd ..
[root@mail mail]# vim sendmail.mc 编辑sendmail配置脚本
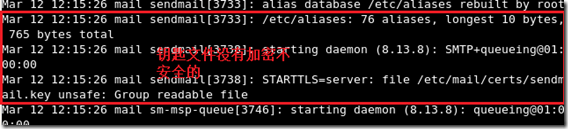
[root@mail mail]# service sendmail restart 重新启动sendmail
Shutting down sm-client: [ OK ]
Shutting down sendmail: [ OK ]
Starting sendmail: [ OK ]
Starting sm-client: [ OK ]
查看日志:tail –f /var/log/maillog
[root@mail mail]# cd certs/
[root@mail certs]# ll
total 16
-rw-r--r-- 1 root root 1155 Mar 12 12:07 cacert.pem
-rw-r--r-- 1 root root 3074 Mar 12 12:06 sendmail.cert
-rw-r--r-- 1 root root 647 Mar 12 12:05 sendmail.csr
-rw-r--r-- 1 root root 887 Mar 12 12:02 sendmail.key
[root@mail certs]# chmod 600 * 更改权限
[root@mail certs]# ll
total 16
-rw------- 1 root root 1155 Mar 12 12:07 cacert.pem
-rw------- 1 root root 3074 Mar 12 12:06 sendmail.cert
-rw------- 1 root root 647 Mar 12 12:05 sendmail.csr
-rw------- 1 root root 887 Mar 12 12:02 sendmail.key
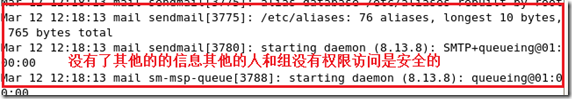
[root@mail certs]# service sendmail restart
Shutting down sm-client: [ OK ]
Shutting down sendmail: [ OK ]
Starting sendmail: [ OK ]
Starting sm-client: [ OK ]
 用Outlook Express查看是否加密:
用Outlook Express查看是否加密:
创建用户user1
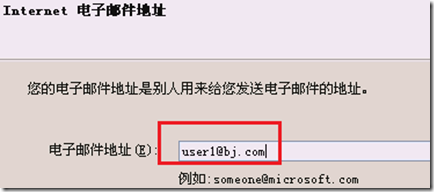
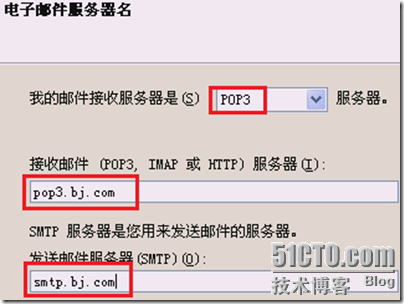
更改user1的属性:
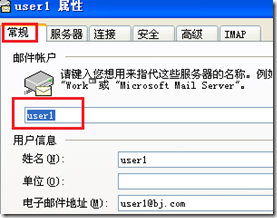
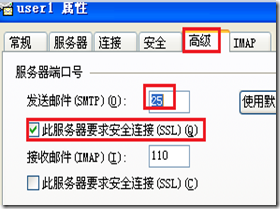
设置dns指向

发送一封邮件给自己:
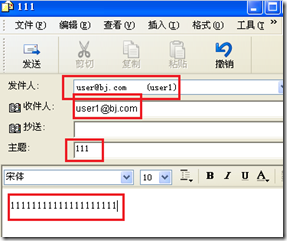

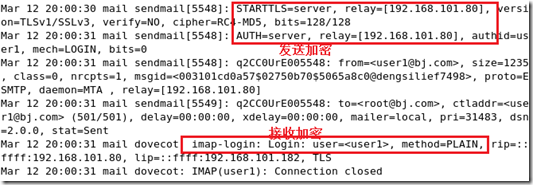
查看日志:(starttls 启动)
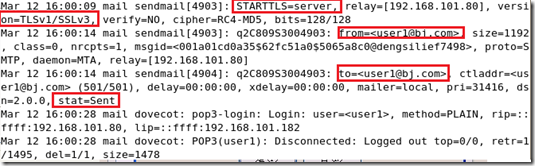
安装抓包工具截取明文邮件的账号:
[root@mail ~]# cd /mnt/cdrom/Server/
[root@mail Server]#vim /etc/yum.repos.d/rhel-debuginfo.repo
[root@mail Server]# yum list all |grep wir 搜索含wir的包
Repository rhel-server is listed more than once in the configuration
This system is not registered with RHN.
RHN support will be disabled.
wireless-tools.i386 1:28-2.el5 installed
wireshark.i386 1.0.8-1.el5_3.1 rhel-server
wireless-tools-devel.i386 1:28-2.el5 rhel-server
wireshark-gnome.i386 1.0.8-1.el5_3.1 rhel-server
[root@mail Server]# yum install wireshark 安装wireshark
启用抓包工具:(当用户接收邮件时:会显示用户名和密码)
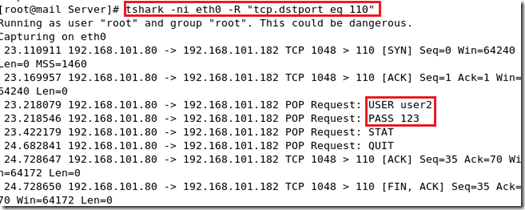
为了安全为了用户所以接收时也要进行加密:
[root@mail certs]# mkdir -pv /etc/dovecot/certs 创建目录
mkdir:created directory `/etc/dovecot`
mkdir: created directory `/etc/dovecot/certs`
[root@mail certs]# cd /etc/dovecot/certs/ 切换到certs目录
做钥匙:
[root@mail certs]# openssl genrsa 1024 >dovecot.key
Generating RSA private key, 1024 bit long modulus
...........++++++
.++++++
e is 65537 (0x10001)
产生请求文件:
[root@mail certs]# openssl req -new -key dovecot.key -out dovecot.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:HENAN
Locality Name (eg, city) [Newbury]:ZHENGZHOU
Organization Name (eg, company) [My Company Ltd]:zzdx
Organizational Unit Name (eg, section) []:tec
Common Name (eg, your name or your server's hostname) []:pop3.bj.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
获得证书:
[root@mail certs]# openssl ca -in dovecot.csr -out dovecot.cert
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 2 (0x2)
Validity
Not Before: Mar 20 12:27:04 2012 GMT
Not After : Mar 20 12:27:04 2013 GMT
Subject:
countryName = CN
stateOrProvinceName = HENAN
organizationName = zzdx
organizationalUnitName = tec
commonName = pop3.bj.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
54:FA:EA:A7:E0:8B:72:DF:57:37:4E:41:84:AA:BA:1A:AB:C4:B7:C9
X509v3 Authority Key Identifier:
keyid:8F:9B:34:8D:DA:DD:63:D5:0B:07:AF:F4:E4:E0:C9:6C:04:44:65:CC
Certificate is to be certified until Mar 20 12:27:04 2013 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@mail certs]# ll 查看证书
total 16
-rw-r--r-- 1 root root 3074 Mar 12 12:06 dovecot.cert
-rw-r--r-- 1 root root 647 Mar 12 12:05 dovecot.csr
-rw-r--r-- 1 root root 887 Mar 12 12:02 dovecot.key
[root@mail certs]# chmod 600 * 更改权限
[root@mail certs]# ll
total 16
--rw------- 1 root root 3074 Mar 12 12:06 dovecot.cert
-rw------- 1 root root 647 Mar 12 12:05 dovecot.csr
-rw------- 1 root root 887 Mar 12 12:02 dovecot.key
[root@mail certs]# vim /etc/dovecot.conf 更改配置脚本
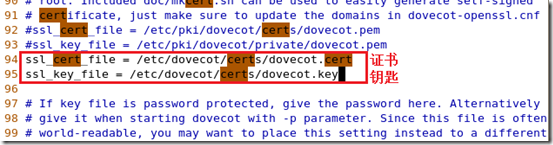
[root@mail certs]# service dovecot restart 重新启动dovecot
Stopping Dovecot Imap: [ OK ]
Starting Dovecot Imap: [ OK ]
[root@mail certs]# netstat -tupln |grep dov 查看端口
tcp 0 0 :::993 :::* LISTEN 4757/dovecot
tcp 0 0 :::110 :::* LISTEN 4757/dovecot
tcp 0 0 :::143 :::* LISTEN 4757/dovecot
用客户进行测试(加密的端口):
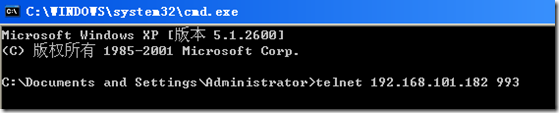
必须新建一个用户:
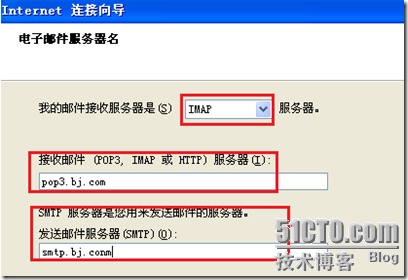
更改用户user1的属性:
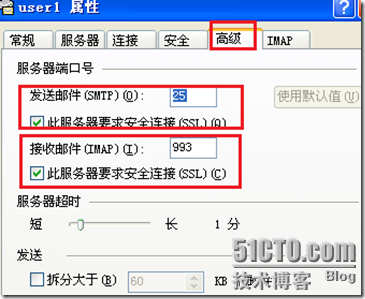
然后让用户user1接收邮件查看日志:
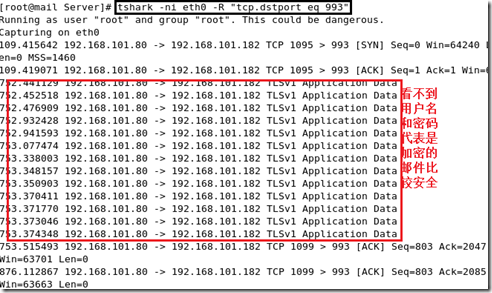
认证sasl(简单认证安全协议) 服务器是saslauthd
查看与有关的包:
[root@mail Server]# cd
[root@mail ~]# rpm -qa |grep sasl
cyrus-sasl-lib-2.1.22-5.el5 连接库包
cyrus-sasl-2.1.22-5.el5(很重要的包)
cyrus-sasl-devel-2.1.22-5.el5 开发包
cyrus-sasl-plain-2.1.22-5.el5 验证方法包
[root@mail ~]# cd /mnt/cdrom/Server/ 切换到光盘上
[root@mail Server]# ll |grep sasl 查找关于sasl的包
-r--r--r-- 103 root root 1251623 Jul 29 2009 cyrus-sasl-2.1.22-5.el5.i386.rpm
-r--r--r-- 99 root root 1418364 Jul 29 2009 cyrus-sasl-devel-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 28967 Jul 29 2009 cyrus-sasl-gssapi-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 24390 Jul 29 2009 cyrus-sasl-ldap-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 129180 Jul 29 2009 cyrus-sasl-lib-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 46415 Jul 29 2009 cyrus-sasl-md5-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 32054 Jul 29 2009 cyrus-sasl-ntlm-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 27027 Jul 29 2009 cyrus-sasl-plain-2.1.22-5.el5.i386.rpm
-r--r--r-- 103 root root 27330 Jul 29 2009 cyrus-sasl-sql-2.1.22-5.el5.i386.rpm
-r--r--r-- 278 root root 39119 Jan 19 2007 gnu-crypto-sasl-jdk1.4-2.1.0-2jpp.1.i386.rpm
[root@mail Server]# chkconfig --list |grep sasl 查看验证服务器情况
saslauthd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
[root@mail Server]# service saslauthd start 启动saslauthd
Starting saslauthd: [ OK ]
[root@mail Server]# chkconfig saslauthd on 设置成开机启动
[root@mail Server]# vim /usr/lib/sasl2/Sendmail.conf 编辑服务器配置脚本
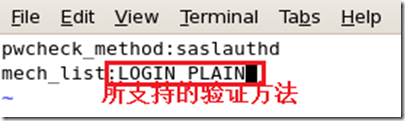
[root@mail Server]# vim /etc/mail/sendmail.mc 改写sendmail配置脚本
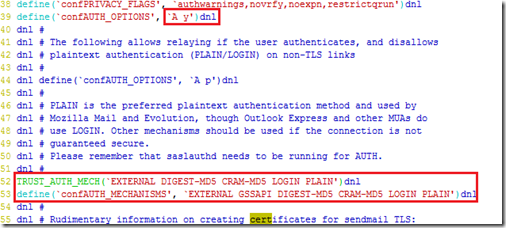
[root@mail Server]# service sendmail restart 重新启动sendmail
Shutting down sm-client: [ OK ]
Shutting down sendmail: [ OK ]
Starting sendmail: [ OK ]
Starting sm-client: [ OK ]
进行测试身份验证:
[root@mail Server]# telnet 127.0.0.1 25
Trying 127.0.0.1...
Connected to mail.bj.com (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Mon, 12 Mar 2012 17:48:52 +0800
EHLO 127.0.0.1
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-AUTH LOGIN PLAIN
250-STARTTLS
250-DELIVERBY
250 HELP
MAIL FROM:USER10@BJ.COM 虽然需要验证但是还可以匿名
250 2.1.0 USER10@BJ.COM... Sender ok 发送邮件说明这不是强制的验证
quit
221 2.0.0 mail.bj.com closing connection
Connection closed by foreign host.
编辑sendmail配置脚本使发邮件的用户需要强制的进行验证:
[root@mail Server]# vim /etc/mail/sendmail.mc
[root@mail Server]# service sendmail restart 重新启动sendmail
Shutting down sm-client: [ OK ]
Shutting down sendmail: [ OK ]
Starting sendmail: [ OK ]
Starting sm-client: [ OK ]
再次的进行身份验证测试:发送邮件
[root@mail Server]# telnet 127.0.0.1 25
Trying 127.0.0.1...
Connected to mail.bj.com (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Mon, 12 Mar 2012 18:29:08 +0800
EHLO 127.0.0.1
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-AUTH LOGIN PLAIN
250-STARTTLS
250-DELIVERBY
250 HELP
MAIL FROM:user10@bj.com
530 5.7.0 Authentication required 需要验证不是合法的用户无法发送邮件
AUTH LOGIN cm9vdA== 输入有效的用户的类似base64编码
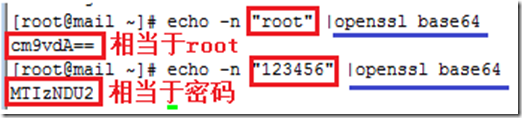
334 UGFzc3dvcmQ6
MTIzNDU2
235 2.0.0 OK Authenticated
MAIL FROM:root@bj.com 验证完之后要再次的输入root邮箱
250 2.1.0 root@bj.com... Sender ok
RCPT TO:user1@bj.com
250 2.1.5 user1@bj.com... Recipient ok
DATA
354 Enter mail, end with "." on a line by itself
4444444444444 邮件内容
. 结束
250 2.0.0 q2CAT8jA005317 Message accepted for delivery
quit 退出
221 2.0.0 mail.bj.com closing connection
Connection closed by foreign host.
用user1登陆查看邮件:
[root@mail Server]# su – user1
[user1@mail ~]$ mail
Mail version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/user1": 2 messages 1 new
1 MAILER-DAEMON@mail.b Sun Mar 11 23:30 13/542 "DON'T DELETE THIS MESSAGE -- FOLDER INTE"
>N 2 root@bj.com Mon Mar 12 18:41 12/390
& 2 查看邮件2
Message 2:
From root@bj.com Mon Mar 12 18:41:28 2012
Date: Mon, 12 Mar 2012 18:29:08 +0800
From: root <root@bj.com>
4444444444444
& exit 退出
在windows上用用户user1给自己发送邮件:
发送过程中会出现:出错信息
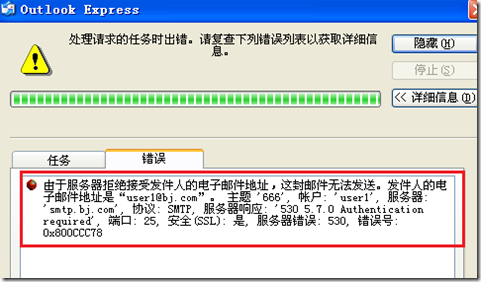
查看日志:看到
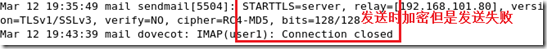
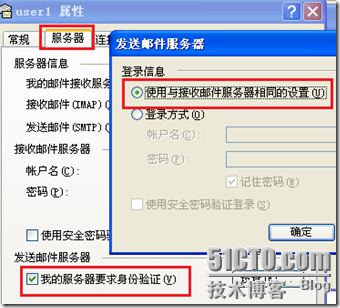
要想发送成功必须设置user1的属性服务器中的登陆于接收邮件具有相同的配置:然后发送
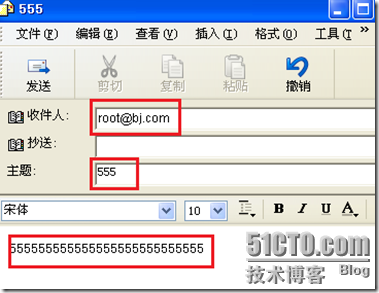
编写邮件发给root:
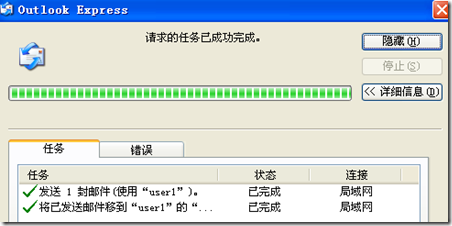
查看日志:
转载于:https://blog.51cto.com/1184394769/816727
mail安全性与加密相关推荐
- 图文结合彻底理解非对称加密、RSA原理及安全性(图文版)
博主:爱码叔 个人博客站点: icodebook 公众号:漫话软件设计 专注于软件设计与架构.技术管理.擅长用通俗易懂的语言讲解技术.对技术管理工作有自己的一定见解.文章会第一时间首发在个站上,欢迎大 ...
- 面向普通人的 PHP 加密
在这个日渐虚拟的互联网世界中,您必须小心保护自已的数据.本文将介绍编码和加密一些重要信息(比如密码.信用卡号.甚至整个消息)的基础知识.并通过使用 PHP 的内置功能,了解加密和解密信息的意义,并且将 ...
- 一种混合加密方案在软件授权中的应用
拥有知识产权的软件一般采取软件保护手段,需要使用某种方式激活软件才可以使用.软件激活本质是对密文数据进行比较,而密文数据是由软件开发商根据目标机器的特征数据进行加密产生的.激活过程是在认证服务器或者目 ...
- 了解Access安全性
简介 在早期版本的 Microsoft® Access(Microsoft Access 2000 以前)中,有关安全性的知识有时被认为是无法为任何人所掌握和应用的.您需要按顺序执行很多步骤,一旦遗漏 ...
- 【线上圆桌 - 263】视频会议终端到终端的加密
本次分享,将针对当前各类终端加密场景,分别介绍基于WebRTC的会议.SFU模式的会议以及WebRTC SFU模式的会议数据加密的异同. 内容源自263音视频架构师 贺晓敏在视频会议下半场圆桌上的分享 ...
- java与php链条遇到的坑,记一次Java加密加签算法到php的坑
写代码的经历中,总少不了与外部的程序对接,一旦有这样的事,往往周期会很长,很麻烦,因为你要考虑的事会多了很多,其中安全性的加密解密就是重要的一项.写代码,可以出Bug,但逼格不能弱.什么是逼格?和别人 ...
- win10文件夹加密_Win10 系统优化软件 Windows 10 Manager v3.2.0
↑ 关注 IT迷,更多干货资源等着你~ Windows 10 Manager是专门用于 Windows10 的集所有功能于一身的实用工具,它包括了40多个不同的实用程序来优化,调整,清理,加快和修复您 ...
- APP平台是怎样实现视频加密呢?
随着培训教育行业的快速发展,有的培训机构或者网校会有自己专门播放视频的APP或平台,学员在购买后可以直接在APP直接播放观看,但有时候可能会出现视频泄露的情况,比如通过账号共享,录屏等这些方式,那么有 ...
- PDF文件简介及PDF文档加密方法
PDF文件的认识: Adobe Reader 关于PDF的图标PDF全称Portable Document Format,译为可移植文档格式,是一种电子文件格式.这种文件格式与操作系统平台无关,也就是 ...
- 接口加密(TokenSpringCloud项目中进行token认证)
文章目录 接口加密 常见加密算法 消息摘要算法 常用摘要算法(MD5.SHA.CRC) 对称加密 常用对称加密算法(DES.3DES.AES) 非对称加密 常用的非对称加密算法(RSA.DSA.ECC ...
最新文章
- 关于机器学习算法的16个技巧
- Struts2 入门修行第一天 | 小节二
- Mybatis的几点小结
- 刷道谷歌泄漏的面试题:面试官想从中考察你什么?
- list 分组_「正则表达式」 匹配分组
- ansible(2)——基本命令
- 配置设备作为DHCP 服务器(基于全局地址池)
- 云图说|小云妹带你揭秘数据复制服务DRS四大功能
- 用Docker容器自带的tensorflow serving部署模型对外服务(成功率100%)
- python 小兵(2)
- 力扣-1508 子数组和排序后的区间和
- 媒体管理工具Media Encoder 2022 for Mac
- Java多线程系列 基础篇04 线程中断
- openGauss助力中国移动获 “ICT优秀案例”
- Python操作MyS QL
- tomcat图标修改——东子破解
- layui表格下拉框无法显示
- Untiy的阿拉伯文本适配
- 百度红包架构分析与推测
- 清风数学建模——插值算法
