希尔密码_密码学中的希尔密码
希尔密码
It is a polygraphic substitution cipher that depends on linear algebra. Every letter from the alphabet is represented by several modulo 26. Simply, we write as A = 0, B = 1, ..., Z = 25 is used, but this is not a correct feature of the cipher.
这是一个依赖于线性代数的测谎替代密码。 字母表中的每个字母都由26为模。简单地,我们写为A = 0,B = 1,...,Z = 25 ,但这不是密码的正确特征。
To encrypt a message, each block of n letters is multiplied by an invertible n × n matrix, against modulus 26 or we can say the multiple inverses of n.
为了加密消息,将n个字母的每个块都乘以可逆n×n矩阵(模数为26)或我们可以说n的多个逆。
To decrypt the message, every block is multiplied by the inverse of the matrix or inversed matrix used for encryption.
为了解密该消息,将每个块乘以用于加密的矩阵或逆矩阵的逆。
The matrix used for encryption is the plain text and one matrix is formed is cipher key when we combine or multiple them we get the new matrix called ciphertext, and the key should be chosen randomly from the set of invertible n × n matrices (modulo 26).
用于加密的矩阵是纯文本,当我们将它们组合或相乘时,形成的一个矩阵是密码密钥,得到一个新的矩阵,称为密文,密钥应从可逆n×n矩阵集中随机选择(取模26 )。
加密 (Encryption)
We have to do encryption on the message 'ACT' (n=3). The key is 'GYBNQKURP' which can be written as the n x n matrix that is 3 x 3 matrix,
我们必须对消息“ ACT”(n = 3)进行加密。 关键是“GYBNQKURP”,其可以被写为NxN矩阵是3×3矩阵,

The message for encryption 'ACT' is written as a vector,
加密消息“ ACT”写为矢量,

The enciphered vector is given as,
加密的向量为
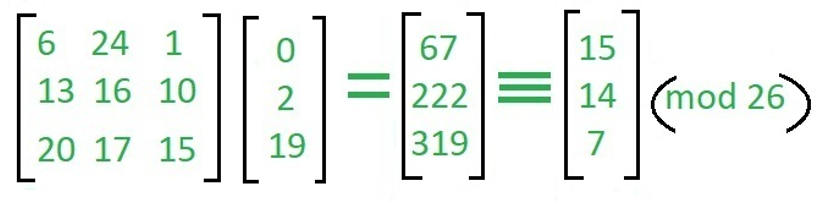
In this, we just do the multiple matrices we just multiple the 1 row with 1 column as we can say 6*0+24*2+1*19=67 same as 13*0+16*2+10*19=222 and 20*0+17*2+15*19=319.
在这里,我们只是做多个矩阵,我们只将1行与1列相乘,我们可以说6 * 0 + 24 * 2 + 1 * 19 = 67与13 * 0 + 16 * 2 + 10 * 19 = 222相同和20 * 0 + 17 * 2 + 15 * 19 = 319 。
And that matrix does the mod 26 with particular column and made again the 3*1 matrix and we alphabetically write them with called ciphertext i.e "POH".
然后,该矩阵使用特定的列进行mod 26运算,并再次制作3 * 1矩阵,然后按字母顺序将其写为密文,即“ POH” 。
解密 (Decryption)
To decrypt the message, we turn the ciphertext back into a plain text, then simply multiply by the inverse matrix of the key matrix as "IFKVIVVMI" in letters. The inverse of the matrix used in the encryption is,
为了解密该消息,我们将密文转换回纯文本,然后简单地乘以密钥矩阵的逆矩阵,即字母“ IFKVIVVMI” 。 加密中使用的矩阵的逆是
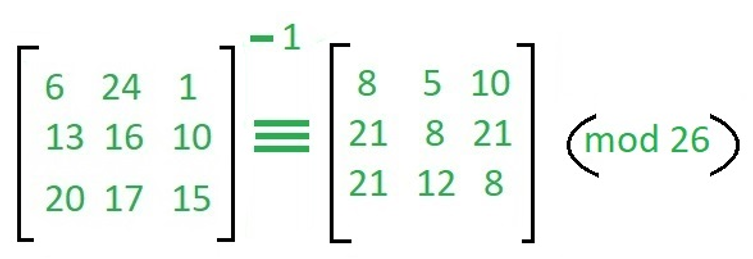
For ciphertext which we already find we decrypt that and make plain text,
对于我们已经发现的密文,我们将其解密并制成纯文本,
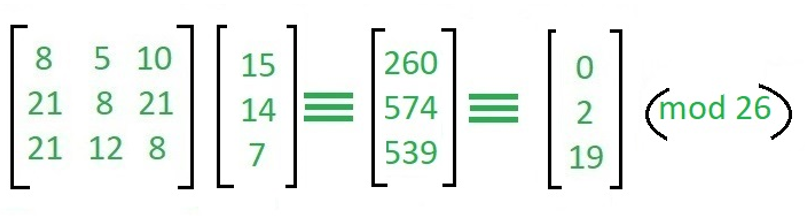
Now, we just find the inverse matrix then multiple it by key then it will give us back "ACT".
现在,我们只需找到逆矩阵,然后将其乘以键,然后它将返回“ ACT” 。
Let, K is DDCF
设K为DDCF

be the key and suppose the plaintext is "HELP". Then this plaintext is represented by two pairs because n is 2.
是键,并假定明文为“ HELP” 。 然后,此纯文本用两对表示,因为n为2 。

Firstly we do encryption, then we will compute
首先我们进行加密,然后我们将进行计算

and continue encryption as follows and written as,
并继续如下加密并写为:

The matrix K is invertible, hence K-1 exists such that KK-1 = K-1K = I2 The inverse of K can be computed by using the formula,
矩阵K是可逆的,因此存在K -1 ,使得KK -1 = K -1 K = I 2可以使用公式计算K的逆,

This formula still holds after a modular reduction if a modular multiplicative inverse is used to compute.
如果使用模块化乘法逆来进行计算,则该公式在模块化归约后仍然成立。
Now, we have to do decryption,
现在,我们必须进行解密,

Then we compute,
然后我们计算
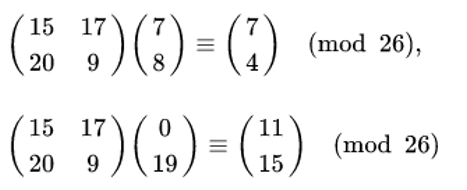
And we get,
我们得到

Security
安全
The basic Hill Cipher is vulnerable to a known-plaintext attack that attacks by key because it is completely linear algebra. An opposite site that intercepts n plaintext/ciphertext character pairs can set up a linear system that can be easily solved; if this will happen then this system is undefined, it is the only way is to add a few more plaintexts/ciphertext pairs. While when n x n matrix multiplication is a useful step when it will be combined with other non-linear operations because matrix multiplication can provide diffusion. For example, a unique chosen matrix can give security that minor differences before the matrix multiplication will give the answer in huge differences after the matrix multiplication. Otherwise, some new ciphers use a matrix multiplication step to gave diffusion. For example, the MixColumns matrix step in AES cipher is matrix multiplication. The function g in Twofish is a combination of non-linear algebra S-boxes i.e substitution boxes with a carefully chosen matrix multiplication (MDS) is used this.
基本的希尔密码很容易受到已知明文攻击,因为它是完全线性的代数,因此会受到密钥的攻击。 截获n个纯文本/密文字符对的相对站点可以建立一个易于解决的线性系统; 如果将发生这种情况,则该系统是不确定的,唯一的方法是添加更多的明文/密文对。 当nxn矩阵乘法是有用的步骤时,它将与其他非线性运算结合使用,因为矩阵乘法可以提供扩散。 例如,唯一选择的矩阵可以确保矩阵乘法之前的微小差异将在矩阵乘法之后的巨大差异中给出答案。 否则,某些新密码将使用矩阵乘法步骤进行扩散。 例如,AES密码中的MixColumns矩阵步骤是矩阵乘法。 Twofish中的函数g是非线性代数S-box的组合,即,使用具有精心选择的矩阵乘法(MDS)的替换框。
Reference: Hill Cipher
参考: 希尔密码
翻译自: https://www.includehelp.com/cryptography/hill-cipher.aspx
希尔密码
希尔密码_密码学中的希尔密码相关推荐
- playfair密码_密码学中的Playfair密码
playfair密码 Playfair cipher is also a substitution cipher technique but it is a bit different than ot ...
- 密码学电子书_密码学中的电子密码书(ECB)
密码学电子书 This Electronic Code Book (ECB) is cryptography as a mode of operation for a block cipher, wi ...
- 维吉尼亚密码和一次性密码本_密码学中的一次性密码
维吉尼亚密码和一次性密码本 The One-time Pad cipher is almost similar to the Vernam cipher, as, like the vernam ci ...
- des算法密码多长_密码学中的多个DES
des算法密码多长 This is a DES that was susceptible to attacks due to tremendous advances in computer hardw ...
- des加密密码补位_密码学中的数据加密标准(DES)
des加密密码补位 This is a Data Encryption Standard that is the asymmetric key generation for the encryptio ...
- 第一次改变root密码_密码学永远改变的一天
第一次改变root密码 On 1 August 1977, Scientific American, a popular science magazine, released its monthly ...
- 密码学加密算法分类_密码学中的国际数据加密算法(IDEA)
密码学加密算法分类 Introduction 介绍 International Data Encryption Algorithm (IDEA) is a type of cryptography a ...
- md5不是对称密码算法_密码学中的消息摘要算法5(MD5)
md5不是对称密码算法 In cryptography, MD5 (Message-Digest algorithm 5) is a mainly used cryptographic hash fu ...
- ofb模式_密码学中的输出反馈模式(OFB)
ofb模式 This is an output feedback (OFB) mode is similar in structure to that of CFB in Cryptography. ...
- 哈希密码_哈希生日和密码
哈希密码 什么是哈希函数? (What is a Hash function?) It's an algorithm that maps an input of arbitrary length to ...
最新文章
- 编码/解码和进制转化工具hURL
- 二叉树中任意两个节点的距离
- CF1251F-Red-White Fence【NTT】
- 数据结构两个月学完_这是我作为数据科学家两年来所学到的
- jQuery刻度尺滚动滑块插件
- 医疗设备-监护仪-数据解析(协议、通信)
- (27)FPGA计数器设计(硬核实现)
- 好的营销,往往叫广深高速
- asp.net 读取mysql_asp.net封装mysql工具类,在页面上引用读取的数据
- shell提取sql数据库文件里的单个表
- Ubuntu常用命令大全
- java mac算法_Mac算法的java实现
- 转 C++压缩解压之snappy
- 盲盒app源码,可搭建部署二开.模式功能介绍.
- #Javascript基础
- 我的梦想就是不工作,有什么错?
- 微软工程院 硕士_微软工程院招聘NLP算法研究员实习生|NLP算法工程师实习生_北京实习招聘...
- 最新研究进展|肠道微生物组在改善抗癌治疗效果方面的强大作用
- 十六进制解码_快速十六进制编码和解码
- 2022年2月最受欢迎编程语言排行榜|Python遥遥领先
热门文章
- 对讲机在哪插卡?插卡对讲机是什么意思呢?5000公里对讲机的哪点事
- 笔记总结-相机标定(Camera calibration)原理、步骤
- Mac 卸载Symantec软件
- 森林防火监控系统解决方案
- [Spring实战系列](2)Maven创建Spring-HelloWorld项目
- 用计算机从85加到98的和是,2018年职称计算机考试题库及答案
- Kali、linux中安装软件
- 学好mysql数据库能找到什么工作_MySQL数据库学习路线汇总整理全集(附详细的学习路线介绍图)...
- Curvy Little Bottles-二分和积分
- 永洪BI在 Linux/Unix 下 jdk 环境如何配置?
