02.CCNA 200-301 题库_51-100
title: CCNA 200-301 题库_51-100
date: 2022-07-13 16:24:16
permalink: /pages/503a31/
categories:
- 网络运维
- CCNA
- CCNA题库
tags: - https://jonas-wolfxin.github.io/pages/55766c/
CCNA 200-301 题库_51-100
How do AAA operations compare regarding user identification, user services, and access control?
A. Authorization provides access control, and authentication tracks user services
B. Accounting tracks user services, and authentication provides access control.
C. Authorization identifies users, and authentication provides access control
D. Authentication identifies users, and accounting tracks user services
Correct Answer D
Explanation:
- Authentication identifies users, Authorization provides access control, and accounting tracks user services
What is the difference between local AP mode and FlexConnect AP mode?
A. FlexConnect AP mode fails to function if the AP loses connectivity with the WLC.
B. FlexConnect AP mode bridges the traffic from the AP to the WLC when local switching is configured.
C. Local AP mode creates two CAPWAP tunnels per AP to the WLC.
D. Local AP mode causes the AP to behave as if it were an autonomous AP.
Correct Answer C
Explanation:
- In local mode, an AP creates two CAPWAP tunnels to the WLC. One is for management, the other is data traffic. This behavior is known as "centrally switched" because the data traffic is switched(bridged) from the ap to the controller where it is then routed by some routing device.
- The FlexConnect AP can locally switch traffic between a VLAN and SSID when the CAPWAP tunnel to the WLC is down.
- FlexConnect allows data traffic to be switched locally and not go back to the controller. It basically causes the AP to behave like an autonomous AP, but be managed by the WLC. In this mode, the AP can still function even if it looses connection with the controller.
which function does the range of private IPv4 addresses perform?
A. allow multiple companies to each use the same address without conflicts
B. provides a direct connection for hosts from outside of the enterprise network
C. ensures that NAT is not required to reach the internet with a private range
addressingD. enable secure communications to the internet for all external hosts
Correct Answer A
Explanation:
Refer to the exhibit. Which prefix does Router 1 use to Host A?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-sBtqdiTT-1661764332257)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/0000300001.png)]
A. 10.10.10.0/28
B. 10.10.13.0/25
C. 10.10.13.144/28
D. 10.10.13.208/29
Correct Answer D
Explanation:
A frame that enters a switch fails the Frame Check Sequence(FCS). Which two interface counters are incremented?
A. input errors
B. frame
C. giants
D. CRC
E. runts
Correct Answer A, D
Explanation:
- A. input errors - total sum of many counters (Includes runts, giants, no buffer, CRC, frame, overrun, and ignored counts.
- B. frame - received frames that have an illegal format
- C. giants - frames that exceed the maximum frame size
- D. CRC - received frames that did not pass the FCS math
- E. runts - frames that did not meet the minimum frame size
Ref: https://www.cisco.com/en/US/docs/internetworking/troubleshooting/guide/tr1904.html
what event has occurred if a router sends a notice level message to a Syslog server?
A. An interface line has changed status
B. An ICMP connection has been built
C. A certificate has expired
D. A TCP connection has been torn down
Correct Answer A Explanation:
0 Emergencies: System shutting down due to missing fan tray
1 Alerts: Temperature limit exceeded
2 Critical: Memory allocation failures
3 Errors: Interface Up/Down messages
4 Warnings: Configuration file written to server, via SNMP request
5 Notifications: Line protocol Up/Down
6 Information: Access-list violation logging
7 Debugging: Debug messagesAn organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
A. platform-as-a-service
B. software-as-a-service
C. network-as-a-service
D. infrastructure-as-a-service
Correct Answer D
Explanation:
- Below are the 3 cloud supporting services cloud providers provide to customer:
- PaaS (Platform as a Service): are used for applications, and other development, while providing cloud components to software. PaaS is a framework they can build upon to develop or customize applications. PaaS makes the development, testing, and deployment of applications quick, simple, and cost-effective. As a result, PaaS frees developers from having to install in-house hardware and software to develop or run a new application.
- SaaS (Software as a Service): SaaS uses the web to deliver applications that are managed by a third-party vendor and whose interface is accessed on the clients' side. Most SaaS applications can be run directly from a web browser without any downloads or installations required, although some require plugins.
- With IaaS, a provider supplies the basic compute, storage and networking infrastructure along with the hypervisor -- the virtualization layer. Users must then create virtual instances such as VMs and containers, install OSes, support applications and data, and handle all of the configuration and management associated with those tasks. Some examples of IaaS services are DigitalOcean, AWS, Azure and Google Compute Engine.
Ref: https://www.techtarget.com/searchcloudcomputing/definition/Platform-as-a-Service-PaaS
Refer to the exhibit. Which route does R1 select for traffic that is destined to 192 168.16.2?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Z70yy0L9-1661764332258)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/0004400001.png)]
A. 192.168.16.0/21
B. 192.168.16.0/24
C. 192.168 26.0/26
D. 192.168.16.0/27
Correct Answer D
Explanation:
- A router evaluates and selects routes in the following order:
- Prefix Length - The longest-matching route is preferred first. Prefix length trumps all other route attributes.
- Administrative Distance - In the event there are multiple routes to a destination with the same prefix length, the route learned by the protocol with the lowest administrative distance is preferred.
- Metric - In the event there are multiple routes learned by the same protocol with same prefix length, the route with the lowest metric is preferred. (If two or more of these routes have equal metrics, load balancing across them may occur.)
source : https://packetlife.net/blog/2010/aug/16/route-preference/
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
A. The switch must be running a k9 (crypto) IOS image
B. The IP domain-name command must be configured on the switch
C. IP routing must be enabled on the switch
D. A console password must be configured on the switch
E. Telnet must be disabled on the switch
Correct Answer A,B
Explanation:
- Ref: https://www.cisco.com/c/en/us/support/docs/security-vpn/secure-shell-ssh/4145-ssh.html
Refer to the exhibit. An engineer configured NAT translations and has verified that the configuration is correct. Which IP address is the source IP after the NAT has taken place?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-RKdjsFuQ-1661764332258)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/image-20220703000423209.png)]
A. 10.4.4.4
B. 10.4.4.5
C. 172.23.103.10
D. 172.23.104.4
Correct Answer D
Explanation:
- After the NAT has taken place, the private address 10.4.4.4 and 10.4.4.5 are being NATTED to public address 172.23.104.3 and 172.23.104.4 respectively, which are the source addresses. Therefore the correct answer should be both 172.23.104.3 and 172.23.104.4, but it's none of the options, but the closest is option D
- Inside local = private source IP;
Inside global = public source IP (after the NAT has taken place);
Outside global = public destination IP;
Inside global = private destination IP
Which command is used to specify the delay time in seconds for LLDP to initialize on any interface?
A. lldp timer
B. lldp holdtime
C. lldp reinit
D. lldp tlv-select
Correct Answer C
Explanation:
- lldp holdtime seconds: Specify the amount of time a receiving device should hold the information from your device before discarding it
- lldp reinit delay: Specify the delay time in seconds for LLDP to initialize on an interface
- lldp timer rate: Set the sending frequency of LLDP updates in seconds
(config)#lldp ?holdtime Specify the holdtime (in sec) to be sent in packetsreinit Delay (in sec) for LLDP initialization on any interfacerun Enable LLDPtimer Specify the rate at which LLDP packets are sent (in sec)tlv-select Selection of LLDP TLVs to send
Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3560/software/release/12-2_55_se/configuration/guide/3560_scg/swlldp.html
Refer to the exhibit. An administrator configures four switches for local authentication using passwords that are stored as a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?
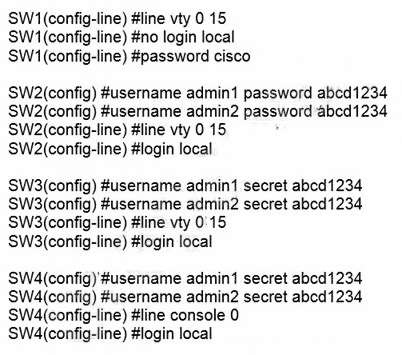
A. SW1
B. SW2
C. SW3
D. SW4
Correct Answer C
Explanation:
- Keyword local authentication: "login local" configuration
- Keyword cryptographic hash: "secret" configuration
- Keyword SSH access: "live vty 0 15" configuration
which statement identifies the functionality of virtual machines?
A. The hypervisor communicates on Layer 3 without the need for additional resources
B. Each hypervisor can support a single virtual machine and a single software switch
C. The hypervisor can virtualize physical components including CPU, memory, and storage.
D. Virtualized servers run most efficiently when they are physically connected to a switch that is separate from the hypervisor.
Correct Answer C
Explanation:
when configuring IPv6 on an interface, which two IPv6 multicast groups are joined?
(Choose two)
A. 2000::/3
B. 2000::5
C. FC00::/7
D. FF02::1
E. FF02::2
Correct Answer D,E
Explanation:
- All-nodes link-local multicast group FF02::1.
When an interface is configured with IPv6 address, it automatically joins the all nodes (FF02::1) and solicited-node (FF02::1:FFxx:xxxx) multicast groups. The all- node group is used to communicate with all interfaces on the local link, and the solicited-nodes multicast group is required for link-layer address resolution. - All-routers link-local multicast group FF02::2. Routers also join a third multicast group, the all-routers group (FF02::2).
- IPv6 classifications:
- Multicast - FF
Global Unicast - 2/3
Unique Local - FC/FD
Link Local - FE80
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipv6/configuration/xe-3s/ipv6-xe-36s-book/ip6-multicast.html
- All-nodes link-local multicast group FF02::1.
Which option about JSON is true?
A. uses predefined tags or angle brackets () to delimit markup text
B. used to describe structured data that includes arrays
C. used for storing information
D. similar to HTML, it is more verbose than XML
Correct Answer B
Explanation:
- JSON data is written as name/value pairs. A name/value pair consists of a field name (in double quotes), followed by a colon, followed by a value.
- JSON can use arrays. Array values must be of type string, number, object, array, boolean or null.
Which statement correctly compares traditional networks and controller-based networks?
A. Only traditional networks offer a centralized control plane
B. Only traditional networks natively support centralized management
C. Traditional and controller-based networks abstract policies from device configurations
D. Only controller-based networks decouple the control plane and the data plane
Correct Answer D
Explanation:
- Most traditional devices use a distributed architecture, in which each control plane is resided in a networking device. Therefore they need to communicate with each other via messages to work correctly.
- In contrast to distributed architecture, centralized (or controller-based) architectures centralizes the control of networking devices into one device, called SDN controller.
What are the two fundamentals of virtualization? (Choose two)
A. It allows multiple operating systems and applications to run independently on one physical server.
B. It allows a physical router to directly connect NICs from each virtual machine into the network.
C. The environment must be configured with one hypervisor that serves solely as a network manager to monitor SNMP traffic.
D. It allows logical network devices to move traffic between virtual machines and the rest of the physical network.
E. It requires that some servers, virtual machines, and network gear reside on the Internet.
Correct Answer A, D
Explanation:
- Each virtualization solution have virtual switches (logical network), these virtual switches allows virtual machines to communicate on the network. We also assign vlan tag on these switches or make them trunk.
- NICs are not part of VMs. Virtual switches of VMs are what connect vitrual NICs of VMs to physical network ( say a router).
Refer to the exhibit. What two conclusions should be made about this configuration? (Choose two)

A. The root port is FastEthernet 2/1
B. The spanning-tree mode is Rapid PVST+
C. The designated port is FastEthernet 2/1
D. The spanning-tree mode is PVST+
E. This is a root bridge
Correct Answer A, B
Explanation:
- Rapid STP or RSTP is IEEE standard; Rapid PVST+ is cisco proprietary
Which command enables a router to become a DHCP client?
A. ip address dhcp
B. ip helper-address
C. ip dhcp pool
D. ip dhcp clientCorrect Answer A
Explanation:
- If we want to get an IP address from the DHCP server on a Cisco device, we can use the command ip address dhcp.
- Note: The command ip helper-address DHCPServerIPAddress enables a router to become a DHCP Relay Agent.
Refer to the exhibit. A router received these five routes from different routing information sources. Which two routes does the router install in the routing table? (Choose two)

A. iBGP route 10.0.0.0/30
B. RIP route 10.0.0.0/30
C. EIGRP route 10.0.0.1/32
D. OSPF route 10.0.0.0/30
E. OSPF route 10.0.0.0/16
Correct Answer C, D, E
Explanation:
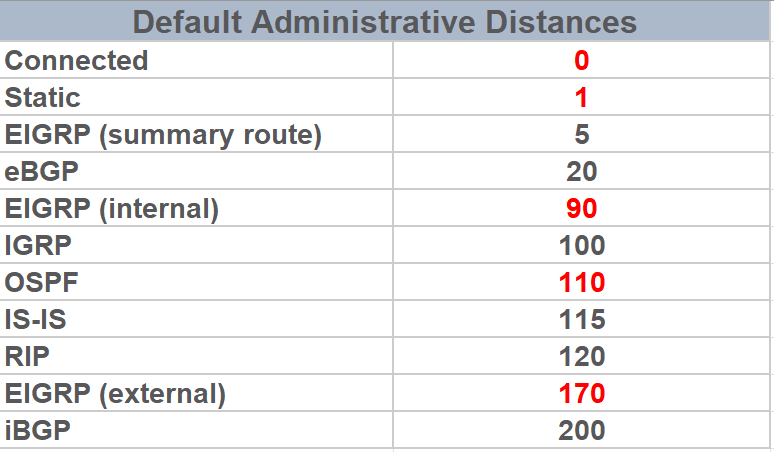
- Ref: https://www.cisco.com/c/en/us/support/docs/ip/enhanced-interior-gateway-routing-protocol-eigrp/8651-21.html
what is the default behavior of a layer 2 switch when a frame with an unknown destination MAC address is received?
A. The Layer 2 switch forwards the packet and adds the destination MAC address to its MAC address table
B. The Layer 2 switch sends a copy of a packet to the CPU for destination MAC address learning
C. The Layer 2 switch floods packets to all ports except the receiving port in the given VLAN
D. The Layer 2 switch dorps the received frame
Correct Answer C
Explanation:
- If the destination MAC address is not in the CAM table (unknown destination MAC address), the switch sends the frame out all other ports that are in the same VLAN as the received frame. This is called flooding. It does not flood the frame out the same port on which the frame was received.
Refer to the exhibit. An extended ACL has been configured and applied to router R2. The configuration started to work as intended. Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two)

A. Add a “permit ip any any” statement to the beginning of ACL 101 for allowed traffic.
B. Add a “permit ip any any” statement at the end of ACL 101 for allowed traffic
C. The source and destination IPs must be swapped in ACL 101
D. The ACL must be configured with the Gi0/2 interface inbound on R1
E. The ACL must be moved to the Gi0/1 interface outbound on R2
Correct Answer B, C
Explanation:
Which two tasks must be performed to configure NTP to a trusted server in client mode on a single network device? (Choose two)
A. Enable NTP authentication
B. Verify the time zone
C. Disable NTP broadcasts
D. Specify the IP address of the NTP server
E. Set the NTP server private key
Correct Answer A, D
Explanation:
- To configure authentication, perform this task in privileged mode:
- Step 1: Configure an authentication key pair for NTP and specify whether the key will be trusted or untrusted.
Step 2: Set the IP address of the NTP server and the public key.
Step 3: Enable NTP client mode.
Step 4: Enable NTP authentication.
Step 5: Verify the NTP configuration. - The question required to configure client mode, i think NTP server "private key" should not be valid. It should be "public key" Reference - https://www.cisco.com/en/US/products/hw/switches/ps-679/products_configuration_guide_chapter09186a008007d785.html#14543
- Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4000/8-2glx/configuration/guide/ntp.html
Reference:: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4000/8-2glx/configuration/guide/ntp.html#wp1019854
A user configured OSPF in a single area between two routers. A serial interface connecting R1 and R2 is running encapsulation PPP. By default which OSPF network type is seen on this interface when the user types show ip ospf interface on R1 or R2?
A. port-to-multipoint
B. broadcast
C. point-to-point
D. non-broadcast
Correct Answer C
Explanation:
- The default OSPF network type for HDLC and PPP on Serial link is point-to-point.
- while the default OSPF network type for Ethernet link is Broadcast
Refer to Exhibit. An engineer is configuring the NEW York router to reach the Lo1 interface of the Atlanta router using interface Se0/0/0 as the primary path. Which two commands must be configured on the New York router so that it can reach the Lo1 interface of the Atlanta router via Washington when the link between New York and Atlanta goes down? (Choose two)
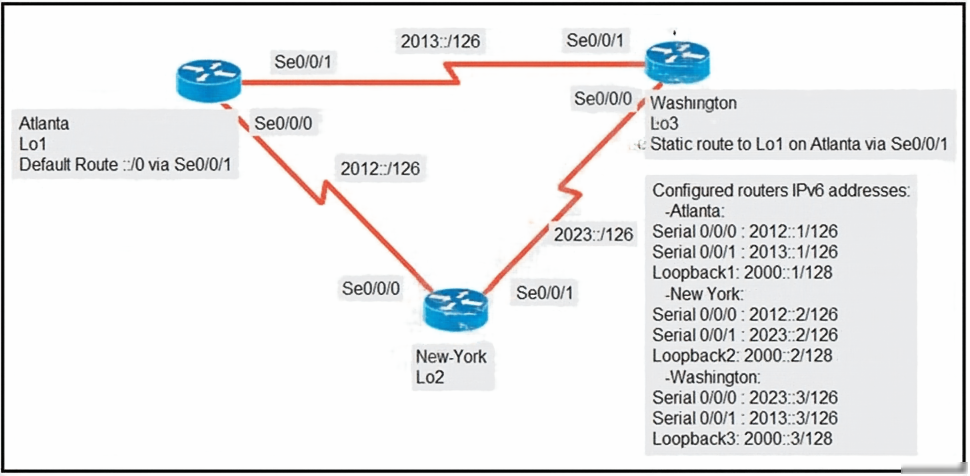
A. ipv6 router 2000::1/128 2012::1
B. ipv6 router 2000::1/128 2012::1 5
C. ipv6 router 2000::1/128 2012::2
D. ipv6 router 2000::1/128 2023::2 5
E. ipv6 router 2000::1/128 2023::3 5
Correct Answer A, E
Explanation:
- Ipv6 route 2000::1/128 2012::1 = washington to atlanta (always up hence, static AD=1)
- Ipv6 route 2000::1/128 2023::3 5 = NY to washington (backup route hence AD = 5)
The network administrator wants VLAN 67 traffic to be untagged between Switch 1 and Switch 2 while all other VLANs are to remain tagged. Which command accomplishes this task?
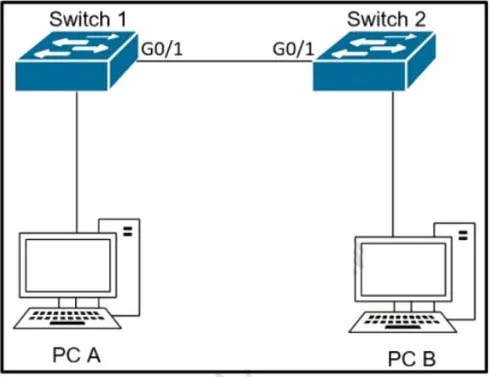
A. switchport access vlan 67
B. switchport trunk allowed vlan 67
C. switchport private-vlan association host 67
D. switchport trunk native vlan 67
Correct Answer D
Explanation:
- Native VLAN: The native VLAN is the one into which untagged traffic will be put when it’s received on a trunk port. This makes it possible for your VLAN to support legacy devices or devices that don’t tag their traffic like some wireless access points and simply network attached devices.
What are the two differences between optical-fiber cabling and copper cabling? (Choose two.)
A. Fiber connects to physical interfaces using RJ-45 connections.
B. The data can pass through the cladding.
C. Light is transmitted through the core of the fiber.
D. The glass core component is encased in a cladding.
E. A BNC connector is used for fiber connections.
Correct Answer C, D
Explanation:
- There are 3 kind of wiring mainly when we talk about networking: Fiber, Coaxial cable, twisted pair. The last 2 are Copper wiring
- BNC Connector is for Coaxial Cable
- the structure of fiber is: Jacket encase Buffer, Buffer encase Cladding, Cladding encase core. We uses light to transmit data through the core.
- RJ45 is a connector is for twisted pair,
which IPv6 address type provides communication between subnets and cannot route on the internet?
A. link-local
B. unique local
C. multicast
D. global unicast
Correct Answer B
Explanation:
- link local addresses do not communicate with other subnets. IPv6 defines rules so the packets sent to any link-local addresses should not be forwarded by any router to another subnet.
Which 802.11 frame type is Association Response?
A. management
B. protected frame
C. action
D. control
Correct Answer
Explanation:
- There are three main types of 802.11 frames: the Data Frame, the Management Frame and the Control Frame. Association Response belongs to Management Frame. Association response is sent in response to an association request.
- Reference: https://en.wikipedia.org/wiki/802.11_Frame_Types
- Reference: https://www.youtube.com/watch?v=PCpnRqKCWCQ
which two minimum parameters must be configured on an active interface to enable OSPFv2 to operate? (Choose two)
A. IPv6 address
B. OSPF process ID
C. OSPF MD5 authentication key
D. OSPF stub flag
E. OSPF area
Correct Answer B, E
Explanation:
- https://www.pearsonitcertification.com/articles/article.aspx?p=1868078#:~:text=2,area%20area-id
- https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_ospf/configuration/xe-3e/iro-xe-3e-book/iro-mode-ospfv2.pdf
- https://www.ietf.org/rfc/rfc2328.txt#:~:text=Area%20ID%0A%20%20%20%20%20%20%20%20%20%20%20%20The%20OSPF%20area%20that%20the%20packet%20is%20being%20sent%20into
Refer to the Exhibit. After the switch configuration, the ping test fails between PC A and PC B Based on the output for switch 1. Which error must be corrected?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-xQzcmO7J-1661764332260)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131515646.png)]
A. There is a native VLAN mismatch
B. Access mode is configured on the switch ports.
C. The PCs are m the incorrect VLAN
D. All VLANs are not enabled on the trunk
Correct Answer A
Explanation:
Which action is taken by a switch port enabled for PoE power classification override?
A. When a powered device begins drawing power from a PoE switch port a Syslog message is generated
B. As power usage on a PoE switch port is checked data flow to the connected device is temporarily paused
C. If a switch determines that a device is using less than the minimum configured power it assumes the device has failed and disconnects
D. If a monitored port exceeds the maximum administrative value for power, the port is shutdown and err-disabled
Correct Answer D
Explanation:
- PoE monitoring and policing compares the power consumption on ports with the administrative maximum value (either a configured maximum value or the port's default value). If the power consumption on a monitored port exceeds the administrative maximum value, the following actions occur:
- A syslog message is issued.
- The monitored port is shut down and error-disabled.
- The allocated power is freed.
Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/power_over_ethernet.pdf
What are the two characteristics of a controller-based network? (Choose two)
A. The administrator can make configuration updates from the CLI
B. It uses northbound and southbound APIs to communicate between architectural layers
C. It moves the control plane to a central point
D. It decentralizes the control plane, which allows each device to make its own forwarding decisions
E. It uses Telnet to report system issues
Correct Answer B, C
Explanation:
- controller-based networking A style of building computer networks that use a controller that centralizes some features and provides application programming interfaces (APIs) that allow for software interactions between applications and the controller (northbound APIs) and between the controller and the network devices (southbound APIs).
- centralized control plane An approach to architecting network protocols and products that places the control plane functions into a centralized function rather than distributing the function across the networking devices.
Refer to the exhibit. Which password must an engineer use to enter the enable mode?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-7yt0iPvP-1661764332260)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131524029.png)]
A. adminadmin123
B. default
C. testing 1234
D. cisco123
Correct Answer C
Explanation:
- Enable Secret overrides the Enable Password command
Which QoS Profile is selected in the GUI when configuring a voice-over WLAN deployment?
A. Bronze
B. Platinum
C. Silver
D. Gold
Correct Answer B
Explanation:
- Cisco Unified Wireless Network solution WLANs support four levels of QoS: Platinum/Voice, Gold/Video, Silver/Best Effort (default), and Bronze/Background.
- Reference: https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/ b_cg74_CONSOLIDATED_chapter_01010111.html
A router running EIGRP has learned the same route from two different paths. Which parameter does the router use to select the best path?
A. cost
B. administrative distance
C. metric
D. as-path
Correct Answer C
Explanation:
- If a router learns two different paths for the same network from the same routing protocol, it has to decide which route is better and will be placed in the routing table. Metric is the measure used to decide which route is better (lower number is better). Each routing protocol uses its own metric.
- For example, RIP uses hop counts as a metric, while OSPF uses cost.
Refer to the exhibit. After the configuration is applied, the two routers fail to establish an OSPF neighbor relationship. what is the reason for the problem?

A. The OSPF router IDs are mismatched.
B. Router2 is using the default hello timer.
C. The network statement on Router1 is misconfigured.
D. The OSPF process IDs are mismatched
Correct Answer B
Explanation:
- the default hello time is 10 seconds which causes a mismatch
How do TCP and UDP differ in the way they provide reliability for the delivery of packets?
A. TCP does not guarantee delivery or error checking to ensure that there is no data corruption; UDP provides message acknowledgment and retransmits data if lost.
B. TCP provides flow control to avoid overwhelming a receiver by sending too many packets at once; UDP sends packets to the receiver in a continuous stream without checking for sequencing.
C. TCP uses windowing to deliver packets reliably; UDP provides reliable message transfer between hosts by establishing a three-way handshake
D. TCP is a connectionless protocol that does not provide reliable delivery of data; UDP is a connection-oriented protocol that uses sequencing to provide reliable delivery.
Correct Answer B
Explanation:
Which output displays a JSON data representation?
A. [外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-MgIZPaxx-1661764332261)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131538690.png)]
B. [外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-9ItsGLm9-1661764332261)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131539617.png)]
C.

D.[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-vUyz8DF8-1661764332262)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131539928.png)]
Correct Answer C
Explanation:
- JSON uses ":" and ","
- It does not use ".", ";" and "-"
Refer to the exhibit. With which metric was the route to host 172.16.0.202 learned?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-FOS2MeZP-1661764332262)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131543286.png)]
A. 0
B. 110
C. 38443
D. 3184439
Correct Answer C
Explanation:
- We have two different routes which covers this.
- The Static 172.16.0.0/24.
- The OSPF 172.16.0.128/25.
- Now with the Longest Prefix Match rule the second route is selected and the correct metric for the route 17216.2.202 will option C.
A packet is destined for 10.10.1.22. which static route does the router choose to forward the packet?
A. ip route 10.10.1.0 255.255.255.240 10.10.255.1
B. ip route 10.10.1.20 255.255.255.252 10.10.255.1
C. ip route 10.10.1.20 255.255.255.254 10.10.255.1
D. ip route 10.10.1.16 255.255.255.252 10.10.255.1
Correct Answer B
Explanation:
An email user has been lured into clicking a link in an email sent by their company’s security organization. The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
A. Physical access control
B. Social engineering attack
C. brute force attack
D. user awareness
Correct Answer D
Explanation:
- This is a training program which simulates an attack, not a real attack (as it says ג€The webpage that opens reports that it was safeג€) so we believed it should be called a ג€user awarenessג€ program. Therefore the best answer here should be ג€user awarenessג€.
- This is the definition of ג€User awarenessג€ from CCNA 200-301 Offical Cert Guide Book: ג€User awareness: All users should be made aware of the need for data confidentiality to protect corporate information, as well as their own credentials and personal information. They should also be made aware of potential threats, schemes to mislead, and proper procedures to report security incidents. ג€
- Note: Physical access control means infrastructure locations, such as network closets and data centers, should remain securely locked.
Refer to the exhibit. Router R1 Fa0/0 cannot ping router R3 Fa0/1. Which action must be taken in router R1 to help resolve the configuration issue?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-wrlOgPfc-1661764332263)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131553791.png)]
A. set the default network as 20.20.20.0/24
B. configure a static route with Fa0/1 as the egress interface to reach the 20.20.20.0/24 network
C. set the default gateway as 20.20.20.2
D. configure a static route with 10.10.10.2 as the next hop to reach the 20.20.20.0/24 network
Correct Answer D
Explanation:
Refer to Exhibit. Which action do the switches take on the trunk link?

A. The trunk does not form and the ports go into an err-disabled status.
B. The trunk forms but the mismatched native VLANs are merged into a single broadcast domain.
C. The trunk does not form, but VLAN 99 and VLAN 999 are allowed to traverse the link.
D. The trunk forms but VLAN 99 and VLAN 999 are in a shutdown state.
Correct Answer B
Explanation:
- 802.1q trunking inserts a four-byte 802.1q tag field into frames sent over the trunk, which contain VLAN information. The 802.1q tag is inserted into each frame transferred over the trunk except for frames transmitted on the native VLAN, which are sent untagged.
- In most cases, the native VLAN has to match on both sides of the trunk unless there is a specific unusual configuration requirement, which is outside the scope of this document. If the native VLANs do not match, the switch will log Cisco Discovery Protocol (CDP) messages stating the mismatch. While not catastrophic, this setup effectively causes the two different native VLANs to be merged into one larger L2 broadcast domain (VLAN). These two VLANs will attempt to calculate one common Spanning-Tree Protocol (STP) topology for such bridged native VLANs, with the risk of eventually exceeding the maximum supported STP diameter
which IPv6 address block sends packets to a group address rather than a single address
A. 2000::/3
B. FC00::/7
C. FE80::/10
D. FF00::/8
Correct Answer D
Explanation:
- FF00::/8 is used for IPv6 multicast and this is the IPv6 type of address the question wants to ask.
- FE80::/10 range is used for link-local addresses. Link-local addresses only used for communications within the local subnetwork (automatic address configuration, neighbor discovery, router discovery, and by many routing protocols). It is only valid on the current subnet. It is usually created dynamically using a link-local prefix of FE80::/10 and a 64-bit interface identifier (based on 48-bit MAC address).
Two switches are connected and using Cisco Dynamic Trunking Protocol. SW1 is set to Dynamic Auto and SW2 is set to Dynamic Desirable. What is the result of this configuration?
A. The link is downstate.
B. The link is in an error disables state
C. The link becomes an access port.
D. The link becomes a trunk port.
Correct Answer D
Explanation:
- Dynamic Auto — Makes the Ethernet port willing to convert the link to a trunk link. The port becomes a trunk port if the neighboring port is set to trunk or dynamic desirable mode. This is the default mode for some switchports.
- Dynamic Desirable — Makes the port actively attempt to convert the link to a trunk link. The port becomes a trunk port if the neighboring Ethernet port is set to trunk, dynamic desirable or dynamic auto mode.
Refer to the exhibit. Which command provides this output?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-d4QbJ0L4-1661764332263)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131615576.png)]
A. show ip route
B. show ip interface
C. show interface
D. show cdp neighbor
Correct Answer D
Explanation:
Refer to the exhibit. If configuring a static default route on the router with the
ip route 0.0.0.0 0.0.0.0 10.13.0.1 120command, how does the router respond?[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-NpPwrGOK-1661764332264)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131617617.png)]
A. It ignores the new static route until the existing OSPF default route is removed
B. It immediately replaces the existing OSPF route in the routing table with the newly configured static route
C. It starts load-balancing traffic between the two default routes
D. It starts sending traffic without a specific matching entry in the routing table to Gigabit Ethernet0/1
Correct Answer A
Explanation:
- AD for the new static route is 120, which is bigger than 110 of OSPF
R1(config)#ip route 192.168.1.0 255.255.255.0 10.1.1.1 ?1-255 Distance metric for this routemulticast multicast routename Specify name of the next hoppermanent permanent routetag Set tag for this routetrack Install route depending on tracked item
Refer to the exhibit. An engineer must add a subnet for a new office that will add 20 users to the network. Which IPv4 network and subnet mask combination does the engineer assign to minimize wasting addresses?
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-uX46xf2a-1661764332264)(https://cdn.jsdelivr.net/gh/Wolfxin/MyPicGo/img/202207131620021.png)]
A. 10.10.225.48 255.255.255.240
B. 10.10.225.32 255.255.255.240
C. 10.10.225.48 255.255.255.224
D. 10.10.225.32 255.255.255.224
Correct Answer D
Explanation:
An engineer must configure a WLAN using the strongest encryption type for WPA2- PSK. Which cipher fulfills the configuration requirement?
A. WEP
B. RC4
C. AES
D. TKIPCorrect Answer C
Explanation:
- Many routers provide WPA2-PSK (TKIP), WPA2-PSK (AES), and WPA2-PSK (TKIP/AES) as options. TKIP is actually an older encryption protocol introduced with WPA to replace the very-insecure WEP encryption at the time. TKIP is actually quite similar to WEP encryption. TKIP is no longer considered secure, and is now deprecated. In other words, you shouldn't be using it.
- AES is a more secure encryption protocol introduced with WPA2 and it is currently the strongest encryption type for WPA2-PSK.
mary>Correct Answer
D
Explanation:
An engineer must configure a WLAN using the strongest encryption type for WPA2- PSK. Which cipher fulfills the configuration requirement?
A. WEP
B. RC4
C. AES
D. TKIPCorrect Answer C
Explanation:
- Many routers provide WPA2-PSK (TKIP), WPA2-PSK (AES), and WPA2-PSK (TKIP/AES) as options. TKIP is actually an older encryption protocol introduced with WPA to replace the very-insecure WEP encryption at the time. TKIP is actually quite similar to WEP encryption. TKIP is no longer considered secure, and is now deprecated. In other words, you shouldn't be using it.
- AES is a more secure encryption protocol introduced with WPA2 and it is currently the strongest encryption type for WPA2-PSK.
02.CCNA 200-301 题库_51-100相关推荐
- 【最新免费】CCNA中文注释题库精选模拟题
CCNA中文注释题库精选模拟题 详细地址:http://selftest.51cto.com/subread.php?sid=296 自测简介: CCNA考试由于试题全部是英文组成,这对于中国 ...
- python100到200的素数_python二级题库12–100到200的素数
一.题目判断101-200之间有多少个素数,并输出所有素数. 二.分析 1.认识素数 素数:质数定义为在大于1的自然数中,除了1和它本身以外不再有其他因数 三.方案def isPrime(num): ...
- 渐进式遗传组卷算法(大规模题库,实际可用的算法) 智能组卷系统
基本遗传算法的缺陷分析:设一套题共需5种题型,共20道题目.设每道题在题库中有100道侯选题目.那么总共的组卷空间大小大约是10020 ,假设遗传算法的种群大小为1000,叠代1000次,那么最多搜索 ...
- oracle上机题库_ORACLE OCM 最新考试题库
Oracle OCM 最新题库,100%保证质量,OCM 大师亲自为您辅导,练习中有任何问题,有OCM 大师为您答疑解惑,传授考场经验,助您一次成功. 课程介绍 1.Oracle Certified ...
- 全国二级c语言上机题库答案,二级C语言上机题库100题加答案
<二级C语言上机题库100题加答案>由会员分享,可在线阅读,更多相关<二级C语言上机题库100题加答案(67页珍藏版)>请在人人文库网上搜索. 1.1 :将大于整数m且接近m的 ...
- CCNA精品学习资料汇总(学习手册+笔记+题库)
CCNA精品学习资料汇总(学习手册+笔记+题库) CCNA认证标志着具备安装.配置.运行中型路由和交换网络,并进行故障排除的能力.获得CCNA认证的专业人士拥有相应的知识和技能,能够通过广域网与 ...
- 二级c语言基础题库100题,二级C语言上题库100题.doc
二级C语言上题库100题 二级C语言上机试题汇编 第01套: 给定程序中,函数fun的功能是:将形参n所指变量中,各位上为偶数的数去 除,剩余的数按原来从高位到低位的顺序组成一个新的数,并通过形参指针 ...
- 行测题库:行测每日一练常识判断练习题02.04
行测题库:行测每日一练常识判断练习题02.04 1.下列说法错误的是: A.CPI反映居民所购生活消费品的价值和服务项目价格变动趋势 B.通货膨胀的实质是社会总需求小于社会总供给 C.经济学领域中最初 ...
- CISCO CCNA CCNP CCIE认证题库下载
CISCO CCNA CCNP CCIE认证题库下载 350-024 CCIE SP IP Telephony Qualification Exam 350-026 CCIE SP Content N ...
- CCNA题库关于Frame-relay看图答题的解答
先上原文,后面解释! (In the old days, this question was a multi-choice question but Cisco upgraded it into a ...
最新文章
- HP-UX Root密码被锁定的非关机情况下解决方案
- vim-go开发环境Tagbar插件和NERTree插件安装
- Linux系统之创建逻辑卷
- 运筹学的课程笔记 markov decision process
- .net随笔-vb.net 系统计时器
- Spring5的Web 组件
- 工业交换机的端口号结构特征
- git啊,你让我好费劲啊
- DDD分层架构的三种模式
- 【鱼眼镜头8】张正友畸变公式;鱼眼的畸变公式需要使用入射角
- ubuntu14.04 Nvidia 驱动和cuda安装(转)
- 凸优化第五章对偶 5.7例子
- jdbc查mysql_mysql的查询及连接JDBC数据库
- 51单片机-宏晶STC与硬仿真
- Python入门50个小程序
- 学习W5500的OTA平台的SDK
- rsync同步脚本示例,带有exclude参数说明
- 【操作系统】第3章 内存管理
- 苹果被曝重大系统漏洞:新款MacBook、iPhone 12统统波及,root权限秒被获取
- MT管理器解锁某APP部分功能
