dsa数字签名算法_密码学中的数字签名算法(DSA)
dsa数字签名算法
Digital Signature Algorithm (DSA) is one of the Federal Information Processing Standard for making digital signatures depends on the mathematical concept or we can say the formulas of modular exponentiation and the discrete logarithm problem to cryptograph the signature digitally in this algorithm.
数字签名算法(DSA)是使数字签名依赖于数学概念的联邦信息处理标准之一,或者我们可以说模幂运算的公式和离散对数问题,用于在该算法中对数字进行数字加密。
It is Digital signatures are the public-key primitives of message authentication in cryptography. In fact, in the physical world, it is common to use handwritten signatures on handwritten or typed messages at this time. Mainly, they are used to bind signatory to the message to secure the message.
数字签名是加密中消息身份验证的公钥原语。 实际上,在物理世界中,此时通常在手写或键入的消息上使用手写签名。 主要是,它们用于将签名者绑定到消息以保护消息。
Therefore, a digital signature is a technique that binds a person or entity to the digital data of the signature. Now, this will binding can be independently verified by the receiver as well as any third party to access that data.
因此,数字签名是一种将人或实体绑定到签名的数字数据的技术。 现在,此绑定将可以由接收者以及访问该数据的任何第三方独立验证。
Here, Digital signature is a cryptographic value that is calculated from the data and a secret key known only by the signer or the person whose signature is that.
在此, 数字签名是根据数据和仅由签名者或签名者知道的秘密密钥计算出的密码值。
In fact, in the real world, the receiver of message needs assurance that the message belongs to the sender and he should not be able to hack the origination of that message for misuse or anything. Their requirement is very crucial in business applications or any other things since the likelihood of a dispute over exchanged data is very high to secure that data.
实际上,在现实世界中,消息的接收者需要确保该消息属于发送者,并且他不应因滥用或其他任何原因而破解该消息的来源。 他们的要求在业务应用程序或其他任何事情中都至关重要,因为对交换数据进行争执的可能性很高,以确保数据的安全。
数字签名框图 (Block Diagram of Digital Signature)
The digital signature scheme depends on public-key cryptography in this algorithm.
在此算法中,数字签名方案取决于公钥加密。
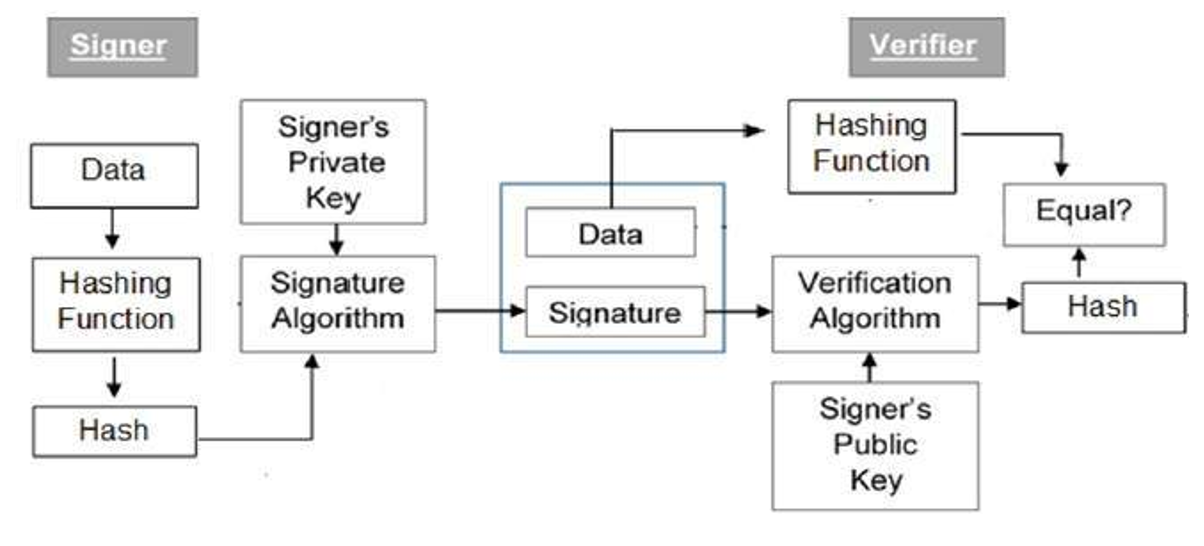
框图说明 (Explanation of the block diagram)
Firstly, each person adopting this scheme has a public-private key pair in cryptography.
首先,采用此方案的每个人在密码学上都有一个公私钥对。
The key pairs used for encryption or decryption and signing or verifying are different for every signature. Here, the private key used for signing is referred to as the signature key and the public key as the verification key in this algorithm.
每个签名用于加密或解密以及签名或验证的密钥对都不相同。 在此算法中,用于签名的私钥称为签名密钥,公钥称为验证密钥。
Then, people take the signer feeds data to the hash function and generates a hash of data of that message.
然后,人们将签名者的提要数据输入哈希函数,并生成该消息的数据哈希。
Now, the Hash value and signature key are then fed to the signature algorithm which produces the digital signature on a given hash of that message. This signature is appended to the data and then both are sent to the verifier to secure that message.
现在,哈希值和签名密钥随后被馈送到签名算法,该算法在该消息的给定哈希值上生成数字签名。 该签名被附加到数据中,然后两者都发送到验证者以保护该消息。
Then, the verifier feeds the digital signature and the verification key into the verification algorithm in this DSA. Thus, the verification algorithm gives some value as output as a ciphertext.
然后,验证者将数字签名和验证密钥输入此DSA中的验证算法。 因此,验证算法将一些值作为密文输出。
Thus, the verifier also runs the same hash function on received data to generate hash value in this algorithm.
因此,验证程序还在此算法上对接收到的数据运行相同的哈希函数,以生成哈希值。
Now, for verification, the signature, this hash value, and output of verification algorithm are compared with each variable. Based on the comparison result, the verifier decides whether the digital signature is valid for this or invalid.
现在,为了进行验证,将签名,此哈希值以及验证算法的输出与每个变量进行比较。 根据比较结果,验证者确定数字签名对此有效还是无效。
Therefore, the digital signature is generated by the 'private' key of the signer and no one else can have this key to secure the data, the signer cannot repudiate signing the data in the future to secure that data by the cryptography.
因此,数字签名是由签名者的“私钥”生成的,没有其他人可以拥有此密钥来保护数据,签名者以后将无法否认对数据的签名以通过密码保护该数据。
数字签名的重要性 (Importance of Digital Signature)
Therefore, all cryptographic analysis of the digital signature using public-key cryptography is considered a very important or main and useful tool to achieve information security in cryptography in cryptoanalysis.
因此,使用公钥密码术对数字签名进行的所有密码分析被认为是在密码分析中实现密码学信息安全性的非常重要或主要和有用的工具。
Thus, apart from the ability to provide non-repudiation of the message, the digital signature also provides message authentication and data integrity in cryptography.
因此,除了提供消息不可否认性的能力之外,数字签名还提供了加密中的消息认证和数据完整性。
This is achieved by the digital signature are,
这是通过数字签名实现的,
Message authentication: Therefore, when the verifier validates the digital signature using the public key of a sender, he is assured that signature has been created only by a sender who possesses the corresponding secret private key and no one else does by this algorithm.
消息身份验证 :因此,当验证者使用发送方的公钥验证数字签名时,可以确保签名仅由拥有相应私钥的发送方创建,而该算法没有其他人创建。
Data Integrity: In fact, in this case, an attacker has access to the data and modifies it, the digital signature verification at the receiver end fails in this algorithm, Thus, the hash of modified data and the output provided by the verification algorithm will not match the signature by this algorithm. Now, the receiver can safely deny the message assuming that data integrity has been breached for this algorithm.
数据完整性 :实际上,在这种情况下,攻击者可以访问数据并对其进行修改,该算法在接收方端的数字签名验证失败,因此,修改后的数据的哈希值和验证算法提供的输出将与该算法的签名不匹配。 现在,假设此算法已破坏数据完整性,则接收方可以安全地拒绝该消息。
Non-repudiation: Hence, it is just a number that only the signer knows the signature key, he can only create a unique signature on a given data of that message to change in cryptography. Thus, the receiver can present data and the digital signature to a third party as evidence if any dispute arises in the future to secure the data.
不可否认性 :因此,只有签名者才知道签名密钥的数字,他只能在该消息的给定数据上创建唯一签名以更改密码。 因此,如果将来发生任何争议以保护数据,则接收方可以将数据和数字签名提供给第三方作为证据。
带有数字签名的加密 (Encryption with Digital Signature)
It is desirable to exchange encrypted messages than plaintext to achieve confidentiality in cryptography. In fact, in the public key encryption scheme, this is a public or encryption key of the sender is available in the open domain, and hence anyone can spoof his identity and send an encrypted message to the receiver in this algorithm.
期望交换加密消息而不是明文以实现加密的机密性。 实际上,在公共密钥加密方案中,这是发件人的公共或加密密钥在开放域中可用,因此任何人都可以通过此算法欺骗其身份并将加密的消息发送给接收者。
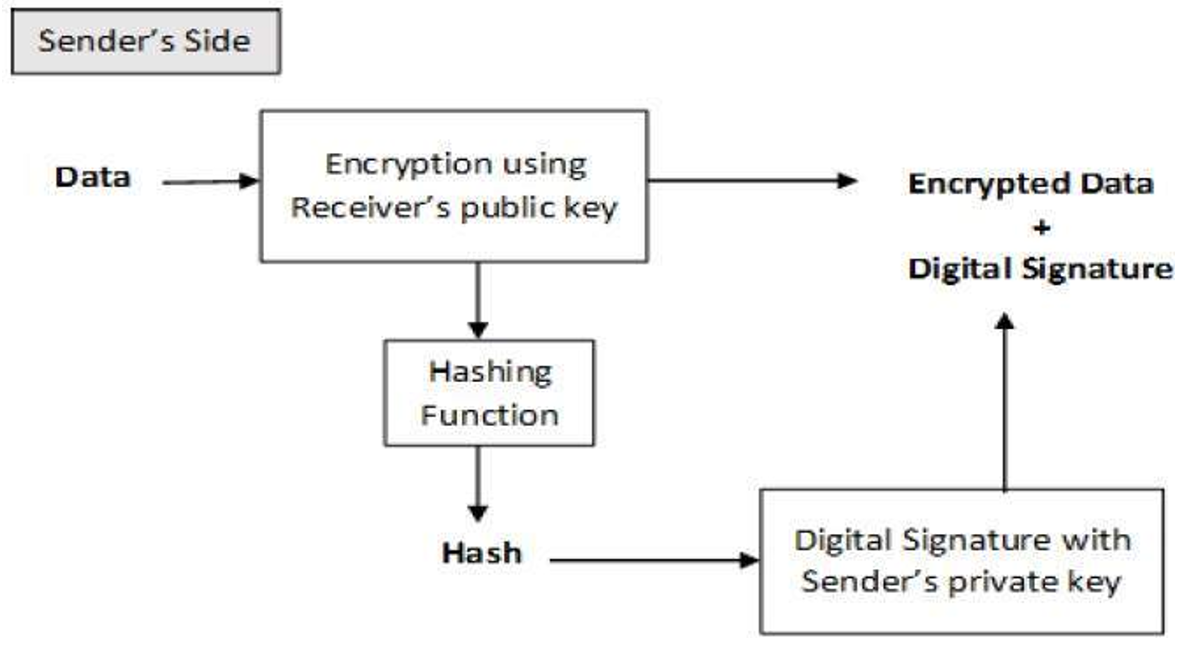
DSA算法步骤 (DSA Algorithm Steps)
The first part of the DSA algorithm is the public key and private key generation through some steps, which can be told as:
DSA算法的第一部分是通过一些步骤生成公钥和私钥,可以将其描述为:
Firstly, choose a prime number q, which is called the prime divisor in this.
首先,选择质数q,在此称为质数除数。
Then, choose another primer number p, such that p-1 mod q = 0. p is called the prime modulus in this.
然后,选择另一个引物编号p,以使p-1 mod q =0。在此将p称为质数模数。
Then, choose an integer g, such that 1 < g < p, g**q mod p = 1 and g = h**((p–1)/q) mod p. q is also called g's multiplicative order modulo p in this algorithm.
然后,选择一个整数g,使得1 <g <p,g ** q mod p = 1且g = h **((p-1)/ q)mod p。 q在此算法中也称为g的乘数模p。
Then, choose an integer, such that 0 < x < q for this.
然后,选择一个整数,例如0 <x <q。
Now, compute y as g**x mod p.
现在,将y计算为g ** x mod p。
Thus, Package the public key as {p,q,g,y} is this.
因此,将公钥打包为{p,q,g,y}就是这个。
And, Package the private key as {p,q,g,x} is this.
并且,将私钥打包为{p,q,g,x}就是这个。
Then, the second part of the DSA algorithm is the signature generation and signature verification in this algorithm, which can be told as:
然后,DSA算法的第二部分是该算法中的签名生成和签名验证,可以这样说:
Firstly, to generate a message signature, the sender can follow these further steps:
首先,要生成消息签名,发送者可以按照以下进一步步骤操作:
Firstly, generate the message digest h, using a hash algorithm like SHA1.
首先,使用类似于SHA1的哈希算法生成消息摘要h。
Then, generate a random number k, such that 0 < k < q.
然后,生成一个随机数k,使得0 <k <q。
Then, Computer as (g**k mod p) mod q. If r = 0, select a different k.
然后,将计算机作为(g ** k mod p)mod q。 如果r = 0,则选择另一个k。
And, Compute i, such that k*i mod q = 1. i is called the modular multiplicative inverse of k modulo q in this.
并且,计算i,使得k * i mod q =1。在此,i被称为k模q的模乘逆。
Then, Compute s = i*(h+r*x) mod q. If s = 0, select a different k.
然后,计算s = i *(h + r * x)mod q。 如果s = 0,则选择另一个k。
Thus, Package the digital signature as {r,s}.
因此,将数字签名打包为{r,s}。
Then, to verify a message signature, the receiver of the message and the digital signature can follow these further steps as:
然后,为了验证消息签名,消息的接收者和数字签名可以按照以下其他步骤操作:
Firstly, Generate the message digest h, using the same hash algorithm.
首先,使用相同的哈希算法生成消息摘要h。
Then, Compute w, such that s*w mod q = 1. w is called the modular multiplicative inverse of s modulo q in this.
然后,计算w,使得s * w mod q =1。w在此称为s模q的模乘逆。
Then, Compute u1 = h*w mod q.
然后,计算u1 = h * w mod q。
And, Compute u2 = r*w mod q.
并且,计算u2 = r * w mod q。
Then, Compute v = (((g**u1)*(y**u2)) mod p) mod q.
然后,计算v =((((g ** u1)*(y ** u2))mod p)mod q。
Wherever, If v == r, the digital signature is valid.
无论何时,如果v == r,则数字签名均有效。
Image Reference: https://www.tutorialspoint.com/cryptography/cryptography_digital_signatures.htm
图片参考: https : //www.tutorialspoint.com/cryptography/cryptography_digital_signatures.htm
翻译自: https://www.includehelp.com/cryptography/digital-signature-algorithm-dsa.aspx
dsa数字签名算法
dsa数字签名算法_密码学中的数字签名算法(DSA)相关推荐
- mardown 标题带数字_标题中带有数字的故事更成功吗?
mardown 标题带数字 统计 (Statistics) I have read a few stories on Medium about writing advice, and there we ...
- md5不是对称密码算法_密码学中的消息摘要算法5(MD5)
md5不是对称密码算法 In cryptography, MD5 (Message-Digest algorithm 5) is a mainly used cryptographic hash fu ...
- des加密密码补位_密码学中的数据加密标准(DES)
des加密密码补位 This is a Data Encryption Standard that is the asymmetric key generation for the encryptio ...
- 数字练习_为什么要练习数字简约
数字练习 重点 (Top highlight) Disclaimer: This article does not contain any affliate links Back in 2018, R ...
- php把数字转化字符串,php中把数字转化为字符串的方法有哪些?-PHP问题
php中把数字转化为字符串的办法有哪些? php中把数字转化为字符串的办法: PHP的数据类型转换属于强迫转换,转换类型为(string):转换成字符串 转换形式: intval() floatval ...
- java string 字符个数字_java从字符串中提取数字
string类函数的补充说明: trim()方法返回调用字符串对象的一个副本,但是所有起始和结尾的空格都被删除了,例子如下:String s=" Hello World ".tri ...
- php 取字符串的数字,php提取字符串中的数字
近日工作中需要在一串字符串中将所有的数字提取出来这么一个小功能,研究了一下发现方法还挺多,值得记录一下,于是对如何使用PHP将字符串中的数字提取出来的功能做了一个小总结,总结三种方法如下: 第一种方法 ...
- matlab朴素贝叶斯手写数字识别_从“手写数字识别”学习分类任务
机器学习问题可以分为回归问题和分类问题,回归问题已经在线性回归讲过,本文学习分类问题.分类问题跟回归问题有明显的区别,回归问题是连续的数值,而分类问题是离散的类别,比如将性别分为[男,女],将图片分为 ...
- php提取字符串中数字,php提取字符串中的数字教程
字符串是我们程序员必定接触法人,有时候工作中需要在一串字符串中将所有的数字提取出来,其实研究一下这种方法还挺多,对如何使用PHP将字符串中的数字提取出来的功能我们做了一个小总结,和大家一起分享一下,总 ...
最新文章
- [WebDev]Web 开发与设计师速查手册大全
- Java 程序员都该懂的 HashMap
- C#中的参数传递(转)
- 如何让滚动条出现在左边
- 关于xml的模糊查询问题
- 到底什么是跨域?附解决方案!
- SpringBoot 中常用注解@PathVaribale/@RequestParam/@GetMapping介绍
- Java反射技术概述
- python效率低为什么_为什么 Python 这么慢?
- js 异步执行_JS异步执行机制——事件循环(Event Loop)
- C++ std:: 的坑
- Android反射机制实现与原理
- BZOJ 2734: [HNOI2012]集合选数( 状压dp )
- 多说评论如何显示最近访客
- ASP.Net中防止页面刷新重复提交的几种方法
- C# 节约里程法实现
- spring切点表达式提取jdk版本与aspectjweaver版本不匹配
- 什么是网络分析仪?它的重要技术指标有哪些?
- 360浏览器登录新浪微博图标显示为字母及占用CPU过高问题的解决
- 【flask高级】从源码深入理解flask路由之endpoint
热门文章
- 远程报:这可能是由于credssp加密oracle修正
- 结构体内容引用自非结构体数组对象axes(handles.axes1)
- Jmeter定时器之吞吐量整形定时器jp@gc Throughput Shaping Timer
- linux shell 中文输入,Linux操作系统的Shell环境中输入中文
- git Cherry-pick Failed your local changes would be overwritten by cherry-pick. hint: commit your
- 网络:tcp长连接与短连接
- 使用QGIS制作点密度专题图
- MySQL DBA的修炼与未来,看看老司机们怎么说?
- 网站安全与渗透测试工程师岗位区别
- 【配送路径规划】基于matlab蚁群算法求解配送路径最短问题【含Matlab源码 2222期】
